Gab OSINT Techniques
Learn about the OSINT exploitation points on Gab, including tools and techniques to help you get the most out OSINT investigations on the platform.

Gab is one of the more recently created social media sites and one that most OSINT investigators are unlikely to have dealt with. The social media platform has attracted groups that are overwhelmingly conservative and although it lacks the large and more diverse user base of other platforms that have been around for longer, it can be a good source of OSINT depending on your target’s demographics.
This article is designed to lead users through the many points of OSINT exploitation which may be found on a Gab account and provide a list of tools and techniques to assist in quickly getting the most out of the platform for an investigation.
Avatar
All Gab accounts should have an avatar as you are given a default one once you sign up. If the user has not changed it from the default one then there will be little investigatory value. However, for those that decided to upload their own avatar there are a few things that one can do to obtain more information.
Primarily, a reverse image search (such as on Google, Bing, Yandex, or Tineye) should be done to check if the profile photo is unique and/or posted on other social media platforms. You will need to get the URL of the photo in order to run the reverse image search which can be done by right-clicking the photo and selecting the Inspect Element option. You will see a bit of code similar to the below which contains the full-size URL of the photo within the parenthesis and quotes:
background-image: url("https://gab.com/system/accounts/avatars/000/000/031/original/172d581295620605.png?1573147377")
Searching this link at images.google.com I discovered that the photo was unique to only Gab and its Dissenter platform.
It is also a good idea to pull the full-size, uncropped, photo for visual inspection by pasting the photo URL from the above source code in the browser’s URL bar. This will allow you to see the full photo and better see all of the smaller details and any bits that might have been cropped out when the photo was covered with the circular mask.

Display Name
The display name is the uppermost name on the user’s account profile and is a larger font size than the username. The display name is not unique to an account and multiple users may have the same display name. Depending on how the user has set their display name it might give an indication of their real name or provide an additional username for searching.
In our above example the user has set their display name to mirror their username. It is likely that this user used their real name in this scenario. Partnering this information with their place of origin found in their biography section would be a good starting point on tracking down this user in real life or on other social media platforms.
Username
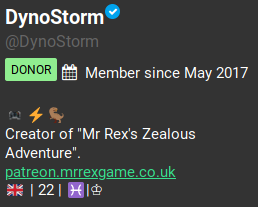
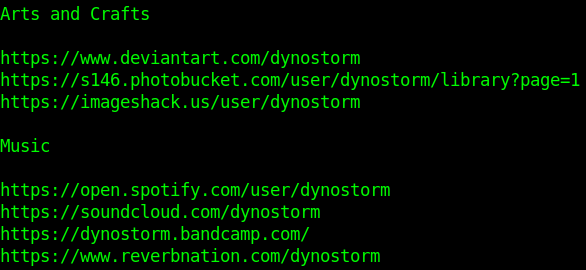
The username will appear directly below the user’s display name and will always begin with an @ symbol and be in the URL of the user’s profile. Usernames are a unique identifier and can only belong to one account at a time and should be searched across other platforms. There are a number of tools that specialize in username searches or you can run the username through a search engine with the username in quotes (such as “DynoStorm”)
Using our above user I ran their username through Google and SULTAN. They both caught numerous accounts on different platforms (with some false positives) to dig further into.
Profile
The user’s profile will contain much of the information that can be collected on a target account. The profile is viewable by adding the target’s username to the end of https://gab.com/ (ex: https://gab.com/##USERNAME) This page will contain the user’s avatar, display name, and username as mentioned above. It will also include additional points of exploitation such as a header photo, user biography, links to the user’s followers and follows, the approximate account join date, as well as profile metadata, and a number of possible badges.
Profile: Header

Gab users have the option of adding a header image which displays at the top section of their profile or their group. This photo should be analyzed much in the same way as the target’s profile photo. A reverse image search is often a good way to start and the full-size photo should also be retrieved in order to do a visual inspection. The full-size photo can be retrieved by right-clicking the header image and clicking View Image. From here you can copy the URL for the reverse image search or manually inspect the photo for details. Taking our above example, we pulled the full-size image, which shows some additional part of the photo hidden in the cropped version.

The reverse image search results came back showing us images that are very similar, but with differing faces superimposed on the hands. The multiple versions of the image suggest that tracing it back to a single account would be unlikely.
Profile: Follows
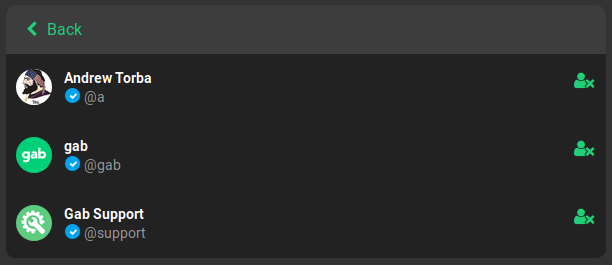
A user’s follows list of all users that the account is currently following. In most cases the user’s follows list will be more useful than the list of their followers as the target is choosing to follow these accounts. For popular accounts in particular this will normally provide a shorter list to analyze. Additionally, these accounts may provide further information on the target’s pattern of life or accounts that they might know in real life or on other social media platforms.
The example above is what a user’s default follows list will look like when an account is created. Be mindful that these three accounts (Andrew Torba, Gab, and Gab Support) appear to be added automatically when new accounts are created. Therefore they will not provide any investigative value other than perhaps suggesting the account has not been heavily utilized.
Profile: Followers
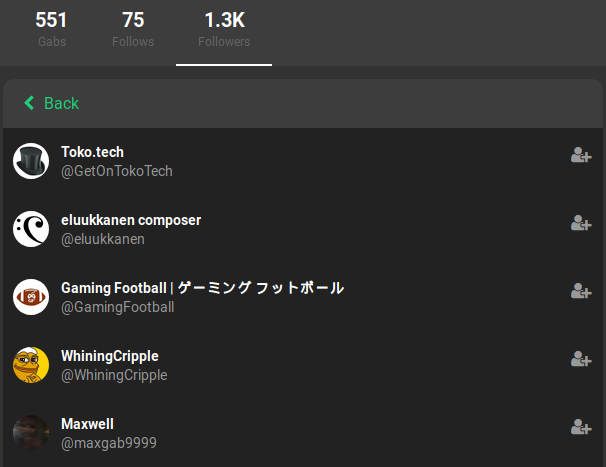
A user’s followers list will contain list of all users that the account is being followed by. This list can be scrolled through and clicking on each account allows an investigator to view each follower’s profile. A user’s followers will not provide as much investigative value as their follows as the account owner does not choose who follows them. At the same time, this list may assist in finding users that might be associated with the target, though it may be more difficult on larger profiles with large follower counts. In our above example we can see that the target is being followed by over 1000 accounts; making sorting through them one by one an impossible task.
Profile: Badges
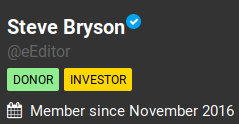
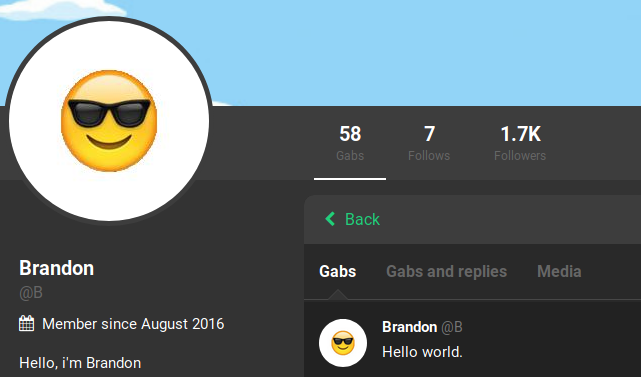
User accounts may exhibit a number of badges on their profile indicating different statuses. The badges listed on the account might show that the user is an investor, a donor, has Gab Pro, or is a bot. There is an additional badge that appears as a white check mark inside of a blue bubble next to the display name which is given to verified accounts. These badges can be useful in determining the legitimacy of the account based on how many are included. Investigators must be aware that the bot badge can be chosen by a user without the account actually being a bot. In our above photo the user has both donor and investor badges as well as a verified badge. This suggests that the account has invested money into the site and the account owner is verified as who he says he is.
Profile: Join Date
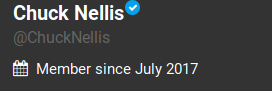
A user’s join date appears under their username on their profile. This line gives an approximate date, showing only the month and year, in which the user joined Gab. The join date can be useful in determining how long an account has been on the platform, with newer accounts being more suspect than older, more established accounts when it comes to trolls or other troublemakers. It is important to note that the website went public in May 2017, which means our example below is one of the more seasoned accounts and was created approximately two months after the open launch.
Profile: Biography
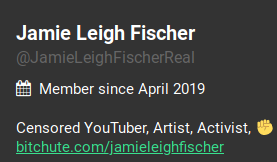
Directly below the join date on a user’s profile is the user biography. This is a section that allows a user to add a text description of their choice. This section is empty by default, however can be a valuable resource when researching a Gab account. The user may use this section to provide real-world information, such as their name, occupation, location, or other pattern of life information.
In our above example, the user's profile includes a link to another one of her accounts on another platform and also mentions that they were on Youtube as well. Using this information I was able to find additional accounts to exploit.
Profile: Profile Metadata
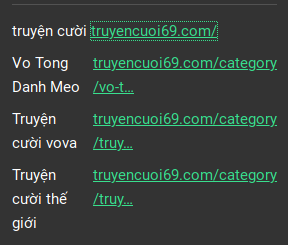
The profile metadata section can be found directly below the account’s biography if both sections are listed. This section is similar to the biography section in that it allows the user to add text, however the profile metadata section is a bit more structured. Rather than one large text block, profile metadata is constrained to a table-like area of up to four rows and two columns. This is commonly used for putting additional social media accounts or other relevant links.
The example above has a user which used the entire space of the profile metadata fields. Their links all lead to various sections of the account owner’s personal website. Once there I was able to find additional links to other social media accounts.
Gabs and Replies
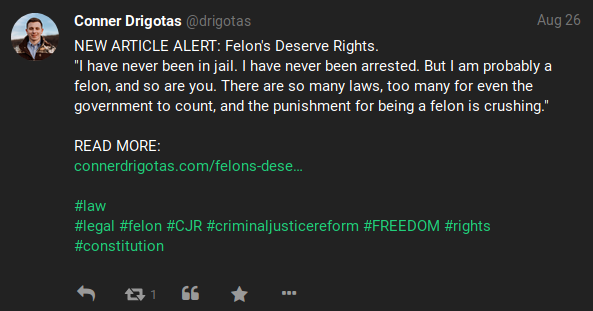
Gabs are the posts that users make on the social media platform. These posts can take many different forms: including plain text posts, polls, posts containing media such as photos or videos, links, and hashtags. What information can be gleaned from a user’s posts can vary wildly as some might post nothing of value while others may have loose lips and give away notable information which can be used in an investigation. Users may also make comments on Gabs, with these replies able to contain the same forms of content as the original posts. Analyzing all of a target’s Gabs and replies are a good way to gather information on a subject, however users with a large number of posts can quickly make it difficult to sort through.
Our above example shows a post which is information-rich and includes a number of hashtags, a link to the user’s personal website, and text (including a unique quote) all which can be exploited during an investigation.
Gabs: Pinned Gabs
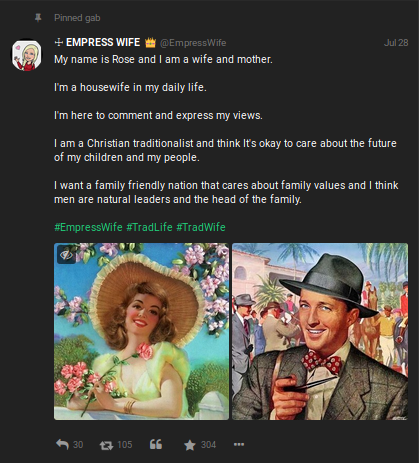
Similar to Twitter, users may pin one of their Gabs or replies to the top part of their profile so other users visiting their profile see it first, regardless of when it was actually posted. In addition to being posted at the top of a user’s profile, pinned Gabs will also show a pushpin and the text “Pinned Gab” at the upper left side of the post. Multiple Gabs or replies can be pinned on a user’s profile and these pinned Gabs tend to contain information that the user feels is highly relevant and wants others to see, whether for additional user interactions or otherwise.
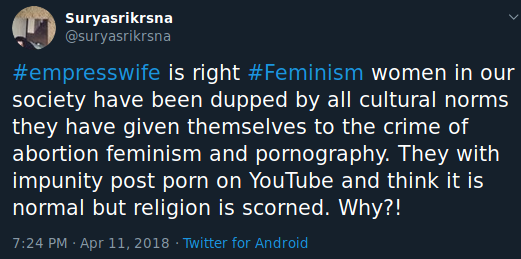
Our above example gives us a very quick read on our target’s beliefs and general information about the user. We can quickly see that the user is female, likely with the first name Rose, is married, has at least one child, and identifies as Christian. The addition of hashtags may also prove useful for finding additional posts to exploit, such as this possibly related post found on Twitter using the same hashtag.
Gabs: Timestamp
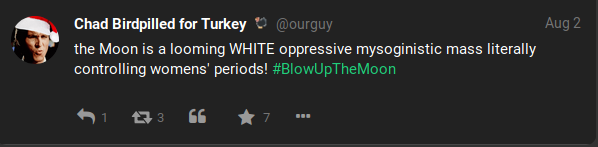
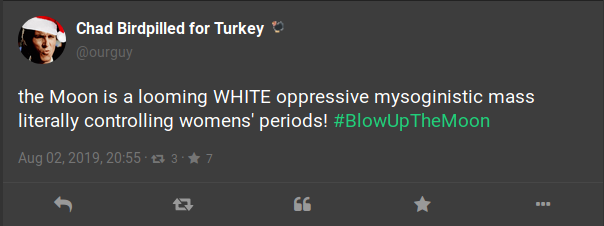
Gabs and replies will also show the time (down to the minute) that they were submitted to the website. This full timestamp may not display at first and instead may appear only as a day and month. Clicking on the individual post will open it in the same window and bring up a different view, with the full timestamp appearing at the bottom of the post above the interaction icons. The full timestamp will assist in investigations which are especially sensitive to the time in which events occurred. Our example above shows a Gab posted with the shortened timestamp view. This one shows only the day and month, however when clicking on the post it will display the below example which provides the day, month, year, and time (hour and minute) the post was created.
Gabs: User Interactions
Users can interact with Gabs and replies in a number of ways including replying to the post, as well as reposting, quoting, or favoriting the post. Replying and quoting are just as they sound. Reposting works similar to Twitter’s retweet option whereas favoriting is like Twitter’s option of liking a tweet. These interactions can be tracked by the number next to their corresponding icons at the very bottom of a post. Clicking on the number next to the social interactions will bring up a second view in which one can see further information on the social interactions from other users.
Viewing the list of social interactions can allow an investigator to see which accounts a user has regular and consistent interactions with. In our above example clicking on the number next to the reposts icon displays a long list of all users which reposted the Gab, including those in the photo below:
Gabs: Photos
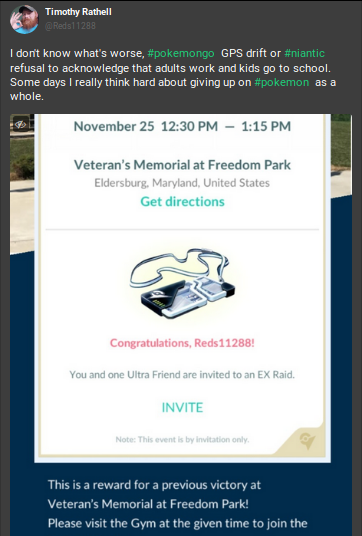
Users also have the option of adding one or more photos to their posts, though the investigatory value of a photo will vary. Some may contain a great deal of identifiable information such as selfies or photos of documents with names and locations whereas other might contain no value whatsoever. As previously mentioned, always run a reverse image search on any photos you find as a preliminary step. Next, we will want to obtain the full-size, uncropped photo uploaded by the user. To do so, we will need to click on the photo within the Gab and it will open the photo up in a new view via a pop-up like below:
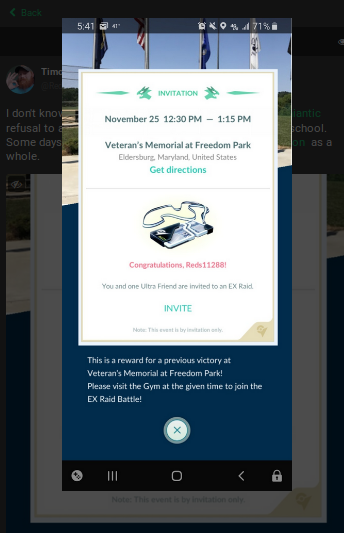
This uncropped photo provided us with more information, but we still want to save the full-size version for further exploitation. From here we can right-click the photo again and select “View Image” to obtain the largest version of the photo available.
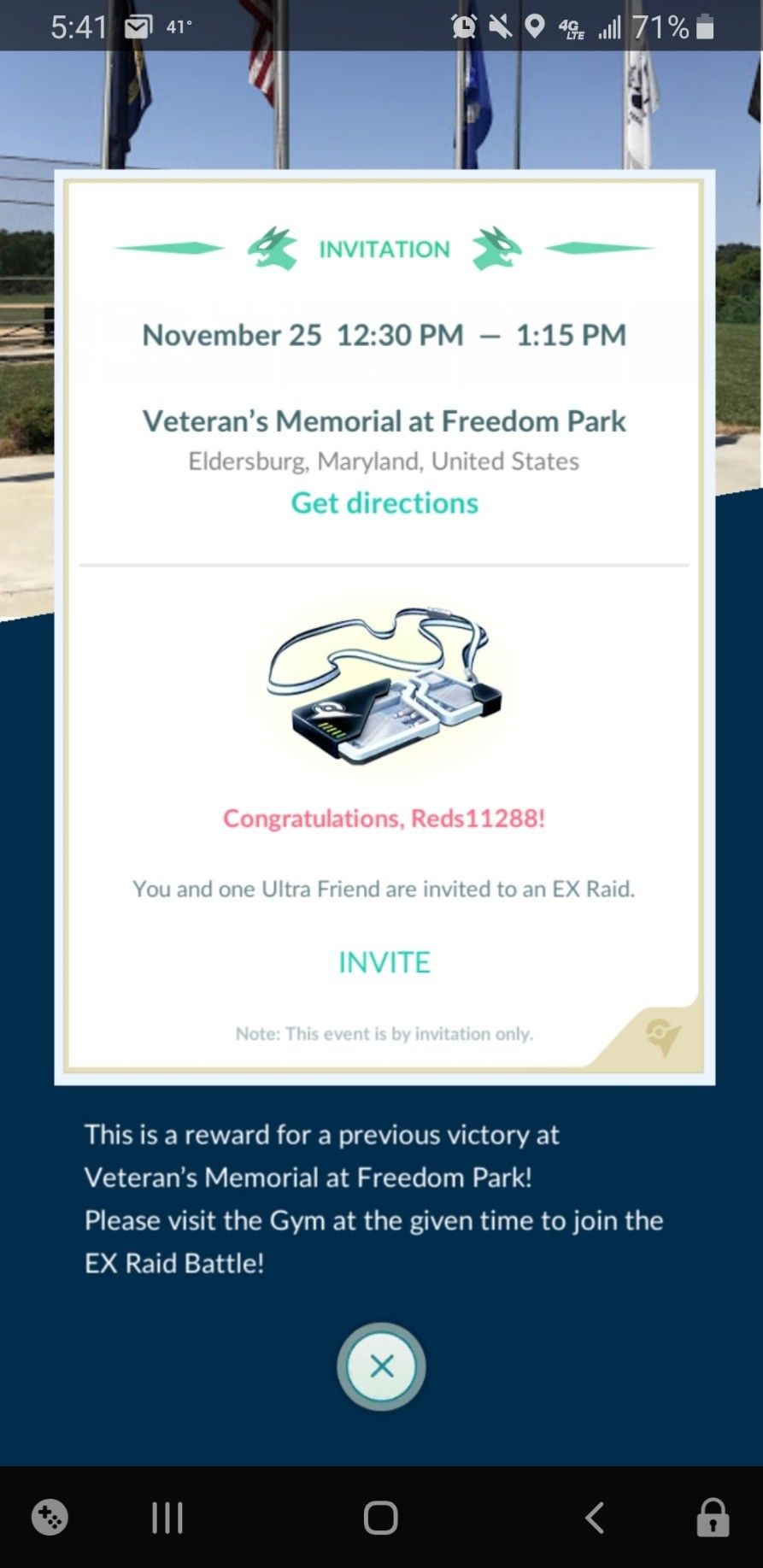
Our above example provides a treasure trove of information on this particular user. In just this one photo we can see that he is a Pokemon Go player. We can also see his username for the game which can be searched for on other platforms, as well as the location of where he has an EX-Raid in Maryland, United States. This means that at some point in the week prior the user participated in a raid at this specific park. This would greatly assist in narrowing down where to look for the target by allowing us to focus our search queries to the Maryland area.
Gabs: Videos
Users may also add a video to their Gabs, however these videos can vary in terms of how they are uploaded and how they can be exploited. Videos may offer a wealth of information if they were originally recorded and uploaded by the user. Those that the user simply shared from elsewhere are not as valuable, however they can still give insight to the user based on their content. It is a good idea to download a copy of all videos when possible so that they can be exploited later without the risk of the user or the platform removing them. I tend to treat and exploit videos as a large set of sequential photos; analyzing frames individually for their content when necessary.
During the research for this article it was noted that the vast majority of Gab videos appeared to be uploaded from a third-party website and then a link to the video was embedded to the post rather than being natively uploaded into Gab. In these cases the video will not play, but will require the user to click the link to go to the video. To download these videos, you may need to find an add-on or tool designed to download videos (for example, https://www.youtubeconverter.io/ for Youtube videos).
For natively uploaded videos, right-clicking the video and selecting “View Video” will open the video file URL (for our above example:
https://gab.com/system/media_attachments/files/016/736/441/original/2ea2ace37c4759c0.mp4?1573908810)
From this view we can right-click the video once more and select the “Save Video As” option to save the file to our computer.
Videos also contain a thumbnail which can be reverse image searched to find it on other platforms or saved to look at later. To find this thumbnail right-click the video in the Gab like above, however instead of selecting “View Video” choose the “Inspect Element” option. This will open up some of the source code, which we can then use to search for “playsinline”. The lines following “playsinline” will include the URL to the video as well as to the video thumbnail such as below:
src="https://gab.com/system/media_attachments/files/016/736/441/original/2ea2ace37c4759c0.mp4?1573908810" -- (Note: Video Url)
poster="https://gab.com/system/media_attachments/files/016/736/441/small/2ea2ace37c4759c0.png?1573908810" -- (Note: Thumbnail Url)
Using the video thumbnail found above to do a reverse image search, I was quickly able to determine that the creator of the video used stock video footage in the video uploaded by our target.
Gabs: Hashtags
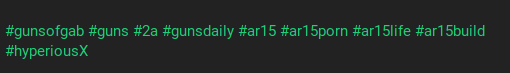
Hashtags operate in a similar fashion on Gab as with any other social media site. Users may add hashtags to their Gab (or reply, or profile sections, etc) which allow other users to quickly thumb through similar content utilizing the same hashtags. You can do a quick search for a hashtag on Gab by adding it to the end of the following URL: https://gab.com/tags/ . Hashtags may provide additional information such as locations, names, usernames, groups, further information on what appears in the connected media, etc.
The above set of hashtags are associated with a post including a photo of a custom AR(Armalite Rifle)-15. The overall collection of hashtags tell us that the user is likely a firearm enthusiast and would likely be found on other platforms using similar hashtags and or in groups devoted to this interest. Additionally, the #hyperiousx hashtag is unique enough (and turns out is the user’s username) that it could be used on other platforms to locate the user, such as on Twitter.
Gabs: Hidden Text
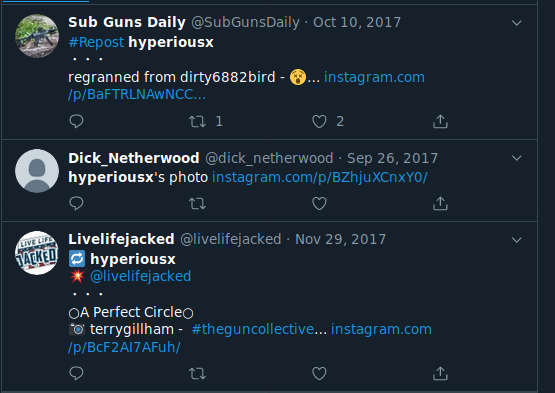
Gabs may also include text that is hidden to other users by default. Think of this as somewhat of a spoiler function in which clicking on "SHOW MORE" will unveil the rest of the text that has been hidden by the user. Be sure to always toggle this option when investigating Gabs as the can sometimes provide valuable information including additional text and/or hashtags. Below is the same post after clicking on the "SHOW MORE" option:
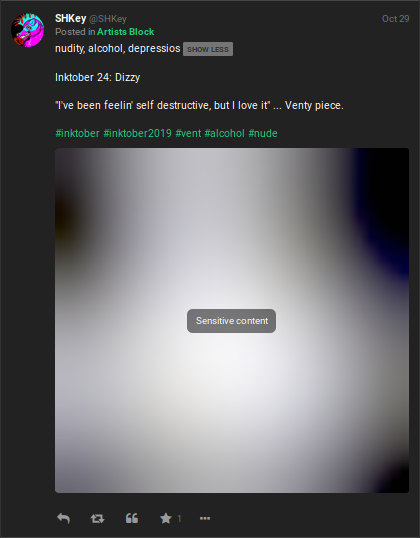
The above Gab gives a good visual example on how much more information a user can pack into the hidden text portion of a Gab. In the hidden text, the text of Inktober 24 might suggest the artwork was created on the 24th (rather than on the 29th when it was posted), or possibly that it was the 24th piece created for Inktober overall with the user missing a few days. The additional hashtags referencing Inktober assisted in quickly finding other posts by the user or others with similar content without having to sort through their other Gabs.
Gabs: Sensitive Content
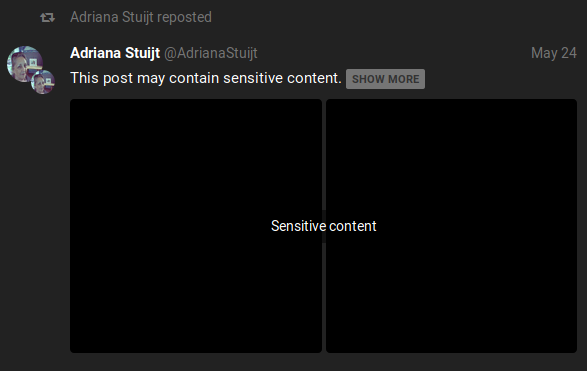
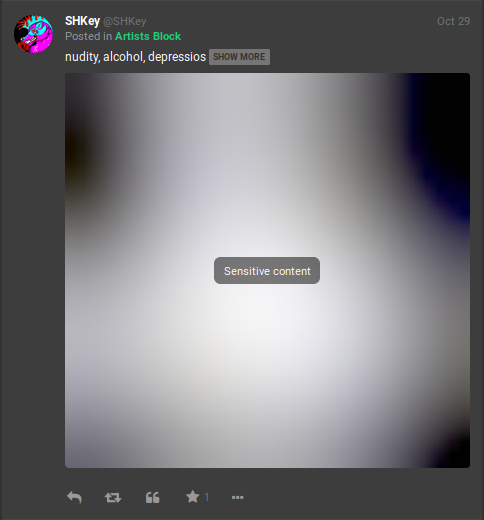
Like hidden text, Gabs may content sensitive content which is hidden by default. This sensitive content may apply to texts and media, with each having their own method for viewing. For text-based sensitive content, users must click "SHOW MORE" in the same manner as hidden text. Media-based sensitive content will have “Sensitive Content” across the media and users must click on this text to view the media. Our above example displays the following images when "Sensitive Content" is clicked on:
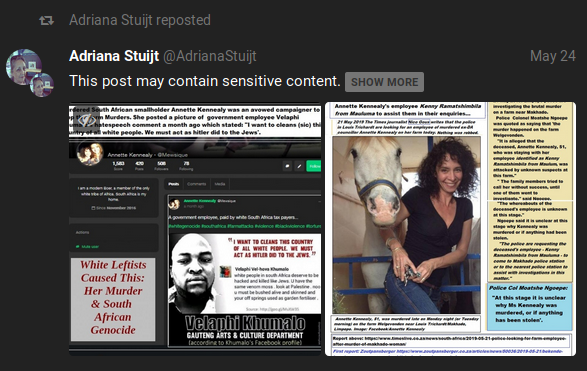
If necessary, clicking on the eye icon on the top left of the photos will re-hide the media.
Gabs: Posted In
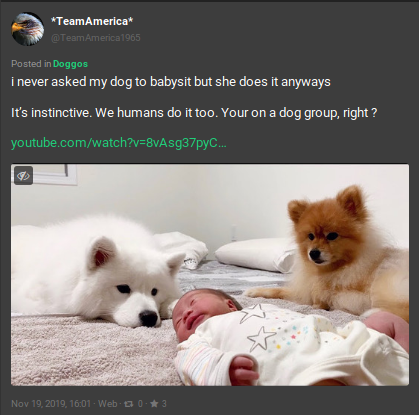
Gabs which are posted within a group will have an additional line of text indicating so above the post. This will appear as “Posted in” and then the group name which will act as a direct link into the group when clicked. On its own this line only provides you a method of quickly finding the groups in which a user might frequently post in and assists in getting a read of the target’s pattern of life based on their interests via group affiliation. Not groundbreaking, although it can lead you into the next area to exploit: groups. Our above example is a Gab which was posted into the group title Doggos which is, you guessed it, all about dogs.
Groups
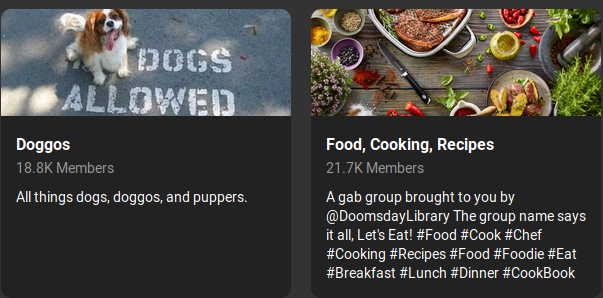
Gab also allows users to join and post within groups. Groups offer additional information to exploit, especially in regards to a target’s overall interests. Groups on Gab are fairly open and contain a number of exploitable points such as: a header, the group name, a description, posts (gabs and replies), and a member list. Since we have already covered exploiting header photos and gabs above we will not be revisiting them here as they function in the same manner. I do not discover a current way to search groups natively on Gab, however the following Google dork may help: site:https://gab.com/groups/ along with your keywords of choice. You can also view featured groups on Gab by navigating to: https://gab.com/groups.
Groups: Group Name

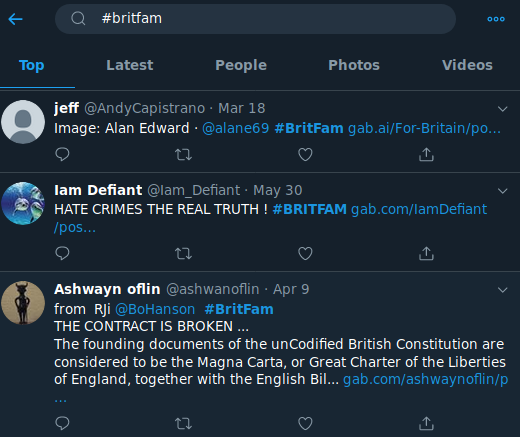
The group name is the group equivalent of the user account’s display name and will appear on the top-left side of the group page in a larger font size and in bold. This name should give an idea about what the group is about and sometimes contains information which can be used to find the same group or its members on different social media sites. Looking at the particular group above, it is worth pointing out that they added a hashtag to the group name. This made it very easy to find users on Twitter who were related to the Gab group by searching for this hashtag.
Groups: Description
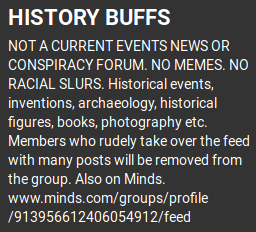
A group’s description is similar in function to the biography section of a user’s profile and will appear directly below the group name. The group description contains text which gives further information regarding the group and its content. This section may also contain valuable information in the form of common group hashtags, possible admin or moderator usernames, and links to the group on other platforms. Our above example is mostly made up of rules and basic information on the group. However, they also included a link to the group operating on Minds which gives us an additional resource to exploit.
Groups: Members
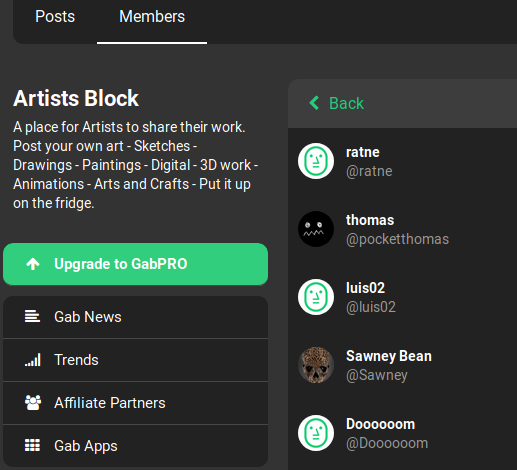
Members of a group can be viewed by clicking on the “Members” tab on the top left side of the group’s page. This view will allow an investigator to view all members within a group and clicking on their usernames will open up the user’s profile. Unfortunately, it does not appear that they are sorted in any useful manner. This might assist with confirming in a user is a member of a group, however it is very difficult to sort through large member lists.
Conclusion
After reading this guide you should now be ready to dive into your next Gab investigation with plenty of tools and know-how to ensure you don’t miss any relevant information. If you are more of a visual learner I have also created a Gab OSINT Exploitation Flow chart which you can find on my Github, along with some basic javascript bookmarklets to help you quickly exploit Gab targets. As always, feel free to reach out to me on Twitter if you need any assistance.


