Windows 10 as a pentest OS
Well, you might be surprised, especially if you're a die-hard GNU/Linux user like me, that you can actually use Windows 10 as a penetration testing operating system!

Well, you might be surprised, especially if you're a die-hard GNU/Linux user like me, that you can actually use Windows 10 as a penetration testing operating system!
Disclaimer: This is not an exhaustive review of Windows 10 for its offensive security qualities, I'm not a Windows power user and that's precisely why I think documenting the shift from GNU/Linux to Windows from my point of view might be interesting. Enjoy!
Why?
A few weeks ago, during a training session with clients, I mechanically ran sudo apt-get update && sudo apt-get upgrade in my terminal (famous last words).
Just a few minutes later, my Ubuntu machine crashed and was basically dead. My machine wouldn't find my filesystem or start a service, and I couldn't even mount my encrypted partition from what was left of my late OS.
Just in case you're in the exact same situation, use this tutorial: do not run apt-get upgrade or dist-upgrade - https://www.fosslinux.com/19213/how-to-install-metasploit-on-ubuntu.htm with both Kali and Ubuntu's repos in your sources.list file.
Thankfully, I had Windows installed on the same machine and a copy of my slides for the rest of the training. I also had a few GNU/Linux virtual machines that we could work from, the rest of the session went fine.
I went back home, and a few days after this incident, I had to start a pentest for a client. I actually didn't find the time to backup my broken OS and reinstall a fresh Ubuntu. That's how I ended up working from the pre-engagement to the report phases on Windows 10, thanks to a mix of curiosity and (let's be honest) laziness.
My usual Pentest setup
I usually work with 3 machines during a security assessment:
- My GNU/Linux (usually Ubuntu or ArchLinux) XPS 13 laptop
- Another local physical Ubuntu server with a GTX 1080 ti (mostly for cracking tasks)
- A remote Kali-Linux VPS
My favorite communication scheme definitely is SSH. I use it with X11 forwarding to use remote GUIs and CLIs.
It's fast, reasonably secure and allows me to easily tunnel ports and copy files without using or installing any other piece of software.
The main tools I work with
I mostly exploit UNIX-like, Web and mobile infrastructures. Here is my list of essential tools selected for this assessment:
- BurpSuite (among the most famous HTTP proxies, an invaluable toolkit for web exploitation)
- Metasploit (the most famous exploitation framework, courtesy of H.D Moore)
- Sublist3r/amass (two great subdomain enumeration tools)
- dirb (my favorite HTTP enumeration tool)
- Nmap (the best ports/hosts/services/vulnerability scanner)
- python/bash (most of my homemade and external tools are Python or bash based)
- testssl.sh (gives plenty of information about the way the certificates and SSL/TLS are configured on a server)
- whois/traceroute/ping/dig (Various network administration and debugging tools, usually available on most UNIX-like systems)
- Visual Studio Code (My to go code editor, has an open source version running on Windows, MacOS, and GNU/Linux and is very user-friendly)
My Windows pentest environment
Quick catch up about my Windows background: I usually only use Windows at home on my gaming machine (even though most of my games can be played on GNU/Linux thanks to Valve's work on Proton) and virtual machines to test Microsoft's specific exploits and services.
This being said, I'm familiar with most of Windows 10's basic features and used WSL and PowerShell in the past.
Without further ado, let me introduce you to my setup:
Basic setup
First of all, I needed to install a few components to run most of my GNU/Linux software.
I started by installing Windows Subsystem for Linux 2, which is the product of a long and surprising collaboration between Microsoft and Canonical, allowing users to run Ubuntu, Kali and other distributions as Windows 10 apps.
Great news if you tried WSL in the past: WSL2 does not break Hyper-V anymore and is now compatible with Docker on Windows!
Last but not least, I installed the Kali Linux Windows 10 app. I usually use Ubuntu or ArchLinux as a main work OS but Kali went through many useful changes recently and I felt like trying it!
Pre-Engagement phase
My pre-engagement phase consists of gathering information from my client to plan what will be tested, when and how. Once I have all of the information I need everything is compiled in 3 documents, including the first draft of my report.
I dislike unnecessarily complex things. I do not use LibreOffice or Microsoft Office to edit my documents. Instead I use my reports in Markdown and using pandoc with a LateX template to build a final pdf file.
The reports and various other files (notes, exploits and scan outputs, for instance) related to the pentest are also stored in password-encrypted 7zip archives.
Pandoc and 7zip can both be painlessly installed on Kali with its package manager:
apt-get install p7zip pandoc
Once my preliminary documentation was done, I could start with the first technical part: the scan phase!
Scan and Enumeration phase
I use a diverse and evolving collection of networks, services and vulnerability scanners and enumeration tools. Let's see how my favorite ones performed on this infrastructure:
Nmap
Let's be honest: Nmap does not work great on WSL, which is absolutely understandable, low level TCP and UDP socket manipulation have always been messy on Windows. Add a weird (and amazing) UNIX-like/Windows socket compatibility layer and it's nothing short of a technological miracle for Nmap to even run on this environment.
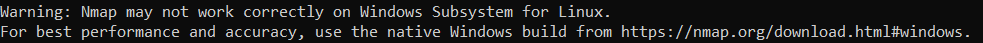
But as Nmap itself advises when you run its binary: it's preferable to run the native Windows nmap.exe instead of the GNU/Linux version. After a quick alias (yes, I could also have simlinked nmap.exe to /usr/bin/nmap) Nmap was fixed and worked great!
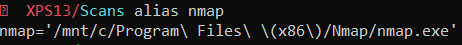
Sublist3r
With python, python-pip and virtualenv installed, Sublist3r ran smoothly. Most of my other python-based scanners (including httpx, dirhunt, sqlmap) operated without any major issue.
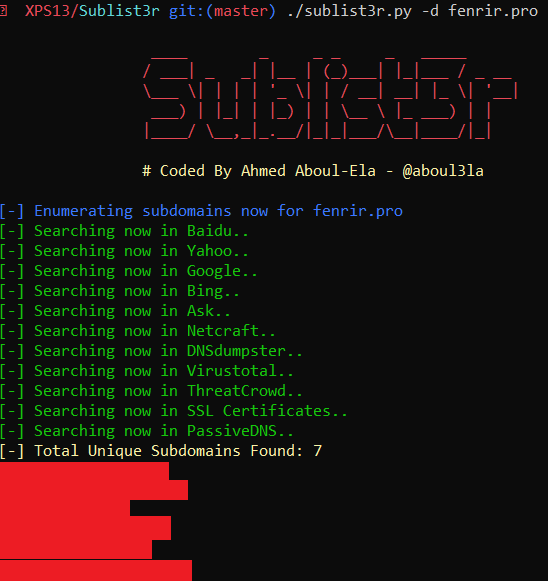
Dirb
Dirb is available in Kali's official repository. After a quick install (apt-get install dirb) it worked perfectly. 10/10 would install again!
testssl.sh
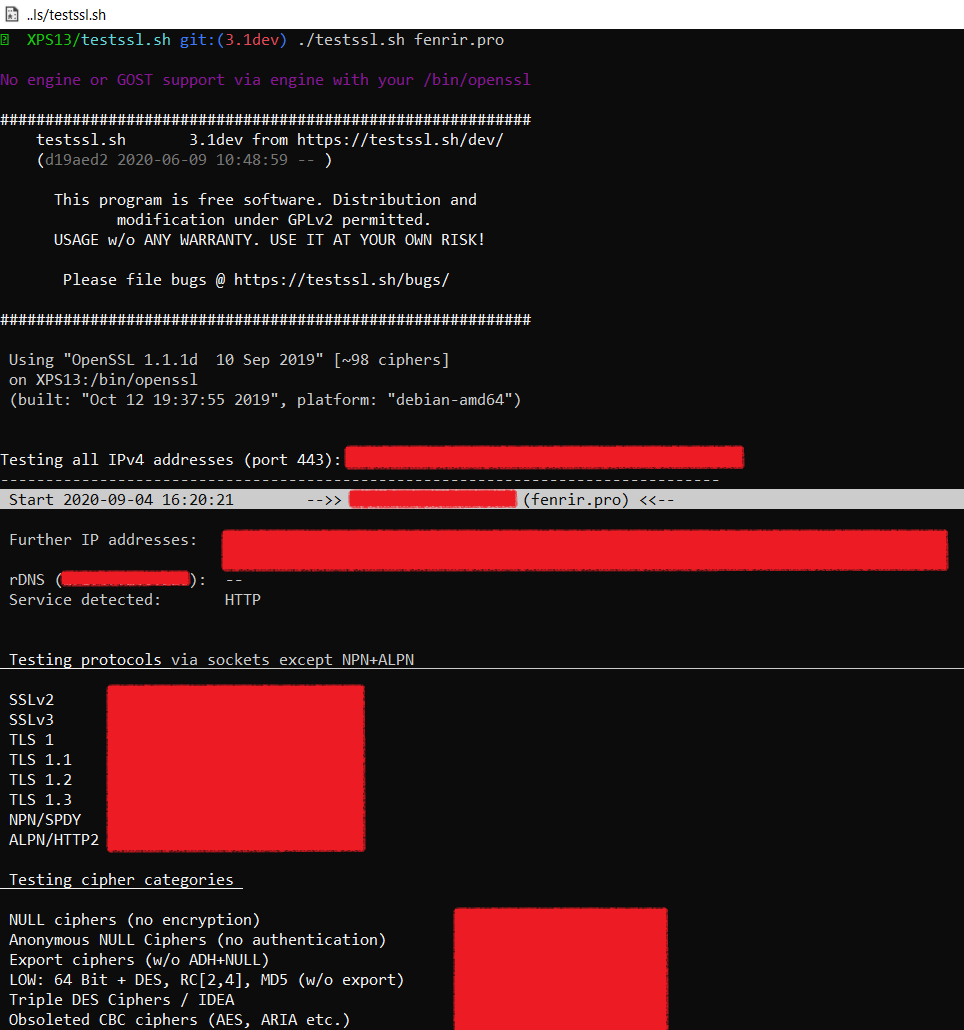
Testssl.sh is a comprehensive and versatile SSL/TLS scanner, I wasn't actually very optimistic its WSL compatibility but it worked perfectly for what I needed it for on my Kali Linux!
You might notice in the screenshot below that the GOST algorithms aren't supported by my version of OpenSSL, which might be an issue for you but weren't for my specific needs!
Exploitation
My exploitation phase relies heavily on tools (handlers, exploits, scripts and frameworks) running on my two servers and my local machine. Let's see how the SSH connections went on Windows!
SSH
OpenSSH runs on Kali and PowerShell without hassle, its syntax is the same as the GNU/Linux version, and I didn't notice any encoding compatibility issues (in particular with the carriage returns).
X11 Forwarding
X11 forwarding is also possible and surprisingly easy to setup: I first installed the VcXsrv Xserver on my Windows 10 host, and after editing the DISPLAY environment variable on Kali with export DISPLAY=localhost:0.0. I could use X11 forwarding with a classic ssh -X user@host!
I could use the i3 window manager and a few local GUI tools on VcXsrv. It worked great even though I think it is a bit slower than Xorg.
Metasploit
The Metasploit framework on Windows wasn't as accommodating as most of the other tools listed here: after I installed it with apt-get install metasploit-framework on Kali, Windows Defender almost instantly flagged and quarantined some of its files: which makes absolute sense, they're legitimate exploitation tools and exploits (you'll also probably notice the EICAR test file here)!
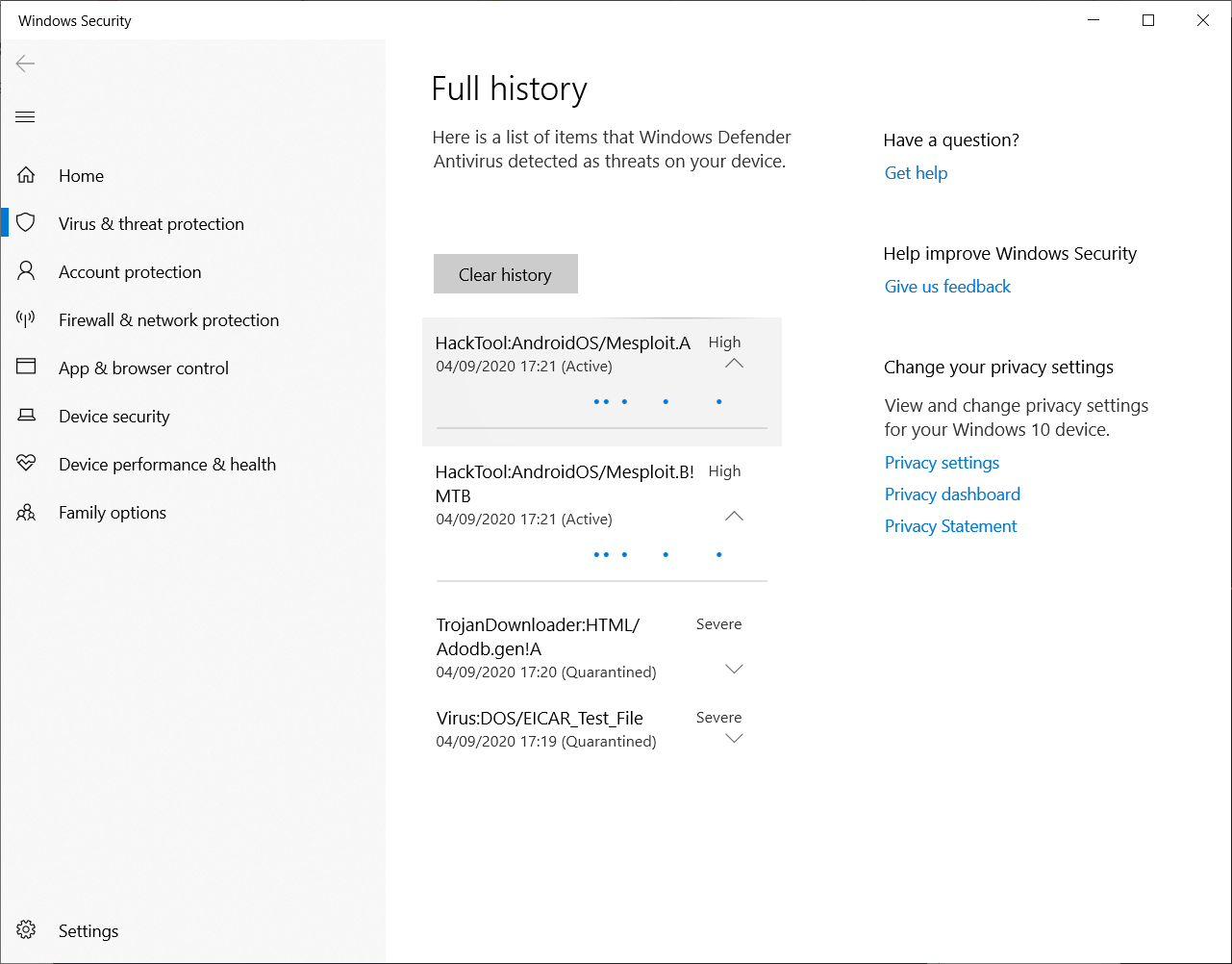
Unfortunately, without those files, Metasploit just doesn't seem to be able to run...
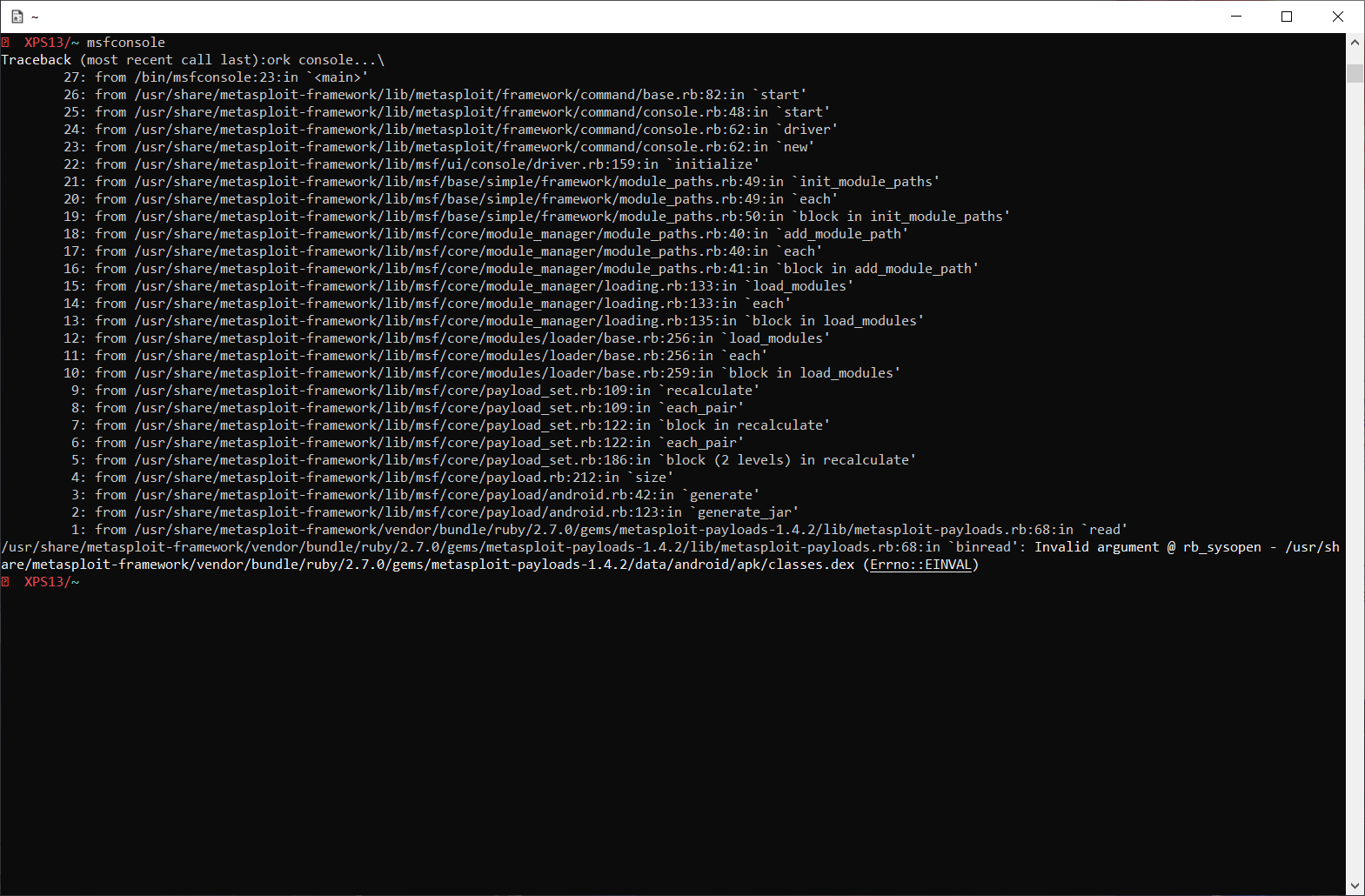
I don't want to disable Windows Defender on a machine, especially if it's on a client's internal network.
I also didn't feel like taking these files out of quarantine, it's legitimate for Defender to isolate those from my OS, and after thinking it over, I don't think having a non-isolated Metasploit installed on my local machine is absolutely necessary. The best solution for me was to install it on my VPS and use it through SSH.
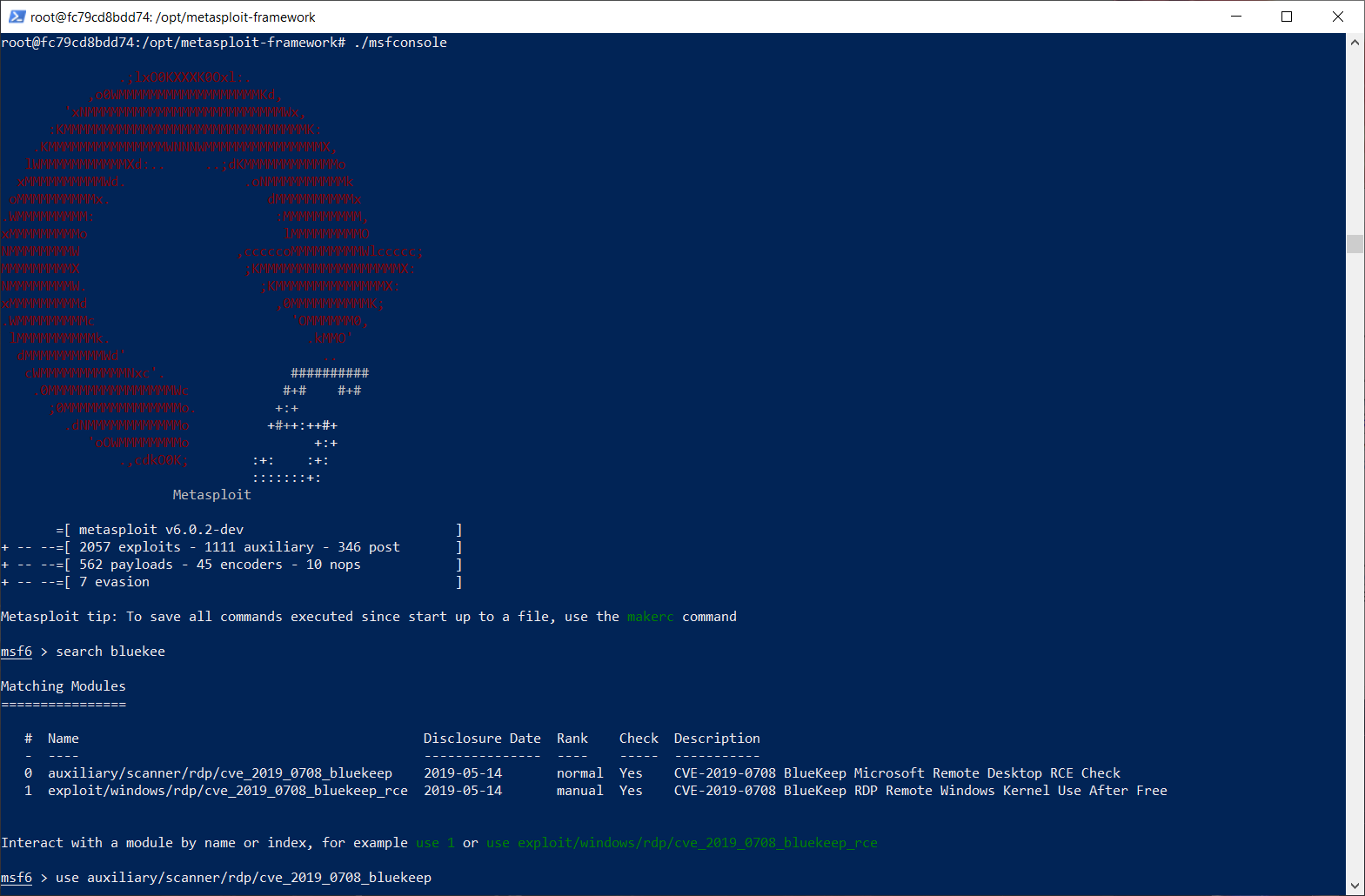
If you don't have another machine available or if you really want or need to run Metasploit on your Windows 10 host, I suggest you try phocean's docker image, all of the exploits I tried ran perfectly and Docker's containerization is, in my opinion, safer than installing the native version on your local OS.
You can try it with the following command in PowerShell:
docker run --rm -i -t --name msf phocean/msf
BurpSuite
BurpSuite has a Windows 10 version that works as well as the GNU/Linux one, it's exactly the same (literally the same .jar) and plugins are OS agnostic.
Python/Bash
Kali Linux comes preinstalled with bash like most GNU/Linux distributions and Python can be installed with apt. The scripts I used were fully compatible and even exploits containing shellcode didn't break.
Whois/Traceroute/Ping/Dig
Both whois and dig are directly available on Kali Linux, tracepath can be installed with apt-get install iputils-tracepath and also can be replaced with tracert.exe if you're familiar with it, ping is (unsurprisingly) preinstalled on Windows 10 and Kali.
In conclusion, can Windows 10 replace your distro as a Pentest OS?
[Warning: personal opinion] Even though Windows 10 has its flaws, it is, from my point of view, a very good operating system for any professional use: Windows Defender Advanced Threat Protection is very efficient (and also available on GNU/Linux) thanks to its offline and online machine-learning detection engines, Microsoft did plenty of work on their product's UX and it has a much more efficient resources usage than its predecessors.
WSL2 and Docker make Windows 10 a flexible environment, which can be a replacement for a UNIX-like OS even if you're not used to Microsoft's tools. PowerShell has undergone appreciable changes and even though it isn't as appealing to me as bash, I could work with it.
Great information security professionals I know or follow on social media use Windows, MacOS, GNU/Linux or other OSes as their daily driver. It's mostly a question of habits, needs and personal preferences.
Contrary to what I can sometimes read on vendors' blogs and in ill-informed tweets and articles, using Kali Linux, Ubuntu, Debian, BlackArch, ParrotOS, MacOS, Windows or even Android has absolutely nothing to do with one's efficiency and proficiency. Whether you're a developer, sysadmin, pentester or reverse engineer the best toolset is the one you're comfortable with.
We have reached a point where cross-compilation, virtualization and containerization allow us to basically run any piece of software on any infrastructure and piping native Windows executables to GNU/Linux specific commands made me realize how unimportant one's choice of Operating System is, especially in our times.
What next?
Most of the tools I needed worked great, but I have to admit I kind of cheated: I used plenty of GNU/Linux tools since time was a constraint. However, spending a week on Windows, was a compelling change nonetheless and I was amazed by WSL2's progress.
Even though I feel more at home on my resurrected Ubuntu, I'm definitely going to spend more time on Windows, especially since I'm trying to learn more about its internals to expand my exploitation skills and technical knowledge in general.
The next step I'd like to take would be to use the Windows 10 native equivalent of my current toolset, maybe with Commando-VM (which has been giving me the eye for a while now) as a base.
I hope you enjoyed reading my feedback on these few days with Windows 10!
If you want to discuss or stay in touch, you can follow me on Twitter @lp1eu.
Take care!

