Windows Forensics: Artifacts (1)
The first article in our series on Windows Forensics from security researcher Hartoyo Wahyu, in this episode he covers artifacts.

In forensic science we will find the word "Artifact". artifacts is an object of relic or prehistoric objects that had previously been used. Artifacts in forensic science are pieces of data that can be used as good information when digital crimes occur so that they can be used as evidence for re-analysis by the forensic team. Artifacts on a computer system can usually be in the form of log or cache activity on the application used because this object can be used to analyze events before and leading up to an incident on the system.
Because this object is a relic of user behavior, the information obtained is not necessarily a small amount or a lot. There are several methods that can be used on the object of analysis when there is a lack of information obtained or there is a lost object that needs to be recovered. In this article I will not discuss how the methods are used when analyzing artifacts, but what types of artifacts can we get on the Windows operating system in general. Here are some of the steps involved in digital forensics:
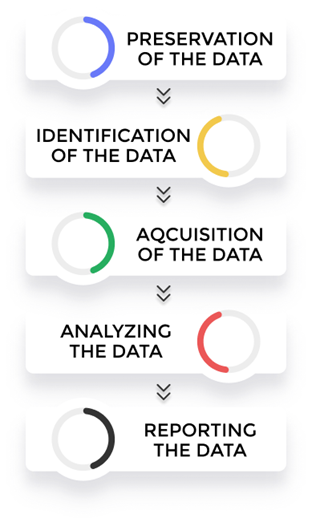
Preservation: Isolate the data, secure it, and preserve it for analysis.
Identification: Identify the purpose of the investigation and resources required
Acquisition: Receive any data relevant to the investigation from the system.
Analyze: The process of analysis is needed using certain methods with the help of tools to support the process of extracting information from the data.
Reports: Preliminary results of the analysis process need to be documented to facilitate extracting information from the data obtained.
Why Choose Windows?
The Windows operating system is easily the most popular OS on earth and one of the many operating systems used around the world, but most new computers or laptop devices use the Windows operating system. So this has an impact in the digital world, most cybercrimes are aimed at Windows so we need to know what little objects will be used as artifacts then conducting forensics on Windows systems. The following are some of the features and components that we can make as artifacts on a Windows system:
- Recycle Bin
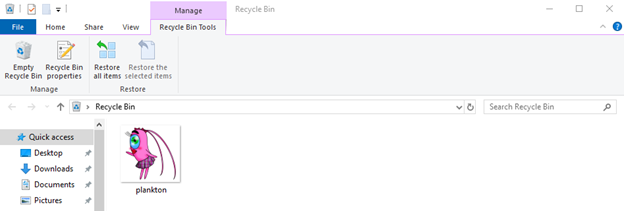
Software commonly used as a place to store data that has been deleted so that it can be recovered when an error occurs in deleting data. Files that have been deleted can be useful artifacts for further analysis. In the following example I have a photo on the desktop, then I delete the photo and the existence of the photo has moved from the desktop to the recycle bin.
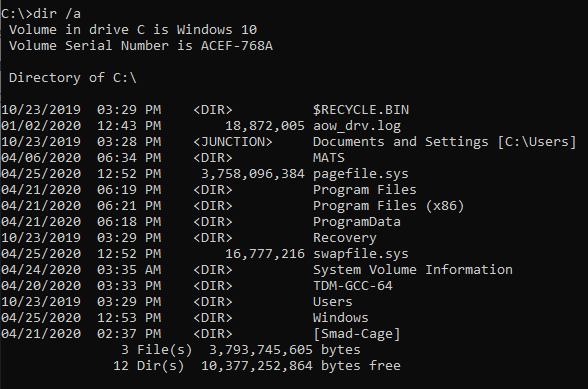
Run the command prompt as administrator and see hidden files by typing dir / a and you can see the $Recycle.Bin folder in the first line.
Moving to the recycling directory, after moving to the trash, then I want to see the contents of the trash directory.
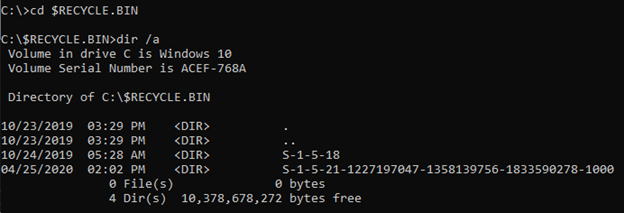
With SID we will find out which folders or files are returned by certain users
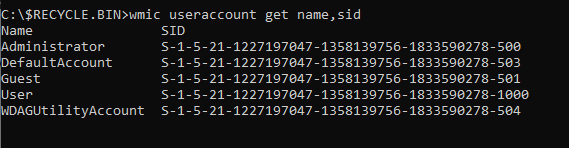
Choose and switch to users directory with SID S-1-5-21-1227197047-1358139756-1833590278-1000. in the SID directory there are files that have been deleted with random names and begin with $I and $R
$I : Contains deleted object metadata.
$R : Filled with data that has been deleted so that it can be recovered again.
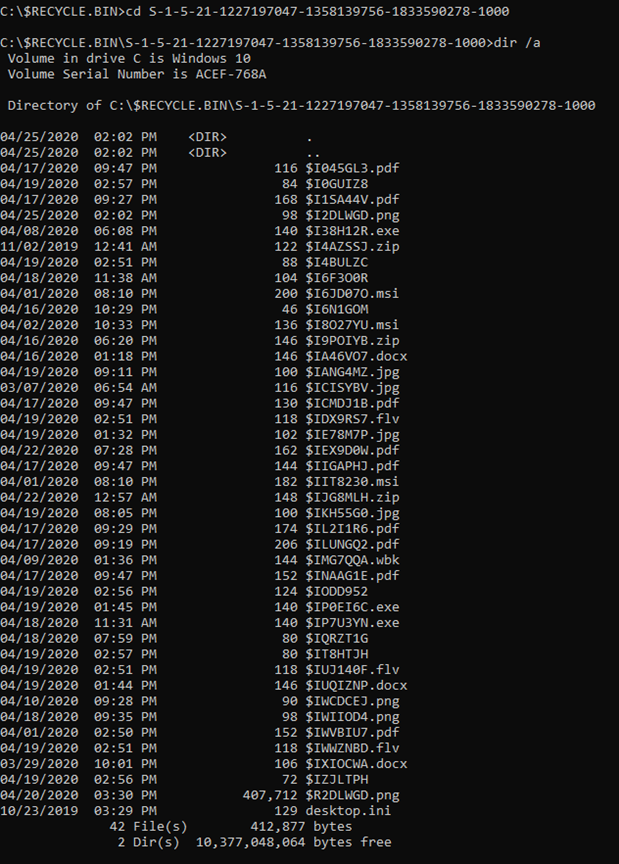
There is a list of files that we have deleted and moved to the recycle bin. Here there is 1 file with a random name that starts with $R. So, let's execute!
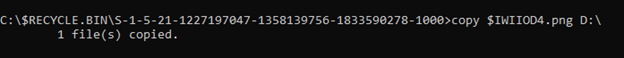
We can get a file with a random name starting with $R, but the file with the $I prefix contains deleted object metadata. We will try to obtain metadata from deleted files by copying the file $IWIIOD4.png to the D: \ directory and then using the $I Parse to get information that is easy to read, even if you don't use this tool you can also try opening it using Hex Editor
In $I Parse tool there are 2 choices of modes, where we can see the file mode or directory mode. If you use directory mode, output will be in the form of .tsv
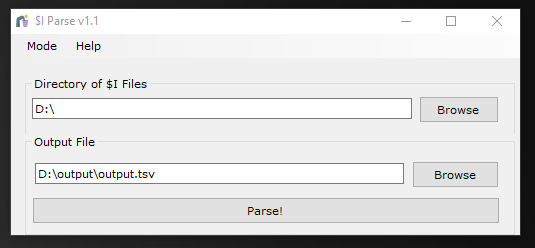
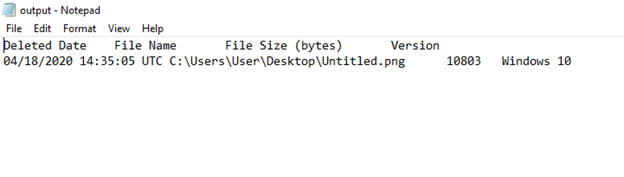
In file mode it will directly display file information that has been deleted from the date the file was deleted, file name, and file size.
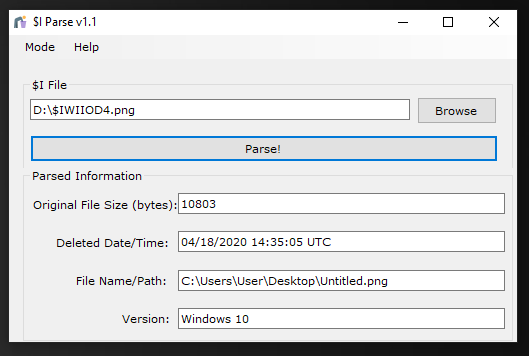
2. Web Browser
Browsers store various user activities when you search for web pages, various types of browsers such as Microsoft Edge, Firefox, Google Chrome, Brave, Opera and others have their own advantages and disadvantages both in terms of performance and privacy. The browser is not just a search engine but can be used as a user's data storage containing a users password stored for when they want to visit a website. The browser will usually ask if the user and password will be stored as history so that when the user revisits the website it does not require input because the credentials have already been stored. Here I will give an example using the Firefox browser, almost all browsers store cache so we need that cache information in the cache folder. Windows stores a folder called Profiles which contains data from applications that have been installed on the system, in my Firefox it is on C:\Users\%USERNAME%\AppData\Mozilla\Firefox\Profiles\fcp6fltm.default then there will be a number of files in the .sqlite format, so we can try to open them using the SQLite DB Browser. To see what site information users have accessed and bookmarks we can see it in the places.sqlite file and there are several other files that store various information such as:
bokmark backups - contains backups of users' Bookmarks.
cookies.sqlite - contains cookie information.
logins.json - contains the username and password information used for a particular site, when the .json file is opened you will not immediately see plain-text but have been encrypted by the browser itself using Triple DES encryption which uses a symmetrical key on the encryption so that another file is needed to be able to see the results of the decryption and the key used is key4.db. To decrypt this file we can use firepwd or firefox_decrypt tools.
downloads.sqlite - contains a list of what files have been downloaded by the browser.
addons.sqlite - contains information from add-ons installed in the browser such as version, description, url, add-ons maker and so on.
permissions.sqlite - contains permitted popup permission information from the website visited.
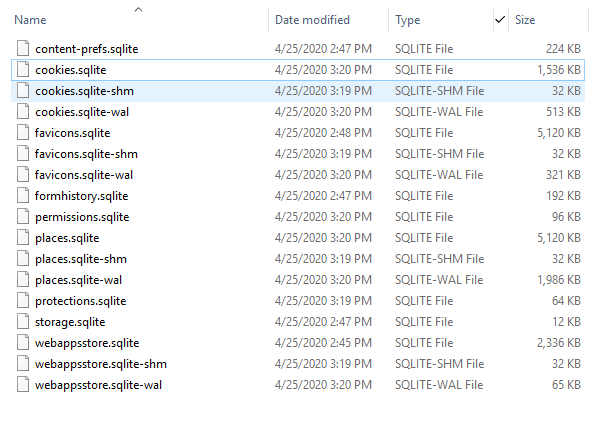
There are several tables that we can try to analyze to get information from the file:
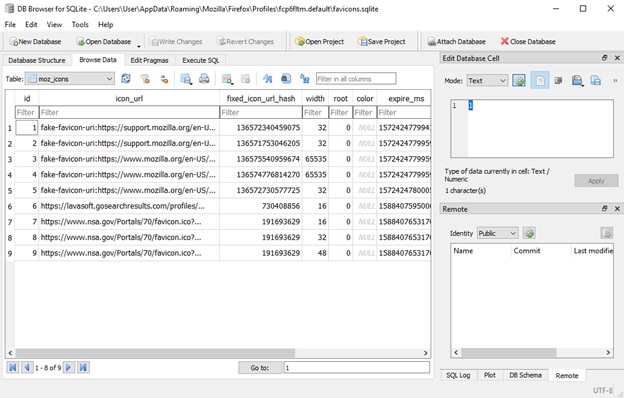
This is an example of information that we can get from the Firefox browser, of course, for other browser folder structures will be different so we need knowledge about the directory structure that exists on the Windows system so that it will be easier for us to find artifacts.

