Ransomware: Attack Techniques and Countermeasures
Learn more about ransomware attack techniques and countermeasures with infosec author Nihad Hassan.

Rapid technological development has brought with it an equal increase in cyber-attacks. Cyber-crimes have become more complex and may lead to compromise thousands or even millions of devices simultaneously. Today there are various types of cyber-crimes, and one of the latest—and most dreaded--ransomware, which is a type of digital extortion, or digital blackmail as it is sometimes called.
Ransomware is a kind of malware that prevents users from accessing their computing device resources and/or personal data stored within them using various methods. Ransomware does not intend to bring any damage to the computer file system, instead leaving it functional to provide a way for the victim to pay the ransom and to display the ransom note (i.e., payment instructions) on the victim’s screen.
The victim’s computing device (whether it is a computer, server, tablet, smartphone and even any type of Internet of Things device) data will become hostage until the device owner pays a ransom to remove the restriction.
Ransomware is an ever-growing problem that hits individuals, the public sector, enterprises, and SMBs. Recent events have focused an intense spotlight on ransomware incidents, and ransomware threats are expected to worsen in the years to come. Cybersecurity Ventures[1] predicts that a ransomware attack will hit a business every 14 seconds by the end of 2019. On the other hand, the estimated damage costs of ransomware attacks will reach $11.5 billion annually in the same period. These numbers are nothing compared with the prediction offered by Cisco systems, which indicates that ransomware attacks are growing more than 350 percent annually[2].
In this article, we are going to talk about ransomware threat, its types, infection vectors and how to defend against it in both individual and enterprise context.
The end purpose of Digital Extortion is not always to extort money illegally through ransoms, sometimes, the end purpose is to obtain information from its victims.
Ransomware types
There are mainly two types of ransomware, crypto and locker ransomware, however, ransomware belongs to the Digital Extortion category of cybercrime, which also contains -in addition to ransomware- other types of cybercrimes -which aims to illicitly acquire or denying access to target personal data in exchange for a monetary gain- such as Scareware (Fake Antivirus & Misleading App), DDoS Extortion and Data Compromise ransom.
Locker ransomware
Locker ransomware works by preventing the victim from reaching to his/her personal files through denying access to computing resources (e.g., locking desktop or preventing the victim from logging in) and then demanding a ransom to regain access.
Crypto Ransomware
This type of ransomware encrypts all personal data existed on the target machine, leaving it hostage until the victim pays the ransom and obtains the decryption key from the attacker. Some variants of crypto ransomware will progressively delete hostage files or release them to the public if the victim failed to pay the ransom on time.
After crypto ransomware installs on the target system, it will silently search for important files -based on their extensions- and begin encrypting them, ransomware will search for files on local hard drive and even all the attached external drives/network shares. After successfully encrypting all victim computer files, it will present the user with a ransom note -showing a countdown timer- asking for payment (ransom) in order to regain access to hostage files. Modern crypto ransomware type request payment –mostly- via Bitcoin cryptocurrency.
Ransomware Symptoms
It is relatively easy to find out if you are affected by ransomware, the following are common symptoms of a ransomware infection.
- You cannot open your files; you always receive an error message that the file you are trying to access has wrong extension (e.g., Windows asks you “how do you want to open this file?”) or it is corrupted.
- The ransomware may change your desktop wallpaper and replace it with a ransom note.
- Your computer is locked and you cannot access your desktop, a splash screen displaying the ransom note appears instead and cover the whole screen asking you to pay a ransom within a limited time frame, otherwise your data will get lost forever.
- Ransom note may appear in a form of a program window that does not cover the whole screen and the user cannot close it.
- You see instruction files in all directories that contain file/s encrypted by the ransomware, these files have different formats such as TXT, PNG, and HTML and its name is written in capital letters (e.g., YOUR_FILES_ARE_ENCRYPTED.HTML and YOUR_FILES_ARE_ENCRYPTED.TXT).
- Your stored file names are scrambled and have a different extension or no extension at all.
First Documented Ransomware
The first documented ransomware first appeared in 1989, it’s called AIDS Trojan (also known as the PC Cyborg virus). The perpetrator -which was a biologist called Joseph Popp- has mailed a 20,000 infected floppy disk to the attendees of “World Health Organization’s AIDS conference”, the disks were labeled “Aids Information – Introductory Diskettes” and contained an interactive questionnaire used to trigger the malware after -approximately- a 90 reboots of the victim machine.
AIDS Trojan works by concealing all directories and encrypting file names located at the C:\ drive on the victim machine making the Windows OS unusable. In order to remove the restriction, the victim has to pay a $189 to a Panamanian post office box. Although the AIDS Trojan was not sophistically built and used a simple symmetrical encryption algorithm to encrypt victim machines files which were relatively easy to overcome, however, it brought serious damage to different research centers around the world.
Some ransomware variants like Doxware threaten their victim to release their personal data (e.g., photos, videos, confidential information, IM chat conversations, and trade secrets in case the victim was a company) to the public if they refuse to pay the ransom. Another variant of the Doxwareransomware is called Popcorn Time, which gives its victim the choice to either pay the ransom or affects two of their friends with it.
Notification requirements of ransomware attacks
There are legal consequences concerning any type of cyber-attacks that involves compromising stored user’s personal data, for instance, the first legal issue that we need to consider of ransomware attacks is the notification requirements.
A notification requirement depends on jurisdiction and on industry type, for example, in the United States, all state laws have enforced data breach notification laws. Under these laws, victim entity (e.g., Corporate, charity organization, education institutes, service provider, social website or any entity/website that keeps personal information about its customers/clients) must inform the authorities of any security breach that involve accessing/suspecting of accessing Personally Identifiable Information (PII) of their users.
In the European Union, the General Data Protection Regulation, which was enacted to protect the privacy of EU citizens (Enforced on May 25, 2018), requires companies working on EU or handling/keeping EU citizen’s personal data to report any data breach within 72 hours’ at maximum. The fines imposed for breaching this regulation is costly (4% of global annual turnover or €20 million)
Ransomware Distribution Methods
There are different attack vectors employed by ransomware to invade computer systems, the following are the most common one:
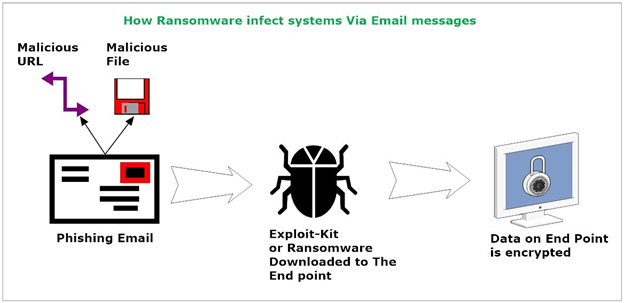
Email is the greatest gateway used by cybercriminals to spread ransomware. Email services can be utilized in different ways to spread ransomware (see Figure 1), mainly through SPAM and phishing emails.
Emails used for malicious purposes are called SPAM or phishing emails. Such emails employ social engineering tactics to convince recipients to download/open the malicious attachment or to visits the infected sites. There are different types of SPAM according to their contents, such as: Phishing Scams, Spear Phishing, Whaling phishing, Email spoofing.
Watering hole attacks
This attack works by monitoring target victim’s (whether he/she is a person or a group of employees working in a specific organization) online browsing habits, so the attacker knows which website is frequently visited by the target victim, then tries to infect it with a malware. Once victim visited the compromised website, he/she will in return get infected with a malware.
Malvertising
Also known as "malicious advertising", in this type, attackers abuse legal advertisement channels (e.g., Google Adsense) to spread malware through injecting malicious code inside ads and web pages.
Exploit kits
Exploit kit is a web-based compromise platform/framework that allows attackers to semi-automate exploitations through evaluating/detecting the victim’s OS/application vulnerabilities and matching them to the repository of exploits stored within the Exploit kit. This allows attackers to select the correct exploit for the target victim machine.
USB and Removable Media
This attack requires the attacker to have physical access to target machine unlike other types of cyber-attacks which target computers via the internet--however it still increases dramatically over the years forced by lack of cybersecurity awareness of end users.
A famous cyberattack conducted via USB drive (an old school attack) was the Stuxnet worm in 2010, this attack results in installing malware on one of the Iranian nuclear facility networks.
Installing pirated software
Malware can come bundled with other software programs, especially those downloaded from the internet. The infection happens when you install an infected program on your machine, then malware within it will install itself--silently--into your computer at the same time.
MS Office Macros
The MS Office macro has been exploited by malicious actors to do malicious actions (e.g., using the VBA KILL command to delete files) or to install malware on victim machines. For instance, cybercriminals distribute MS Office files online with a malicious macro embedded within them, and upon opening the infected office files it will do its malicious actions on victim machines.
An example of ransomware that infects machines through using the macro feature via Microsoft Word Document is the Locky ransomware.
Ransomware-as-a-Service (RaaS)
Businesses are shifting their operations from locally installed OS and applications into using software packages that run in the cloud such as the Software as a service (SaaS) model.
Ransomware as a service (RaaS) adopts a similar approach to SaaS but on the malicious side. RaaS is an online software package sold in underground markets and/or forums using a subscription-based model. It aims to simplify ransomware attacks for novice cybercriminals in exchange for a cut of ransom payments acquired by the RaaS agents.
RaaS is an emerging dangerous model that usually involves three actors: a malware author, a service provider, and agents (attackers). Malware authors develop ransomware code and integrate it into an online dashboard and present it for sale or rent. They also provide step-by-step instructions on how to launch ransomware attacks, so criminals with no technical background can use this service easily.
Remote Desktop Connection
Many companies outsource their IT support works through third-party companies, these contractors can be existed in the same country or simply overseas.
To enable these contractors to perform their job of monitoring and troubleshooting Windows networks, Windows offer a built-in feature (Also available for other OS) called Remote Desktop Protocol (RDP) that allows a user to mirror the screen, keyboard, and mouse of a remote system on his/her local device as if being exactly right there. RDP uses port 3389 to communicate.
Attackers can utilize brute-force (By exploiting weak passwords) and social engineering techniques to acquire RDP login credentials, after then install any type of malware (e.g. Deploying ransomware) on the victim machine in addition to infiltrating target network.
Cybercriminals are selling backdoors and compromised remote desktop protocol (RDP) accounts for just $10 each, this market is very active – and growing- on the dark web.
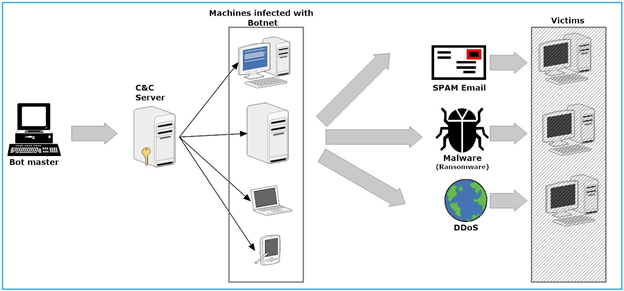
Botnets
Botnet is a compromised machine controlled by a Command and Control (C&C) server and used to launch -in associated with other thousands or even millions of compromised machines- DDoS attacks, for instance, botnets can be exploited to play another malicious role which is downloading ransomware -or any type of malware- from its C&C server to infect the computer hosting it (see Figure 2).
Zero-day vulnerability
These are vulnerabilities discovered by black hat hackers and usually found in web browsers, browser add-ons or applications – and sometimes can be existed on the OS itself. Criminals exploit such vulnerabilities to do their evil work (e.g. installing ransomware on victim machine).
Lack of training
Different statistics and research find that the lack of security awareness (lack of skilled personnel) play a key role in exposing organizations to different cyber threats, especially ransomware.
Employee awareness of IT security is considered the first line of defense in protecting information systems. Security awareness training ensures that employees are aware of the different attack techniques that may employ by cybercriminals to break into the organization’s systems and information and they know how to mitigate and report such incidences to the appropriate person.
DNS Security
Ransomware utilizes DNS service at different stages of its attack, for example, DNS reconnaissance is used during targeted attacks to gain insight about target enterprises network such as sub-domains and web hosts. DNS is also used in the delivery process of email spam campaigns carrying ransomware with it. Many Ransomware strains need to use DNS to communicate with its command and control (C&C) server. Using secure DNS servers to block malicious activities become crucial to mitigate, detect and respond to such attacks more quickly.
The following is a list of DNS-based threat blocking providers
1. OpenDNS (https://www.opendns.com) 208.67.222.222 - 208.67.220.220
2. Comodo (https://www.comodo.com/secure-dns) 8.26.56.26 - 8.20.247.20
3. Yandex.DNS (https://dns.yandex.com/advanced) 77.88.8.88 - 77.88.8.2
4. Quad9 (https://www.quad9.net) 9.9.9.9
For enterprises, they should consider having a secure in-house DNS server, or subscribe for a commercial threat-blocking DNS service with more advanced capabilities -than the free providers already mentioned- for maximum protection.
Countermeasures against ransomware attack
There are different technical and procedural countermeasures to stop ransomware before it infects our system, the following are the main one for both endpoint devices and enterprise networks.
For endpoint devices
- Install security solutions (anti-virus and anti-malware).
- Update OS and installed applications.
- Use virtualization technology: A user can execute programs, open e-mail attachments, download and install internet programs, and visit compromised web sites safely without being afraid of infecting his/her operating system with malware, as the virtual machine will run in a sandbox isolated entirely from its host machine’s operating system.
- Use Web Browser Privacy Add-Ons: Such as,
- Privacy Badger (https://www.eff.org/privacybadger)
- HTTPS Everywhere (https://www.eff.org/https-everywhere)
- NoScript (https://noscript.net)
- uBlock Origin (https://addons.mozilla.org/en-US/firefox/addon/ublock-origin)
- Disable Macros in office files.
- Disable Windows Script Host (WSH).
- Use Least Privilege account.
- Do not install pirated software, especially the one downloaded from torrent website.
- Avoid plugging untrusted USB devices to your computing device.
- Avoid Public Phone Chargers – A malware can be delivered via such public chargers.
- Change important files extensions : This trick can be effective to prevent damage caused by many types of ransomware strains, for example, WannaCry ransomware search and encrypt specific file extensions such as: MS Office files (e.g. .doc,docx,.xls,xslx,.ppt,.pptx ..etc.), different backup archive file types (e.g. .zip,.rar,.bakcup,.bak) and popular image/video file formats. By changing your important file’s extension’s name to something -arbitrarily- you can avoid many types of ransomware.
- Backup your data. This is still the best effective procedure to recover from a ransomware attack.
- Configure Windows to better fight ransomware
- Show file extensions by going to Control Panel > File Explorer Options. In Windows 7, select Control Panel > Folder Options and go to the View tab, deselect the option “Hide extensions for known file types.”
- Disable AutoPlay.
- Disable Remote Desktop Protocol (RDP), and if you need to use it, make sure to secure it with a strong password (16 alpha numeric characters).
- Enable Software Restriction Policies (SRP).
The Endpoint device includes any Internet-capable computing device such as desktop computers, laptops, smartphones, tablets, Internet of Things (IoT) device, printers or other specialized hardware such as POS terminals and smart meters.For enterprise
For enterprise
- Efficient Patch Management.
- Enforce Physical security controls within your organization.
- Network Segmentation.
- Deploy a generic anti-ransomware product.
- Vulnerability Management: is the practice of identifying vulnerabilities in computer systems and then working to remove their risk before they get exploited by a malicious actor.
- Deploy Next-Generation Firewalls & Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS).
- Use network sandboxing technology, so suspicious files can be executed first at network perimeter before allowing it to access enterprise network.
- Malicious URL Blocking, we can configure firewall to play this role.
- Deploy Honeypots.
- Deploy anti-spam technology and make sure to scan all in-coming and out-going email messages.
- Implement Data classification policy.
- Enforce strong password requirements.
- Implement software usage restriction policy.
- Govern USB drive use.
- Maintain effective backup & recovery strategy.
- Enforce security policy.
Data sanitization
Email attachments and files downloaded from the internet are commonly used as a vehicle to carry out malicious code. Data sanitization (also known as Content Disarm and Reconstruction (CDR)) is a protective anti-malware technology that assumes all files entering the enterprise network are malicious and works to sanitize each file (removing potentially malicious code) before passing it to the endpoint device. Utilizing a data sanitization system at all entry points such as email attachments, web browser downloads and even on endpoint computers to sanitize files carried within USB devices, become an essential protection measure against unknown malware and other advanced attacks exploiting zero-day vulnerabilities.
A security policy is a major element for any organization operating in today’s information age and want to secure its work environment from both internal and external threats. Regardless of the size of an organization, having a security policy is essential to address all possible security threats and to suggest countermeasures before they occur.
According to a report titled “Today’s State of Vulnerability Response: Patch Work Demands Attention” published by ServiceNow and the Ponemon Institute that addresses the importance of patch management, found that “Fully 57% of respondents who reported a breach said that they were breached due to a vulnerability for which a patch was available but not applied. 34% say they actually knew they were vulnerable before the breach occurred.”[3]
Summary
Ransomware has proven to be a highly effective form of cyber-attack afflicting both businesses and individuals. Ransomware can spread using different methods, mainly by using the email system or via compromised websites housing Exploit Kits. However, the most attack vector is still the lack of end-user training in IT security issues, for instance, most ransomware attack methods can be stopped by a conscious user who thinks twice before -for example- clicking a suspicious link sent via email or through direct IM chat.
As malware authors continue their endeavor to write advanced malicious code and work to develop new spreading methods, we can expect to see future ransomware families will come supplied with more capabilities to evade detection and to automatically propagate to other networks and even infect IoT devices such as smart watches, smart TV and medical devices, however, until then, the knowledge acquired from understanding the behaviors -in terms of the infection vector, communications model and how it spread- of currently deployed ransomware families, will help us to understand and defend against the new ransomware families that are going to appear in the future.
[1] Cybersecurityventures, “Global Ransomware Damage Costs Predicted To Hit $11.5 Billion By 2019” September 25, 2019. https://cybersecurityventures.com/ransomware-damage-report-2017-part-2/
[2] Cisco, “Cisco Cybersecurity Report Series” September 25, 2019. https://www.cisco.com/c/en/us/products/security/security-reports.html#~stickynav=2
[3] Servicenow, “Today’s State of Vulnerability Response: Patch Work Demands Attention” , April 25,2019 https://www.servicenow.com/content/dam/servicenow-assets/public/en-us/doc-type/resource-center/analyst-report/ponemon-state-of-vulnerability-response.pdf
About The Author: Nihad Hassan (@DarknessGate) is the author of a number of books on digital forensics, open source intelligence (OSINT) and digital security. This article is an excerpt from his latest published book "Ransomware Revealed" Published by Apress. Other books related to OSINT, Digital Privacy and Digital Forensics from the same author can be found here.


