How to Hack An Insecure Web App: OWASP WebGoat Challenge (Part 2)
Mars Groves teaches us how to steal credit cards from a database as part of the OWASP WebGoat challenge.

Previously, in the first walkthrough article of my three part OWASP WebGoat challenge series, I demonstrated how you can break the authentication scheme in an insecure web app, now, I am going to show you how to steal credit cards from a database.
Part 2: How to Steal Credit Cards From a Database
A malicious actor can steal all credit card numbers from a database on an insecure website or web application that requires a credit card to purchase any of its products or services on sale. They can use a number of techniques to accomplish this, but for the purpose of this walkthrough, I will show you one simple way how they can achieve this.
So, how do they do it?
They tamper data.
What kind of data?
Cookies!

Cookie Monsters That Are Not So Nice
Most of us may already be familiar with the blue Cookie Monster from Sesame Street. Every time he would get a chance to come near any cookies, he would grab a bunch of them and get his hands full and chomp, chomp away! He doesn't care about anything else. He even has a song dedicated to cookies, and the lyrics go like this: "C is for Cookie, and that's good enough for me."
Well, guess what?
The bad guys think so too.
I'm not talking about the delicious chocolate chip kind either.
I'm talking about cookies stored on your computer.
What exactly are cookies?
Cookies (also known as HTTP cookies, web cookies, or internet cookies) are small data packets sent from a website that are stored on your computer by your browser for tracking purposes. While you're browsing a website, you may not be aware that cookies are being stored from your browser to your local machine for future use to identify you.
This can present serious problems when there are security vulnerabilities on a insecure website that may allows its cookie's data to be read by a malicious actor who may use it for the following: to gain access to user data, obtain user credentials, or to login to a website with malicious intent such as exfiltrating credit card information. Look into cross-site scripting (XSS) and/or cross-site request forgery (CSRF) attacks for more on this.
These kind of cookie monsters are not very nice!
Let me show you how they can steal credit cards just from tampering a cookie!
How to Steal Credit Cards from Database with a Cookie
In this walkthrough, I will demonstrate a simple technique that malicious actors can use to tamper data on an insecure website/web app to steal your financial data such as credit card information. In this walkthrough, I will show you step-by-step how the bad guys do it!
Step-by-step instructions:
1) Login to insecure website from the attacker machine (Kali).
2) Add a "tamper data" extension to your web browser. In this scenario, we will be using the Tamper Data for FF Quantum extension on a Mozilla Firefox web browser.
3) Go to the checkout page where credit card payments are required to make a purchase. In this case, it is the page where the "Buy Now" button is present.
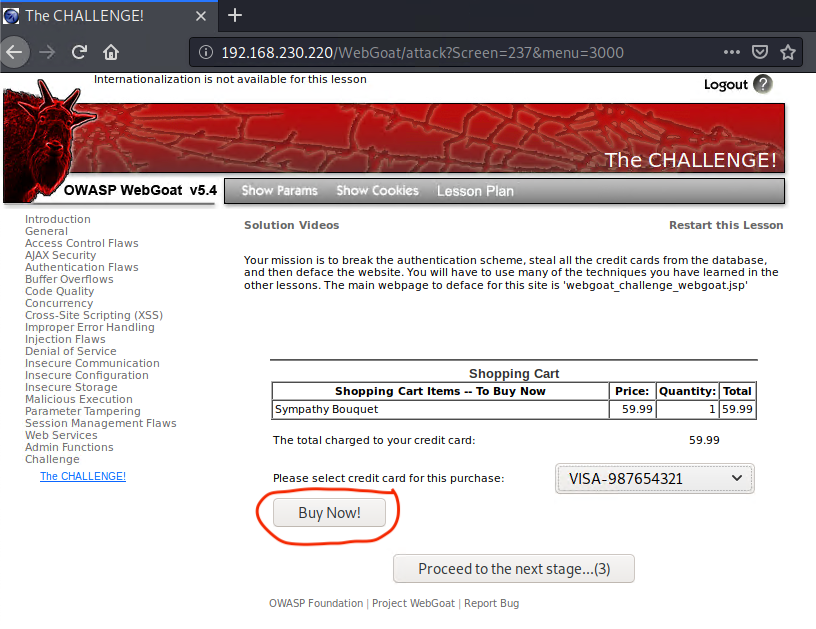
4) Next, click on the Tamper Data for FF Quantum add-on extension which will be at the top-right corner near the URL address bar. Once it opens, you will see a list of choices to select. Keep the default selection, and then click "Start Tamper."
5) Return to your checkout page and click on the "Buy Now" button! You should see the Tamper Data add-on pop up like this! It will show the Request Body information such as credit card information and the user youaretheweakestlink.
6) Click on the "Ok" button seen in the Tamper Data for FF Quantum extension underneath your username.
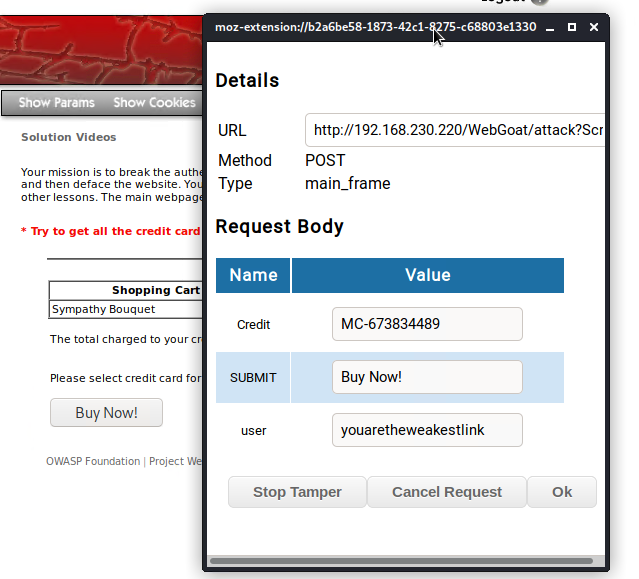
7) You will see the POST HTTP request which will include the cookie that has the user information inside of it.
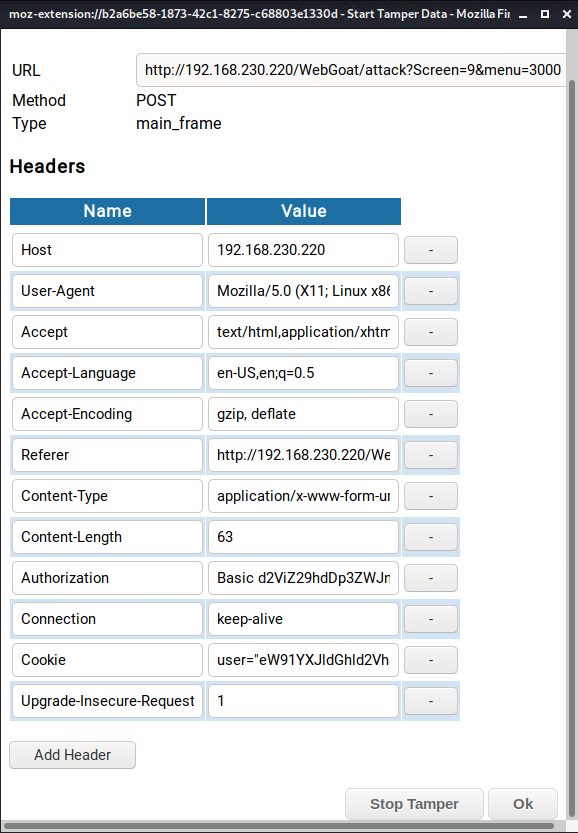
SQL Injection
This is the eighth step that is the juiciest part! We will copy the cookie's user details inside of the double quotation marks before we will execute SQL injection inside the cookie parameter. Since the cookie's user details are shown in Base64 format, we will also decode the Base64 cookie data we just copied at https://www.base64decode.org to verify the user.
💡 Tip: One way to quickly tell if data is in Base64 format while scanning is to check if there is an equal sign(s) present at the end of the scrambled letters/numbers.
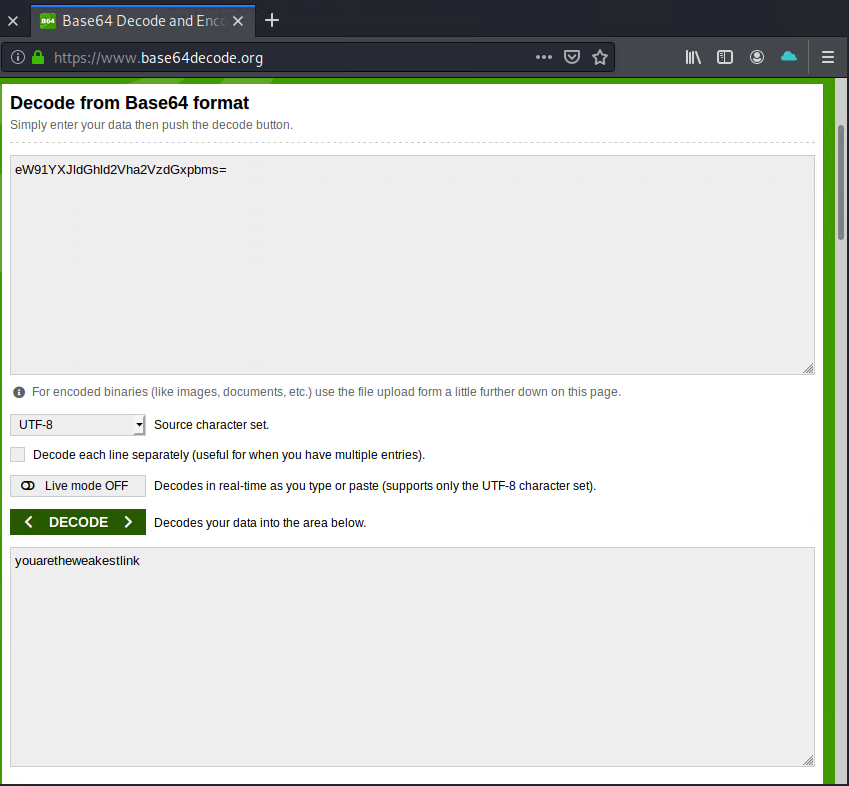
Here, we copied the Base64 data inside of the cookie's user details and we decoded it. We verified that the user is indeed youaretheweakestlink.
9) Now, we are going to emulate malicious actors and do something very bad! We will tamper the cookie parameter with SQL injection inside of the user details in order to grab credit card details of ALL users on the website, and not just you as the user youaretheweakestlink.
Here is the SQL injection code to accomplish this.
youaretheweakestlink' or '1'='1
However, the cookie parameter must be in Base64 format, so that the code can be executed. We will go to https://www.base64encode.org so we can encode it into Base64 format as seen below.
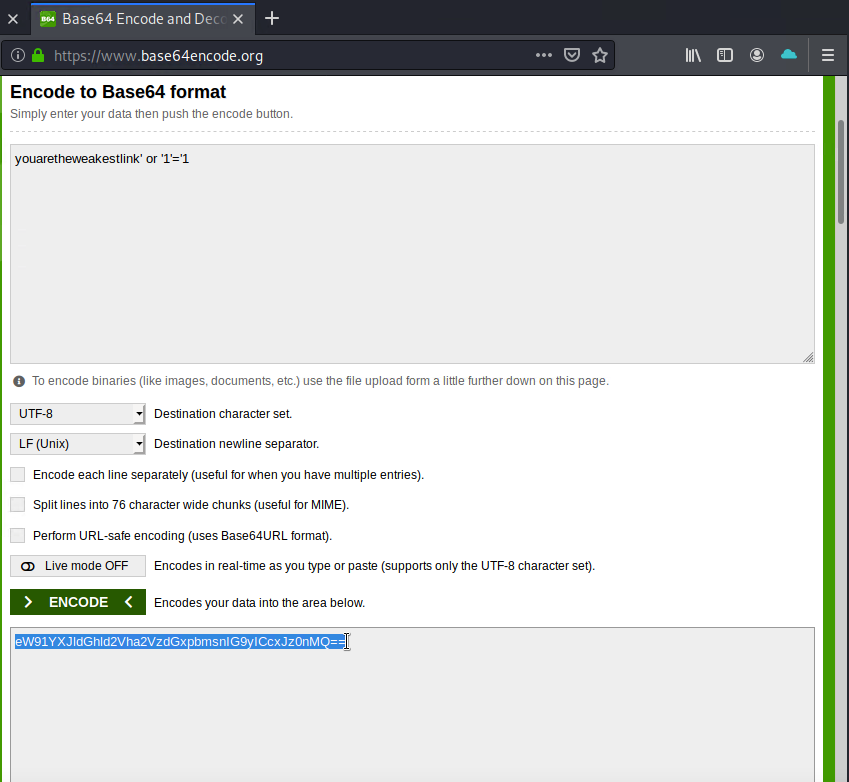
9) We will copy the SQL injection code in Base64 format and paste it into the cookie parameter inside of the double-quotation marks for the user using the Tamper Data extension.
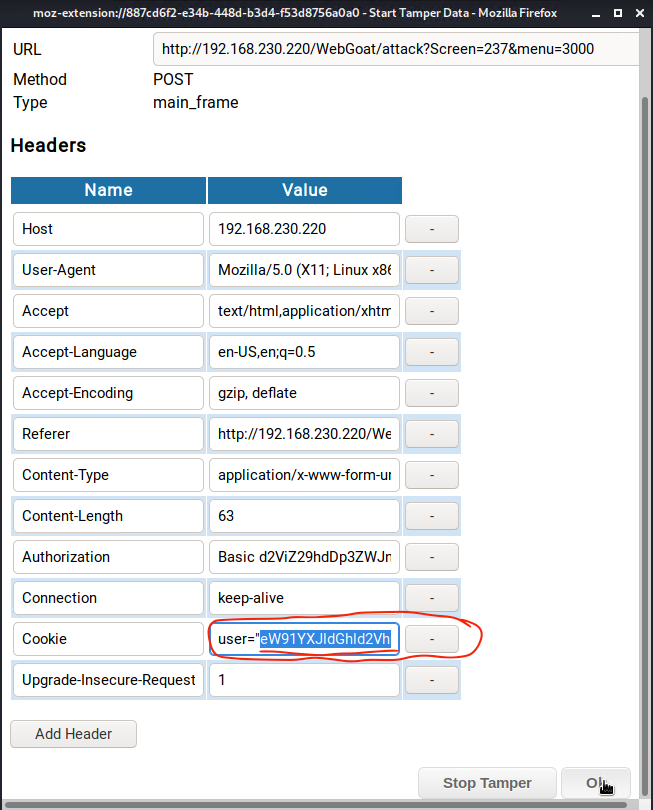
Now, we will click "OK" and watch the magic happen!
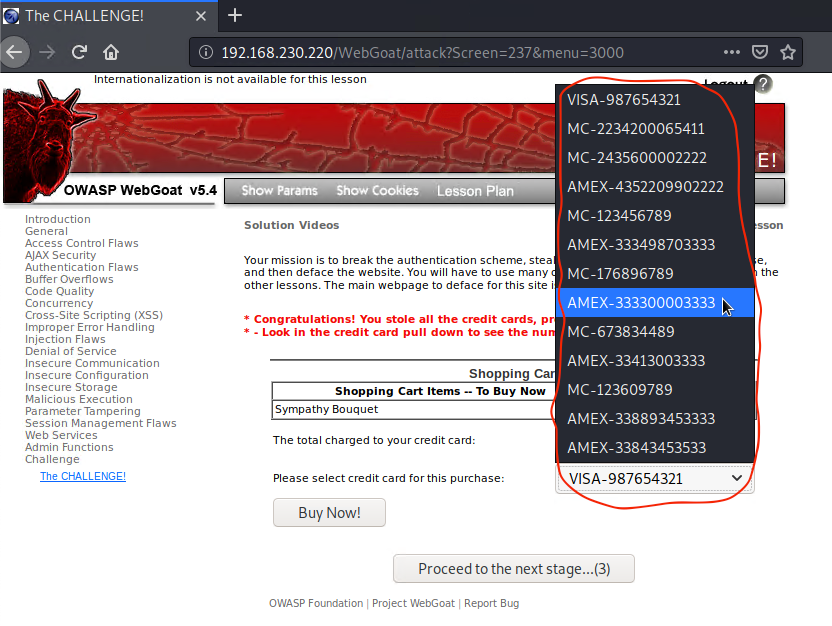
VOILA! We have successfully captured all credit card information details from ALL users on an insecure web app. Just like the bad guys!
Protect Yourself From Using Insecure Websites
Anytime you log into a website especially when you will be purchasing anything with a credit card, only use the HTTPS link and never the HTTP link version. The HTTPS protocol is the secure version of HTTP. The S stands for Secure. HTTPS transmits all data using Transport Layer Security (TLS), formerly known as Secure Sockets Layer (SSL), which encrypts communication. It is very hard to decrypt data sent to and from a server with the HTTPS protocol.
This is why it is imperative for all users to log into a website using the Hyper Text Transfer Protocol Secure (HTTPS) protocol e.g., https://yourwebsitehere.com link rather than the Hyper Text Transfer Protocol (HTTP) protocol e.g., http://yourwebsitehere.com.
When accessing insecure websites, it is advisable to visit them from a virtual machine or with remote browser isolation. This will protect your computer from malicious actors on the web. Remote browser isolation may be a preferred choice when browsing the web, since your cookies will not be stored after each browsing session which gets deleted after it ends.
⚠️ DISCLAIMER: Do not try any of these tactics on a web application from any device without written legal permission. This warning is here to spare you any potential legal troubles, jailtime, and/or termination from your job. Only try these tactics on web apps that you are legally permitted to, including web apps deliberately made insecure for anyone who wants to break or research them.
Stay tuned and learn how to deface a website in the final part of the OWASP WebGoat challenge coming soon.
Happy hacking, folks! 🍻

