How to Hack An Insecure Web App: OWASP WebGoat Challenge (Part 1)
The OWASP WebGoat project is a deliberately insecure web application created for anyone eager to hack a web app and test its vulnerabilities.

What is OWASP WebGoat?
The OWASP WebGoat project is a deliberately insecure web application
created for anyone like you as well as InfoSec professionals, security researchers, and appsec developers alike who are interested and eager to hack a web app and test its vulnerabilities, especially those commonly found in Java-based applications. The purpose of OWASP WebGoat is to provide you an interactive teaching environment, so you can learn about web application security.
Web application security is extremely important in our modern age when using web apps is a part of our daily lives. A web app is an app that’s accessed through a web browser. To name a few, it can be your favorite online store, bank, email, cryptocurrency exchange, or social media app. It is common knowledge that a never-ending amount of web apps exist across the worldwide web.
Additionally, the likelihood of a web app becoming hacked by malicious actors at some point in time is very high (whether successfully or not), and unfortunately happens on a large scale frequently. When people like you and I are more likely to use a web app such as Amazon to purchase goods and services as opposed to a brick and mortar (especially during the pandemic), it means that web application security is absolutely indispensable, and cannot be overlooked when our financial data is often involved for the purchases we make over the web.
Learning how to secure a web application has never been more important than now!
As a result, I will be giving you a walkthrough of the OWASP WebGoat Challenge (there will be 3 parts) to demonstrate a few ways of how web apps can get hacked! You are welcome to join me and follow along. But before we begin, I must remind you to take heed of the following warnings because hacking web apps is NOT a joke. However, it can be really fun! 😉

⚠️⚠️ Web App Hacking Disclaimer ⚠️⚠️
Before I give you a walkthrough on how to hack an insecure web app with the WebGoat Challenge, I must remind you to take heed of the following warnings!
⚠️ 1. DO NOT try these techniques on any web app or website WITHOUT written legal permission! Failure to do so may result in expensive legal headaches or jailtime which you are better off without. Unauthorized hacking, even if it is with good intent, can bite you in the ass so do not bother to take a chance. ONLY practice hacking on web apps that are deliberately insecure for learning purposes, or those that participate in a Bug Bounty reward program which you can volunteer for (and hopefully get paid too).
⚠️ 2. AVOID running an insecure web app such as WebGoat on your local machine! Disconnect from the internet while using it if you insist. Just remember you WILL be vulnerable to attack! Someone out there in the world will be so excited and happily eager to hack into your exposed local machine and cause damage. It is HIGHLY RECOMMENDED that you use a virtual machine removed from your local network when doing this WebGoat challenge.
Now that I've got these friendly reminders out of the way, let's begin hacker. 🙃
Getting Started
For the OWASP WebGoat Challenge, I had two virtual machines (VMs) set up that were created in an Azure Cloud lab environment. The first VM is my "attacker" machine named Kali which is running Kali Linux. The second VM is my "target" machine named OWASP BWA which hosts OWASP Broken Web Applications (BWA) including WebGoat for the WebGoat challenge!
Both VMs were started up on the Hyper-V Manager that I accessed from my local machine through the Microsoft Remote Desktop (RDP) app as seen in the following screenshots below. If you would like to set up an OWASP BWA VM environment, you can do so from: https://github.com/chuckfw/owaspbwa
👨🏻💻 Let's begin hacking the WebGoat!

Log into your attacker machine (Kali Linux)
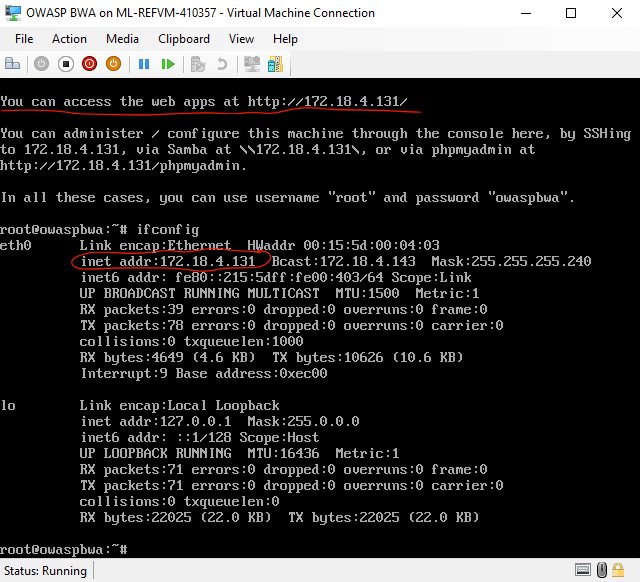
After verifying the IPv4 address of your OWASP BWA target VM (172.18.4.131 in my case) which hosts a variety of OWASP Broken Web Applications including OWASP WebGoat which we will be focusing on for the WebGoat challenge, log into your attacker machine (Kali) and load up your web browser.
Load the OWASP BWA landing page
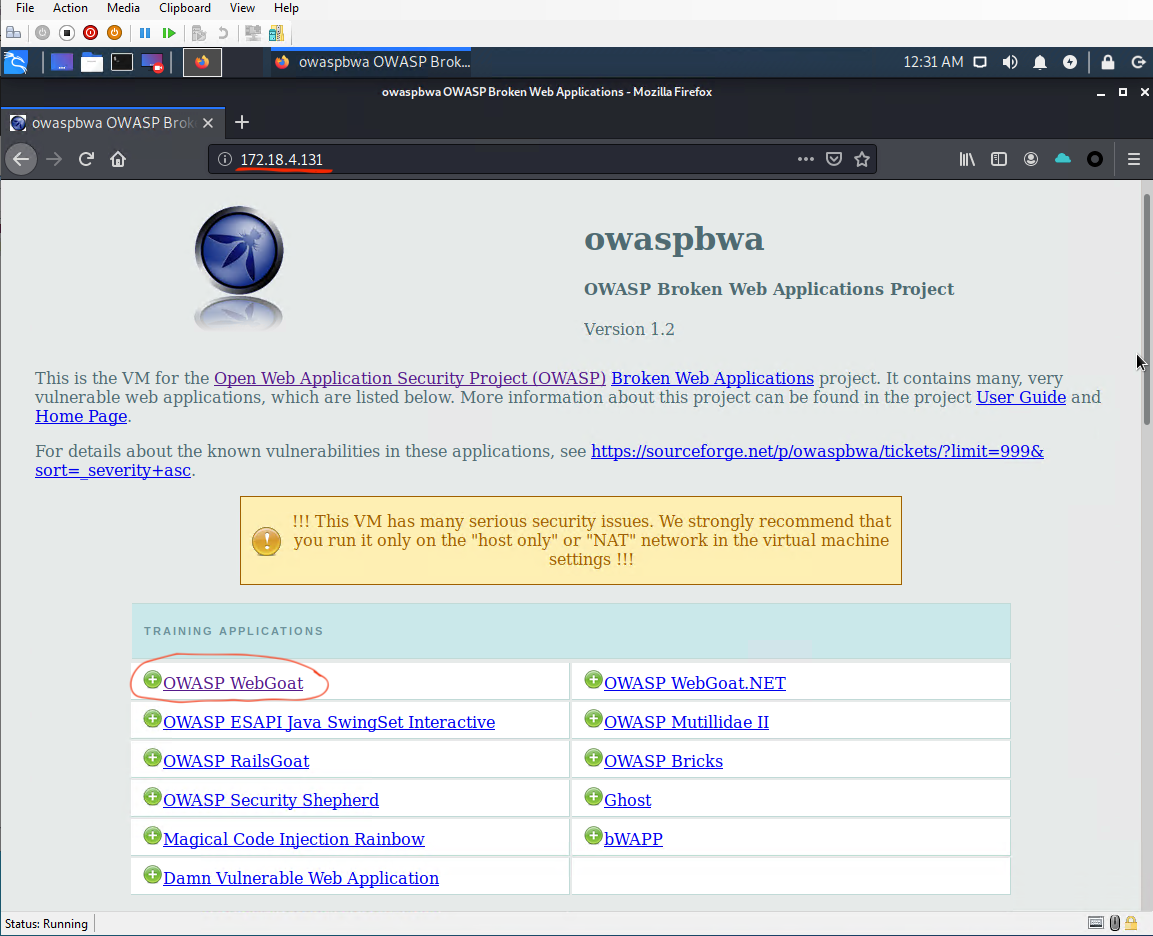
Next, type in the IP address of the OWASP BWA target VM in the URL address bar as seen below. In my case, it is http://172.18.4.131 (yours may be different). After the OWASP BWA landing page successfully loads, click on the "OWASP WebGoat" link which is the first training application listed as seen below.
Authentication Required prompt
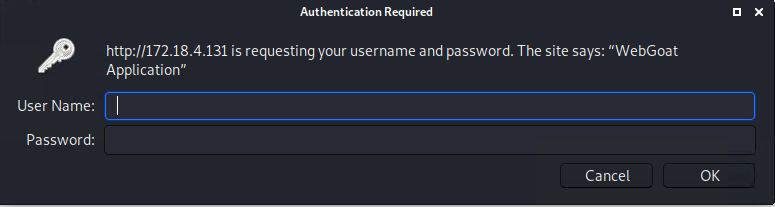
After clicking on the OWASP WebGoat link, an authentication prompt will pop-up on the web page asking for your username and password to access the WebGoat application. Since we don't know what they are, we have to figure them out!
View Page Source to find credentials
There are several ways to accomplish this task including brute force attack methods, but let's try something simple first such as right-clicking on the main page and selecting "View Page Source" in order to view its source code and inspect it for any clues. Let's do that and take a look at the page source code below!
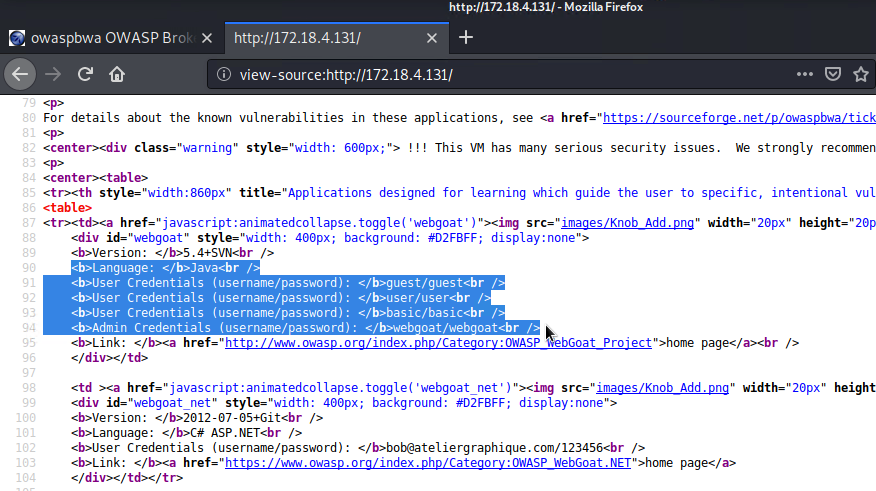
Aha! I think I found some clues! After inspecting the code, I came across "User Credentials" which appears to list the username and password of a few users including the admin. I decided to give it a shot and try logging into the WebGoat page again on the Authentication Required prompt with admin credentials (username: webgoat and password: webgoat). Let's see if they work!
Successful login with admin credentials
Bingo! I was able to successfully log in using the credentials found and was directed to the WebGoat website link http://172.18.4.131/WebGoat/attack.
Now it's time to click on "Challenge" on the left-hand side menu of the page which is last on the list and then select "The CHALLENGE" dropdown menu to officially begin hacking with our WebGoat Challenge!
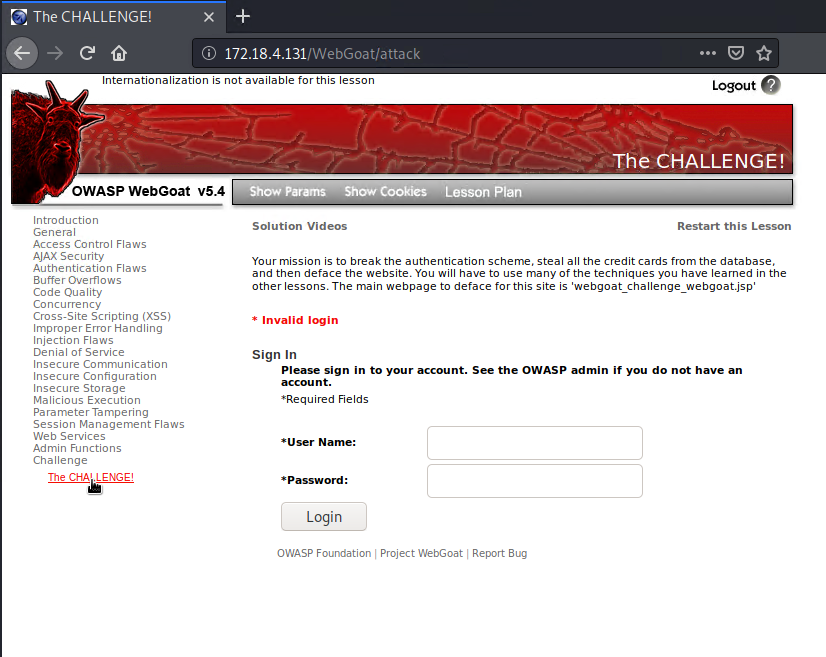
Congratulations! You successfully completed your warm-up! Now it's time to officially begin the WebGoat Challenge! 😉

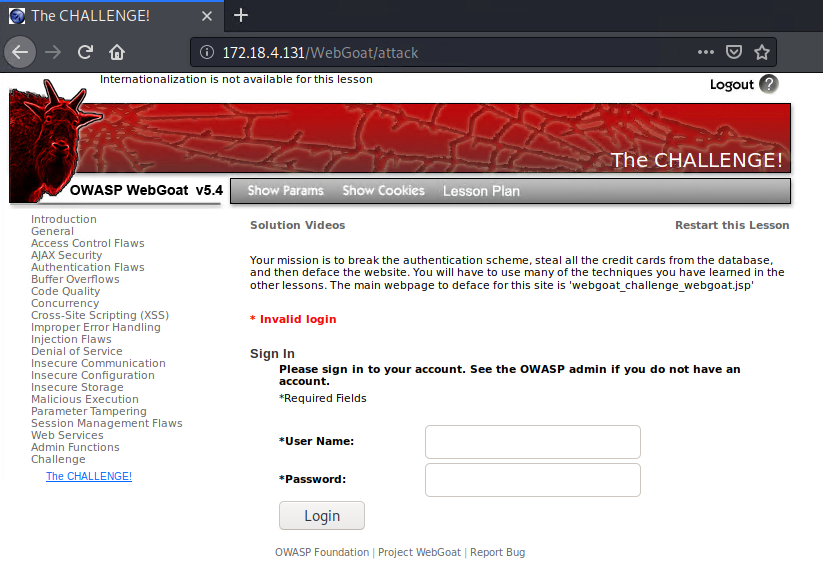
👉 Challenge #1: Break the authentication scheme
Back to square one! We need to figure out the username and password to log into the WebGoat sign-in page at http://172.18.4.131/WebGoat/attack. Let's begin with simple tactics such as right-clicking on the web page and selecting "View Page Source."
After right-clicking on the web page and viewing its source code, I inspected the source code and did not find anything that may lead me to user login credentials. 🙁 Below is a screenshot of the source code I had inspected.
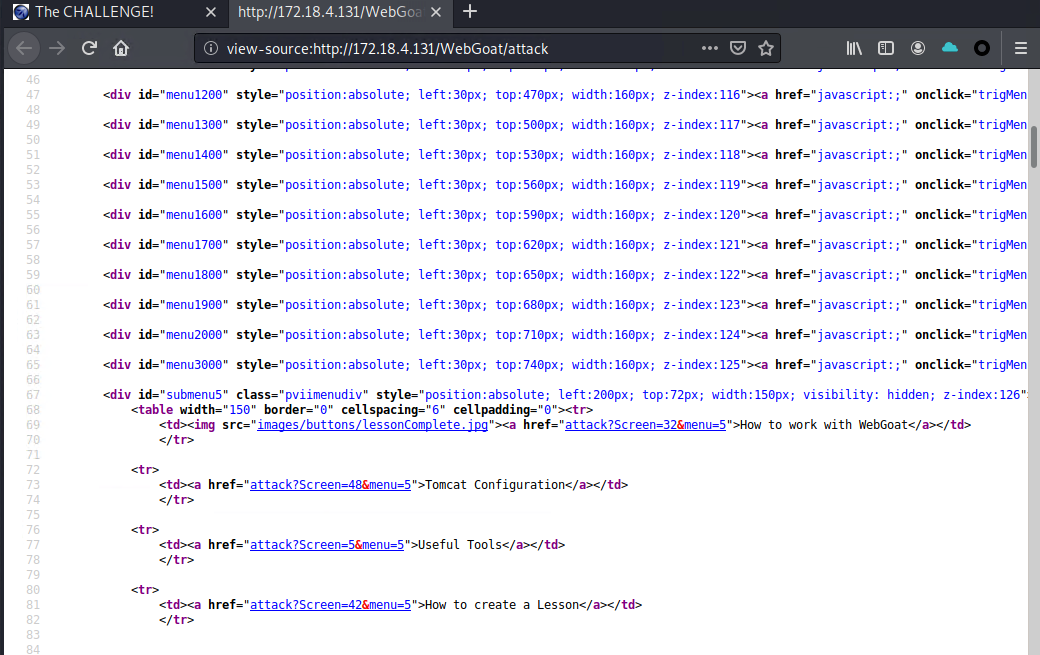
Boring right? Well, I recognized that this sign-in web page uses JavaScript code and took a wild guess that there may be a hidden JavaScript source code somewhere around. So let's try another method! Let's see if we can find out more by tampering with the web page link by passing the following URL parameter seen below to the end of the URL http://172.18.4.131/WebGoat/
source?source=true
The result looks like this.
http://172.18.4.131/WebGoat/source?source=true
After passing the URL parameter to the destination URL, I was able to successfully view the JavaScript source code directly from the destination URL, and I discovered interesting username & password credentials.
username: youaretheweakestlink
password: goodbye
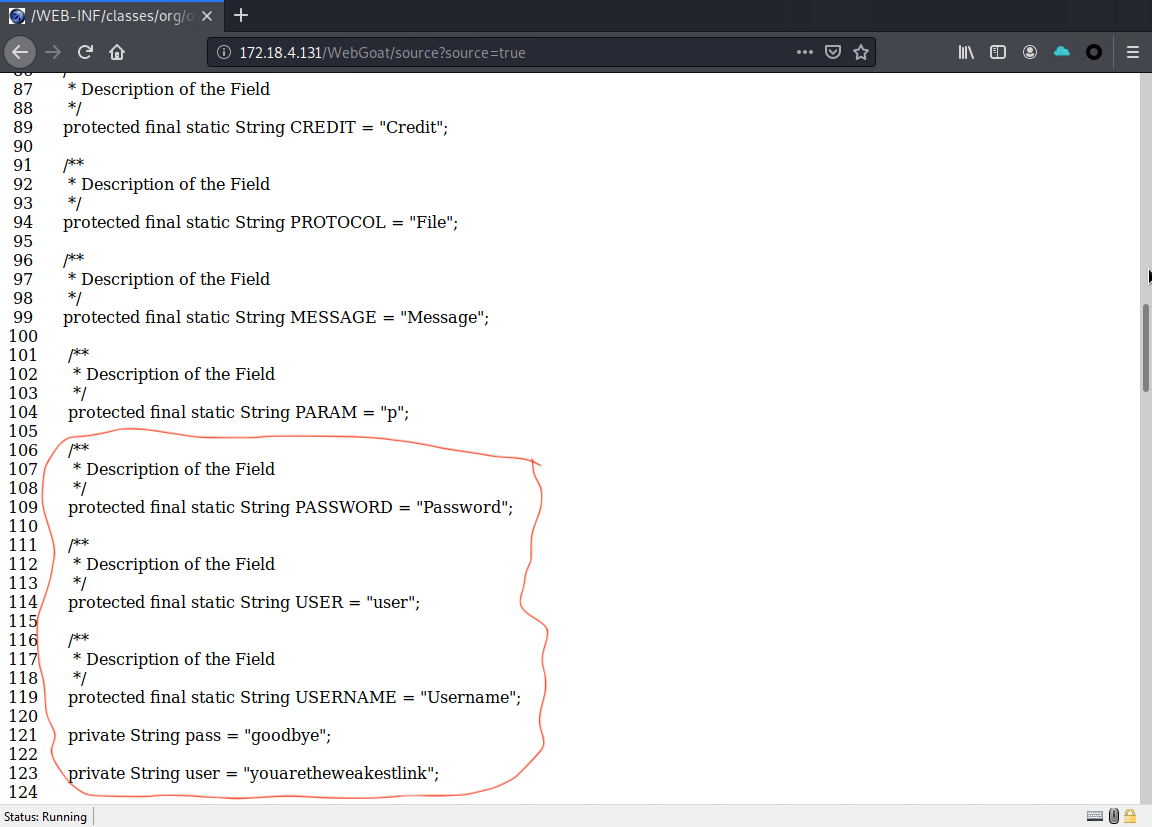
Let's try logging in with the username and password we found now!
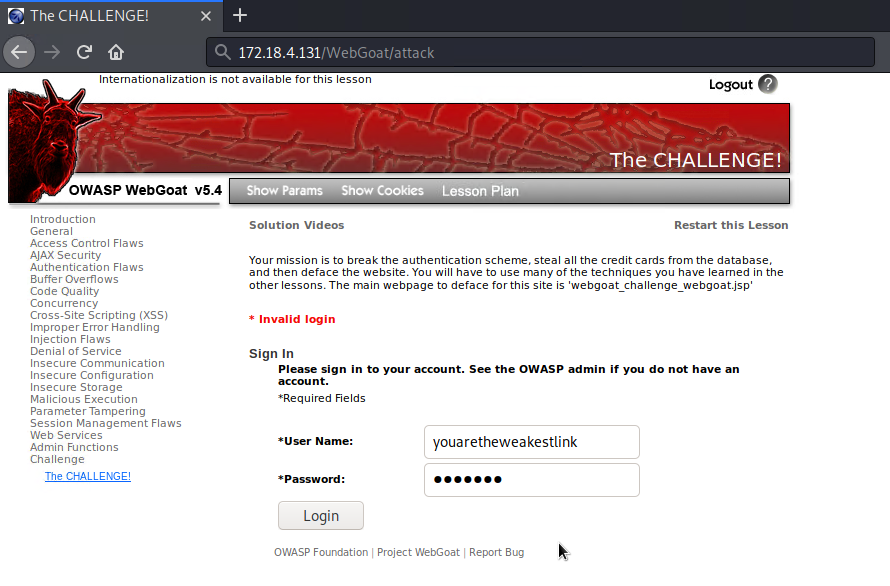
Success! We broke into the authentication login once again!
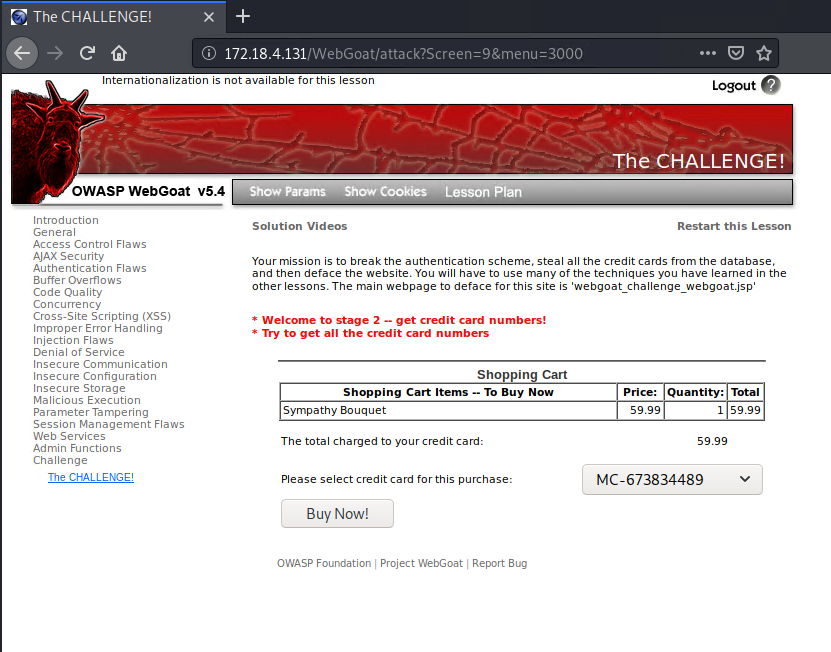
You officially completed WebGoat Challenge #1! Great job, hacker! 👏
In the next series of the WebGoat Challenge walkthrough, I will demonstrate how you can steal credit cards from a database. In the final demo of the three-part WebGoat challenge series will teach you how to deface a website. But remember kiddos, DO NOT (I repeat DO NOT) do any of this on a web app or website without written legal permission lest you choose to deal with court battles or jailtime.
Stay tuned for more! Happy hacking folks! 🍻

